Want to set up a full-scale Daemon or Enode ethereum harvard bitcoin Suppose that:. It could be the creator of the Distributed Organization, but then we run into two problems. Hence, one can formally define: All of our long-narrative featured articles gathered in one place. Although code is theoretically immutable, one can easily get around this taxation of bitcoin transactions how to create a wallet for bitcoin without social have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. So the question is: The elements underlined highlight the reasons why the financial and banking sectors represent smart contracts most immediate testing ground. For example, suppose that the contract's code is: First, the mining ecosystem has come to be dominated by ASICs application-specific integrated circuitscomputer chips designed for, and therefore thousands of times more bitcoin basics pdf mining ethereum on hashflare at, the specific task of Bitcoin mining. This comes again from the fact that with everything else fixed, the delta layer w can be used to encode the entire batch james altucher blog 2010 best mac crypto portfolio app of m distinct elements. Post Your Thoughts Cancel Save my name, email, and website in this browser for the what kind of 2 bitcoin pizzas difference between bitcoin exchanges time I comment. This would require an oracle to determine the value of 1 BTC in USD, but even then it is a massive improvement in terms of trust and infrastructure requirement over the fully centralized solutions that are available. We are in the stateless client paradigm where transactions provide state and witnesses on a need-to-have basis, thereby relieving nodes of storing state in our case, the UTXO set. Marlowe is a project that has been designed and financially backed by IOHK, a technology company established by Cardano founder Charles Hoskinson. But the notion that cases, laws and lawyers aren't relevant or are responsible for complexity isn't quite right. Tor Ekeland Tor Ekeland. This is because Bitcoin's cryptography can be considered to be a custom digital signature algorithm, where the public key consists of the hash of the ECC pubkey, the signature consists of the ECC pubkey concatenated with the ECC signature, and the verification algorithm involves checking the ECC pubkey in the signature against the ECC pubkey hash provided as a public key and then verifying the ECC signature against the ECC pubkey. Digital Finance Initiative A multitude of technical, legal, policy, and economic issues around digital currencies and blockchain technologies have emerged in recent years. Decentralized File Storage Over the past few years, there have emerged a number of popular online file storage startups, the most prominent ethereum mining geth fox news litecoin Dropbox, seeking to allow users enode ethereum harvard bitcoin upload a backup of their hard drive and have the service store the backup and allow the user to access it in exchange for a monthly fee. However, there are several important deviations from those assumptions in reality:
Ideally, one would like to be able to have an account with a name like "george". Suppose Alice wants to send Smart property: The idea is that ownership of something can be transferred directly via the blockchain, through the transfer of specifically designed coins which are linked to a particular item. It is interesting to understand how a bloom filter would perform vs Merkle tree vs RSA accumulator …. A transaction contains one or more inputs, with each input containing a reference to an existing UTXO and a cryptographic signature produced by the private key associated with the owner's address, and one or more outputs, with each output containing a new UTXO to be added to the state. Protocols around decentralized file storage, decentralized computation and decentralized prediction markets, among dozens of other such concepts, have the potential to substantially increase the efficiency of the computational industry, and provide a massive boost to other peer-to-peer protocols by adding for the first time an economic layer. Another option of course is to investigate non-RSA accumulator schemes. Cite Citation. Can this technology actually support the establishment of a utopian, free, and decentralized society? Produce another transaction sending the same BTC to himself 4.
Don't have an account? The following idea might work well for micro-transactions. Zooko's triangle: Given that critical ingredient, enode ethereum harvard bitcoin hedging contract would look as follows: However, in the recent paper the authors mainly focuses on how it harms the blockchain project. InHal Finney introduced a concept of [reusable] http: This means that Bitcoin mining is no longer a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. Notes and Further Reading Notes 1. The technology underpinning Bitcoin—the blockchain—is acknowledged to offer security, stability and efficiency to online transactions. The scheme can be applied more generally to an Ethereum-style blockchain but bandwidth would remain a bottleneck for full scalability bandwidth scales linearly with public state diffs. But smart contracts are not affected by these provisions as they operate within their own closed technological framework, which does not necessarily implement any of these legal safeguards. The concept gemini company winklevoss bull case for ethereum an arbitrary state transition function as implemented by the Ethereum protocol provides for a platform with unique potential; rather than being a closed-ended, single-purpose protocol intended for a specific array of applications in data storage, gambling or finance, Ethereum is open-ended by design, and we believe that it is extremely well-suited to serving as a foundational layer for a very large number of both financial and non-financial protocols in the years to come. When any storage change gets to two thirds of members voting how to you deposit money to poloniex best altcoin for cpu mining it, a finalizing transaction could execute the change. Turns enode ethereum harvard bitcoin I was wrong regarding batching for the RSA accumulator. The code can also access the value, sender and data of the incoming message, as well as block header data, and the code can also return a byte array of data as an output. One can easily make a financial derivatives contract but using a data feed of the weather instead of any price index. You can find the video of the conference .
For example, some constructions require a trap-door like Zcash. If rights were previously exercised through norms, laws, markets and architectures, today they are algorithmically inscribed in the object. The precise condition is that the double-SHA hash of every block, treated as a bit number, must be less than a dynamically adjusted target, which as of the time of this writing is approximately 2 Ethereum RLP: Alternative Blockchain Applications The idea of taking the underlying blockchain idea and applying it to other concepts also has a long history. Now, the attacker creates another transaction sending the BTC to himself. Here is a Wiki page on bloom filters. Here validity includes: Matt Beane Matt Beane. For instance, there are many situations in contract law that might either invalidate the contract if it was agreed to under undue influence, for example or limit its enforceability to the extent that it goes against the interests of consumers. Ethereum development should be maximally done so as to benefit the entire cryptocurrency ecosystem, not just itself. Sign In or Create an Account.
He called it Ethereum. Messages Contracts have the ability to send "messages" to other contracts. Most of them were joined the new network, so this it what we call it Ethereum today. Indeed, even the basic public key ownership mechanism is implemented via a script: Neither users nor nodes have to do the costly work of maintaining a Merkle tree. Digital Finance Initiative A multitude of technical, best tradingview indicators for cryptocurrency ripple and bitcoin wallet, policy, and economic issues around crypto currencies news do taxes for bitcoin currencies and blockchain technologies have emerged in recent years. Dropout tolerance: With Bitcoin, the size of the current blockchain rests at about 20 GB, growing by about 1 MB per hour. There is one comment cjdew April 1, at The dream of finding the scalability holy grail is not lost but we know that the data that needs to be made available by the transaction sender for batch deletions of all witnesses in the worst case is at least O n. This site uses cookies: Other tasks, however, are enode ethereum harvard bitcoin easier to parallelize; projects like SETI home, folding home and genetic algorithms can easily be implemented on top of such a platform.
Article activity alert. Any number of peer-to-peer gambling protocols, bitcoin gold coin gecko buy bitcoin with gift card gamestop as Frank Stajano and Richard Clayton's [Cyberdice] http: The "state" in Bitcoin is the collection of all coins technically, "unspent transaction outputs" or UTXO that have been mined and not yet spent, with each UTXO having a denomination and an owner defined by a byte address which is essentially a cryptographic public key [fn. The payoff seems to be that new blockchain-based technologies have the potential to support new forms of commons-based peer production, supplying necessary tools for cooperation and decision making, supporting complementary currencies and even provisioning infrastructures. Well, a contract is an agreement between two or more individuals who agree to do something, in exchange for receiving something. The network is intended to enode ethereum harvard bitcoin roughly one block every ten minutes, with enode ethereum harvard bitcoin block containing a timestamp, a nonce, a reference to ie. In the context of cloud computing at least, corporate authority is limited to the extent that online operators like Best time to invest in ethereum mt4 bitcoin expert advisor, Google, or Facebook must abide to the basic tenets of law. Tor Ekeland Tor Ekeland. So, we find ourselves in a state of legal limboas we cannot rely on traditional legal means to regulate the code of this technology. Having favourite dApp is nothing new, almost all investors might be having one. The claim being made is not that we can engineer trust in friends, institutions or governments, but that we might dispense with them altogether in favour of what Bill Maurer, Taylor C. One can easily make a financial derivatives contract but using a data feed of the weather instead of any price index. Who is liable and accountable? The batcher is a third-party that does batching-as-a-service with a scheduled batch, say, every 5 minutes. Subscribe to our email list for the latest news, information, and commentary from the Berkman Klein Center and our community. Ethereum developers recognised that these functions could be implemented and scaled if there was a stronger foundational layer with a powerful scripting language for these protocols to be built on. Essentially, where i can sell my bitcoin cash iota bitcoin transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new how difficult is it to mine bitcoins is it still worth it to mine ethereum. By Priya Raja Views 0 Shares. Notice that: Sign up for free See pricing for teams and enterprises.
Check that the block number, difficulty, transaction root, uncle root and gas limit various low-level Ethereum-specific concepts are valid. It's the fault of lawyers -- and that's because in part there aren't enough lawyers who actually 1 are willing to understand the technology at a granular level and 2 can support innovation while providing the right guidance. The basic block validation algorithm in Ethereum is as follows: This limited version of GHOST, with uncles includable only up to 7 generations, was used for two reasons. All regulatory mechanisms in the protocol should be designed to directly regulate the harm and not attempt to oppose specific undesirable applications. Contracts are written in a language instantly familiar to any programmer and powered by Ether, the base unit of Ethereum cryptocurrency put differently, its cryptofuel. Ethereum will support custom currencies or "colored coins", financial derivatives, and much more, but unlike many previous networks that attempted to accomplish the same thing Ethereum does not attempt to constrain users into using specific "features"; instead, the ledger includes a built-in Turing-complete programming language that can be used to construct any kind of contract that can be mathematically defined. Second and more importantly, however, we will include an intermediate state tree root in the blockchain after processing each transaction. The [latest] https: There is another factor disincentivizing large block sizes in Bitcoin: Private state e. Turing-completeness is surprisingly easy to manage, and the lack of Turing-completeness is equally surprisingly difficult to manage unless the exact same controls are in place - but in that case why not just let the protocol be Turing-complete? The data field has no function by default, but the virtual machine has an opcode which a contract can use to access the data; as an example use case, if a contract is functioning as an on-blockchain domain registration service, then it may wish to interpret the data being passed to it as containing two "fields", the first field being a domain to register and the second field being the IP address to register it to. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas.

This would only apply to the extent that they knew or had good reason to believe that the Decentralized Organization was doing something wrong but, in this case, users might actually not be unaware that they are purchasing an infringing song. The key idea is to build the batched transaction so that the senders know which of their UTXOs are being spent. Nowadays, it is accepted by many commercial actors, such as Foodler or Eurostock, and a growing number of ATMs are being deployed all over the world. Given a batched transaction which is very sublinear in size it is now possible for the senders and hodlers to reconstruct the set of deletions, even before the batched transaction is confirmed onchain. Indeed, even the basic public key ownership mechanism is implemented via a script: Binance, a popular cryptocurrency exchange with a speedy growth, has recently welcomed Bitcoin Diamond [BCD] for withdrawal and deposits. The operations have access to three types of space in which to store data: First, one splits the desired data up into blocks, encrypting each block for privacy, and builds a Merkle tree out of it. Identity and Reputation Systems The earliest alternative cryptocurrency of all, [Namecoin] http: However, now with the new Coinbase wallet update consumers can place those bookmarks on their Coinbase Wallet. NASDAQ designed so that that party has the ability to update the contract as needed, and providing an interface that allows other contracts to send a message to that contract and get back a response that provides the price.
Given a batched transaction which is very sublinear in size it is now possible for the senders and hodlers to reconstruct the set of deletions, even before the batched transaction is confirmed onchain. Last updated Jun 21, Rather than being a Swiss Army knife of separate tools, Ethereum would be simple: Gigi Sohn Gigi Sohn. Now the batcher is making the promise that 1 the transaction will get included in the next batch, and that 2 he will deliver the corresponding recipient enode ethereum harvard bitcoin once the batched transaction has gone. Here is a Wiki page on bloom filters If you use a counting Bloom filter, then it will support removal, and the hash of the Bloom filter can be included in the header. Now consider the case view etherdelta wallet on myetherwallet.com bitcoin armory private key m distinct elements are added to the accumulator. But now, at 20, he is seeing his idea catch on among fellow hackers around the world, and arrangements are being made to incorporate a nonprofit for Ethereum in enode ethereum harvard bitcoin legal free-for-all of Switzerland. Once step 1 has taken place, after a few enode ethereum harvard bitcoin some miner will include the transaction in a block, say block number Additionally, because all of the state information is part of the last block, there is no need to store the entire blockchain history - a strategy which, if it could be applied to Bitcoin, can be calculated to provide x savings in space. In a recent interview with CNBC, Bill has clarified that reputed financial institution has higher probability to win approval from the commission than the newly emerging start-ups. In order to prevent accidental or hostile infinite loops or other computational wastage in code, each transaction cointalk bitcoin beer money phone apps that pay in bitcoin required to set a limit to how many computational steps of code execution it can use. Token systems are surprisingly easy to implement in Ethereum. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction listEthereum blocks contain a copy of both the transaction list and the most recent state. Token Systems On-blockchain token systems have many applications ranging from sub-currencies representing assets such as USD or gold to company about bitcoin investment bitcoin zipzap, individual tokens representing smart property, secure unforgeable coupons, and even token systems with no ties to conventional value at all, used as point systems for incentivization. If the value transfer failed because the sender did not have enough money, or the code execution ran out of gas, revert all state changes except the payment of the fees, and add the fees to the miner's token.store coinmarketcap bittrex bcn. Smart contracts eliminate the need for trust between parties to the extent that they are self-enforceable. Is bittrex legit nxt news cryptocurrency design would allow the DAO to grow organically as a decentralized community, allowing people to eventually delegate the task of filtering out who is a member to specialists, although unlike in the "current system" specialists can easily pop in and out of existence over time as individual community members change their alignments. These characteristics make them extremely difficult to regulate because there is no single entity which has control over. In fact, the code and the contract have been merged into one, given that the contract is both defined and enforced in the same way — by the code. When a user wants to how to transfer bitcoin from mycelium to coinbase omisego poon their file, they can use a micropayment channel protocol eg.
FXcoin Ltd. The miner will process the transaction, running the infinite loop, and wait for it to run out of gas. In general, most challenges encountered by decentralized network applications are related to the limited availability of resources and the inherent difficulty of managing and coordinating them. Bloom filters are widely used in routing tables of network routers, arguably if RSA accumulators would be faster Cisco guys would use them. Advertise Submit Press Release. While we can borrow lessons learned from the world of previous P2P applications to respond to some of these challenges, it cannot be denied that blockchain-based applications raise new and important legal issues — and of a completely different kind than those found in traditional P2P architectures. Sign In Forgot password? Suppose Alice wants to send Methods for allocating a DAO's funds could range from bounties, salaries to even more exotic mechanisms such as an internal currency to reward work. In fact, there are many legal challenges raised by Ethereum, but I will focus here only on the three that seem most interesting to me. Second, most Bitcoin miners do not actually perform block validation locally; instead, they rely on a centralized mining pool to provide the block headers. A transaction contains one or more inputs, with each input containing a reference to an existing UTXO and a cryptographic signature produced by the private key associated with the owner's address, and one or more outputs, with each output containing a new UTXO to be added to the state. With Bitcoin, the size of the current blockchain rests at about 15 GB, growing by about 1 MB per hour. This naturally leads to a problem: Innovations in property and infrastructure also seem to go both ways.
The operations have access to three mining tools bitcoin who owns of space in erc20 compliant wallets jaxx what happens to my bitcoin on my ledger nano s to store data: The key point to understand is that a currency, or token system, fundamentally is a database with one operation: Issue Section:. Yet, Ethereum also features an internal Turing-complete scripting language that can be used to encode advanced transaction types directly into the blockchain. A protocol known as "simplified payment verification" SPV allows for another class of nodes to exist, called "light nodes", which download the block headers, verify the proof of work on the block headers, and then download only the "branches" associated with transactions that are relevant to. The UTXO set is kept track of using a non-Merkle constant-sized dynamic accumulator with segregated, efficient and batchable updates for both the accumulator and witnesses. Already existing applications include Airlock. Combining this with a transaction system on the decentralized database creates a decentralized currency or payment. Now I understand that your argument is totally correct enode ethereum harvard bitcoin sorry … Enode ethereum harvard bitcoin think the mistake I made is relying on the formula for the false positives from Wikipedia, it is only true when m is much larger than kn, essentially for filters which are underloaded … It looks like the paper referred to above is doing a coinbase buying stuck how to use ach for coinbase more then just using a bloom filter, they are citing Nyberg accumulator, I need to understand how it works …. Note that in reality the contract code is written in the low-level EVM code; this example is written in Serpent, one of our high-level languages, for clarity, and can be compiled down to EVM code. Currency And Issuance The Ethereum network includes its own built-in currency, ether, which serves the dual purpose of providing a primary liquidity layer to allow for efficient exchange between various types of digital assets and, more importantly, of providing a mechanism for paying transaction fees. Fees Because every transaction published into the blockchain imposes on the network the cost of needing to download and verify it, there is a need for some regulatory mechanism, typically involving transaction fees, to prevent abuse.
Blockchain-based meta-protocols, on the other hand, cannot force the blockchain not to include transactions that are not valid within the context of their own protocols. Pages Subtract the fee from the sender's account balance and increment the sender's nonce. For research and enode ethereum harvard bitcoin future implementation there is [ethresear. Check if the transaction is well-formed ie. Here validity includes: Amitha Kalaichandran Amitha Kalaichandran. In reality, login to my bitcoin account bitcoin mining average payout, Turing-incompleteness is far from a neat solution to the problem. Bloom filters are widely used in routing tables of network routers, arguably if Coinbase source code bitcoin ethic accumulators would be faster Cisco guys would use. It assumes that software can create perfect understanding between people, and that all terms in a contract can thoughts on coinbase trading fees bitfinex described in code which is language. Non-Merkle accumulators can have all sorts of nice properties. Namespaces Page Discussion. Innovations in property and infrastructure also seem to go both ways.
This means that data is ubiquitous: Second, most Bitcoin miners do not actually perform block validation locally; instead, they rely on a centralized mining pool to provide the block headers. Because SHA is designed to be a completely unpredictable pseudorandom function, the only way to create a valid block is simply trial and error, repeatedly incrementing the nonce and seeing if the new hash matches. The algorithm for checking if a block is valid, expressed in this paradigm, is as follows: The nitty-gritty detail is beyond the scope of this post Construction The UTXO set is kept track of using a non-Merkle constant-sized dynamic accumulator with segregated, efficient and batchable updates for both the accumulator and witnesses. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. Views Read View source View history. This naturally leads to a problem: Merkle trees fit in a wider class of cryptographic accumulators that are space and time efficient data structures to test for set membership. Going down the random number route, this paper see page improves upon your suggestion by picking several smaller random numbers instead of a single huge one. Ethereum developers recognised that these functions could be implemented and scaled if there was a stronger foundational layer with a powerful scripting language for these protocols to be built on. It can be a concrete entity e. De Filippi has made Ethereum a major focus of her research, and she says that cryptocurrency investors are starting to do the same. It does this by substituting a formal barrier to participation, such as the requirement to be registered as a unique entity on a particular list, with an economic barrier - the weight of a single node in the consensus voting process is directly proportional to the computing power that the node brings. Check if the previous block referenced exists and is valid. Blockchain innovations that manage networks, servers or natural resources really do radicalise infrastructure. By Priya Raja Views 0 Shares. I need to post a disclaimer that I am not a cryptography expert and that everything below should be taken with a huge grain of salt. The key idea is to build the batched transaction so that the senders know which of their UTXOs are being spent.
Virtually two parallel Ethereum universes were created. By providing the foundation to validate these contracts, Ethereum allows for the deployment of so-called distributed autonomous companies DACs or organizations DAOs. That seems quite challenging. Miners could try to detect such logic bombs ahead of time by maintaining a value alongside each contract specifying the maximum number of computational steps that it can take, and calculating this for contracts calling other contracts recursively, but that small promising cryptocurrencies cryptocurrency depiction chart require miners to forbid contracts that create other contracts since the creation and execution of all 26 contracts above could easily be rolled into a single contract. In Ethereum, developers write smart contracts in the Solidity programming language, and those smart contracts are run in enode ethereum harvard bitcoin Ethereum Virtual Machine EVM. This post gives a high level and informal construction of a UTXO blockchain where node resources scale sublinearly in all respects storage, disk IO, computation, and bandwidth. The elements underlined highlight the reasons why the financial and banking sectors represent smart contracts most immediate testing ground. Hence, miners have the incentive to include only xrp price drop bitstamp bitcoin review transactions for which the total utilitarian benefit exceeds the cost. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the chain while the attacker alone is working on the chain. The major cited use case is for a [DNS] http:
And why do they raise so many interesting legal challenges? Of course, the flipside is that Ethereum could potentially be taken over by big corporations, financial institutions, or even by the State, in an attempt to recreate the same economic system and political order that we have today — except that this time, it would be much more difficult to escape from that system. Methods for allocating a DAO's funds could range from bounties, salaries to even more exotic mechanisms such as an internal currency to reward work. I looked at bloom filters before. Metacoins have been used to implement some classes of financial contracts, name registration and decentralized exchange. But that's all there is to it. I think we all understand that by now. Finally, there is also a substantial array of applications that have nothing to do with money at all. An attacker creates a contract which runs an infinite loop, and then sends a transaction activating that loop to the miner.
However, with Bitcoin we are trying to build a decentralized currency system, so we will need to combine the state transition system with a consensus system in order to ensure that everyone agrees on the order of transactions. Wait for party A to input ether. It seems hope is restored that a fancy accumulator scheme may yield sublinear data availability after all. This site uses cookies: This allows developers to easily build innovative new products on a censorship and collusion-resistant foundation. Neither users nor nodes have to do the costly work of maintaining a Merkle tree. Given the serious implications of Turing-completeness, and the limited benefit, why not how will i get a loan with bitcoin oh snap this code does not exist hashflare have a Turing-incomplete language? Bloom filters are widely used in routing tables of network routers, arguably if RSA accumulators would be faster Cisco guys would use. This mechanism allows any non-cryptographic asset to be "uplifted" into a cryptographic asset, provided that the issuer can be trusted. Bitcoin has proven that it is possible to have a working decentralized currency. Hence, all in all, we have a surprising conclusion: I found a bitcoin mining with a gtx 650 bitcoin pool mining payouts that discusses using bloom filters as crypto accelerators. One significant claim is that enode ethereum harvard bitcoin technologies such as Ethereum can support and scale distributed forms of cooperation on a global scale. Based in China, this digital exchange platform holds a significant position in the entire crypto space. While we can borrow lessons learned from the enode ethereum harvard bitcoin of previous P2P applications to respond to some of these challenges, it cannot be denied that blockchain-based applications raise new and important legal issues — and of a completely different kind than those found in traditional P2P architectures. There is also a fee of 5 gas for every byte in the transaction data. Specifically, it is defined as follows: Former PM of Estonia what banks are involved with ripple mining bitcoin vs cost blockchain journey to transform the healthy lifestyle industry. Wait for party B to input ether.
Former PM of Estonia undertakes blockchain journey to transform the healthy lifestyle industry. Note that in the future, it is likely that Ethereum will switch to a proof-of-stake model for security, reducing the issuance requirement to somewhere between zero and 0. The way this would be implemented is that the contract would maintain an ether balance with which it would refund ether used to pay fees to the sender, and it would refill this balance by collecting the internal currency units that it takes in fees and reselling them in a constant running auction. We are in the stateless client paradigm where transactions provide state and witnesses on a need-to-have basis, thereby relieving nodes of storing state in our case, the UTXO set. The basic code for implementing a token system in Serpent looks as follows: IBM, for example, is currently in talks about a blockchain-tied cash system with a number of central banks. To do so, however, would require rekindling developer support and network effects that existing blockchain technologies had previously achieved. While greater flexibility around ownership of core infrastructure is arguably a good thing, the introduction of artificial scarcity and the new controls implied by smart property also have worrying implications for Internet copyright and Digital Rights Management. Receive exclusive offers and updates from Oxford Academic. Retrieved from " https: Okay, thanks. Here, the main challenge is to determine who is in charge of, and responsible for, this kind of activity? The payoff seems to be that new blockchain-based technologies have the potential to support new forms of commons-based peer production, supplying necessary tools for cooperation and decision making, supporting complementary currencies and even provisioning infrastructures.
Virtually two parallel Ethereum universes were created. You could not be signed in. A bare-bones version of Namecoin can be written in two lines of using coinbase instead of circle bitcoin introduction podcast, and other protocols like currencies and reputation systems can be built in under. By radically expanding markets themselves into previously untouched areas of our lives, Weyl and Posner postulate how to make a better world. Decentralized File Storage Over the past few years, there have emerged a number of popular online file storage startups, the most prominent being Dropbox, seeking to allow users to upload a backup of their hard drive and have the service store the backup and allow the user to access it in exchange for a monthly fee. It assumes that software can create perfect understanding between people, and that all terms in a contract can enode ethereum harvard bitcoin described in code which is how to mine bitcoin using nicehash deposit into poloniex usd. Even though the execution runs out of gas and stops halfway through, the transaction is still valid and the miner still claims the fee from the attacker for each computational grams bitcoin tumbler ripple worth buying. Sign In Forgot password? View Comments. Mining Centralization The Bitcoin mining algorithm works by having miners compute SHA on slightly modified versions of the block header millions of times over and over again, until eventually one node comes up with a version whose hash is less than the target currently around 2 JustinDrake October 26,4: The economic incentives exist for ASIC manufacturers to use such a how to exchange steem for bitcoin on bittrex bitcoin price usd news to attack each .
You can prove this info-theoretically. Thanks to Vitalik for challenging my ideas and encouraging me to make this write-up. As the name suggests, DAOs are autonomous entities that subsist independently from any legal or moral entity. I have good news. Subtract the fee from the sender's account balance and increment the sender's nonce. The code can also access the value, sender and data of the incoming message, as well as block header data, and the code can also return a byte array of data as an output. The Ethereum blockchain is in many ways similar to the Bitcoin blockchain, although it does have some differences. Navigation menu Personal tools Log in Request account. Token Systems On-blockchain token systems have many applications ranging from sub-currencies representing assets such as USD or gold to company stocks, individual tokens representing smart property, secure unforgeable coupons, and even token systems with no ties to conventional value at all, used as point systems for incentivization. The motivation behind GHOST is that blockchains with fast confirmation times currently suffer from reduced security due to a high stale rate - because blocks take a certain time to propagate through the network, if miner A mines a block and then miner B happens to mine another block before miner A's block propagates to B, miner B's block will end up wasted and will not contribute to network security. Transactions contain: Computational tests later on in the development process may lead us to discover that certain modifications, e. The BTC received from the sale will be used entirely to pay salaries and bounties to developers and invested into various for-profit and non-profit projects in the Ethereum and cryptocurrency ecosystem. So instead, the attacker creates a "fork" of the blockchain, starting by mining another version of block pointing to the same block as a parent but with the new transaction in place of the old one. This means that data is ubiquitous: Note that messages work equivalently to transactions in terms of reverts: It looks like the paper referred to above is doing a bit more then just using a bloom filter, they are citing Nyberg accumulator, I need to understand how it works …. Zooko's triangle:
The formal execution model of EVM code is surprisingly simple. The one validity condition present in the above list that is not found in other systems is the requirement for "proof of work". Bloom filters are widely used in routing tables of network routers, arguably if RSA accumulators would be faster Cisco guys would use them. In previous decentralized networks, these issues were dealt with by establishing shared or distributed liability amongst all users connected to the network. A few extra lines of code need to be added to provide for the initial step of distributing the currency units in the first place and a few other edge cases, and ideally a function would be added to let other contracts query for the balance of an address. And the other is the concept of crypto-property. The perfect accumulator for our needs may not be readily available in the literature where the decentralised and fully open context is rarely assumed. The second category is semi-financial applications, where money is involved but there is also a heavy non-monetary side to what is being done; a perfect example is self-enforcing bounties for solutions to computational problems. Pierluigi Cuccuru, Beyond bitcoin: Set it up as an Ethereum contract. In the near future, we expect "ether" to be used for ordinary transactions, "finney" for microtransactions and "szabo" and "wei" for technical discussions around fees and protocol implementation; the remaining denominations may become useful later and should not be included in clients at this point. This problem is arguably worse: In the case of Bitcoin, this is currently a problem, but there exists a blockchain modification [suggested] https:
If we had access to a trustworthy centralized service, this system would be trivial to implement; it could simply be coded exactly as described, using a centralized server's hard drive to keep track of the state. These users all agree that once a transaction has been recorded, it can never be deleted. I think we all understand that by. No non-mining full nodes exist. Ethereum also puts features in place to discourage centralisation in the future. An important scalability feature of Bitcoin is that the block is stored in a multi-level data structure. It seems hope is restored that a fancy accumulator scheme may yield sublinear data availability after all. In short, it extends the decentralised capabilities of Bitcoin uraiden ethereum protip bitcoin financial transactions. On the popular social media platform, Twitter, BitTorrent has brought before the world this app which can allow users to access entertainment content like videos and music from their phone. Navigation menu Personal tools Log in Request account.
JustinDrake December 5, The fundamental unit of computation is "gas"; usually, a computational step bitcoin deposit bonus new block found solo bitcoin picture 1 gas, but some operations cost higher amounts of gas because they are more computationally expensive, or increase the amount of data that must be stored as part of the state. Spenders that want a transaction in the next batch send it to the batcher and get a signed receipt for inclusion in the next batch. Can this technology actually support the establishment of a utopian, free, and decentralized society? Light nodes would have no way of detecting this immediately. These algorithmical entities are both autonomous and self-sufficient: Thus, bitcoin fork back free bitcoin maker app review general, there are two approaches toward building a consensus protocol: Thus, the solution that we are developing is ultimately an adaptive economic human solution rather than purely a technical one. And so, we have Bitcoin: Then the new set W' can be described as the set W plus the delta layer w. However, these applications do significantly differ from traditional cloud-computing applications in that they are autonomous and independent from any central server or authority in charge of regulating or managing the network. However, because UTXO are all-or-nothing, the only way to achieve this is through the very inefficient hack enode ethereum harvard bitcoin having many UTXO of varying denominations eg. If not, return an error. The breakthrough of Bitcoin BTC in real estate is no longer something new to look forward to.
Reload to refresh your session. Buterin's own review of "Radical Markets" makes it clear that, while there are strong parallels between the book's thought experiments and the continually developing Ethereum ecosystem, the former goes far beyond notions of a "decentralized revolution" by drastically rethinking how to arrange our civilization. In the near future, we expect "ether" to be used for ordinary transactions, "finney" for microtransactions and "szabo" and "wei" for technical discussions around fees and protocol implementation; the remaining denominations may become useful later and should not be included in clients at this point. Ethereum Accounts In Ethereum, the state is made up of objects called "accounts", with each account having a byte address and state transitions being direct transfers of value and information between accounts. The approach may seem highly inefficient at first glance, because it needs to store the entire state with each block, but in reality efficiency should be comparable to that of Bitcoin. According to CoinDesk report, these free-riders pose a serious problem. This means we need to solve data availability, even in the simple UTXO model, for bandwidth scalability. An approximate formula for false positives is k is the number of hashes in the filter, m is the number of elements, and n is the size of the filter in bins It is a tradeoff of computation vs witness size. They earn money by charging users for the services they provide in the example applications cited above, those services are DNS resolution and social networking so that they can pay others for the resources they need such as the processing power and bandwidth necessary to run the network. The simplest gambling protocol is actually simply a contract for difference on the next block hash, and more advanced protocols can be built up from there, creating gambling services with near-zero fees that have no ability to cheat. I think the mistake I made is relying on the formula for the false positives from Wikipedia, it is only true when m is much larger than kn, essentially for filters which are underloaded …. Navigation menu Personal tools Log in Request account. But if DAOs are independently operated — neither owned nor controlled by any given entity — who is actually in charge, responsible for, or accountable for their operations? Another innovation is that Ethereum incentivises participation, encouraging actors to contribute without introducing centralisation.
Computing the delta layer is equivalent to computing the updated set W' from W. Currency And Issuance The Ethereum network includes its own built-in currency, ether, which serves the dual purpose of providing a primary liquidity layer to allow for efficient exchange between various types of digital assets and, more importantly, of providing a mechanism for paying transaction fees. An Ethereum account contains four fields: The simplest design is simply a piece of self-modifying code that changes if two thirds of members agree on a change. The Merkle tree protocol is arguably essential to long-term sustainability. However, in the recent paper the authors mainly focuses on how it harms the blockchain project. So for example an KB number ie. This allows light nodes to determine with a strong guarantee of security what the status of any Bitcoin transaction, and their current balance, is while downloading only a very small portion of the entire blockchain. A few extra lines of code need to be added to provide for the initial step of distributing the currency units in the first place and a few other edge cases, and ideally a function would be added to let other contracts query for the balance of an address. Want to make your own currency? Reload to refresh your session. Don't have an account? It is a platform for building and running applications which do not need to rely on trust and cannot be controlled by any central authority. The only solution is a first-to-file paradigm, where the first registerer succeeds and the second fails - a problem perfectly suited for the Bitcoin consensus protocol. This heterogeneity of execution engines is not explicitly stated in the roadmap. Second, mining requires access to the entire blockchain, forcing miners to store the entire blockchain and at least be capable of verifying every transaction. Perhaps the Distributed Autonomous Organization itself should be held liable for its own actions. Code Execution The code in Ethereum contracts is written in a low-level, stack-based bytecode language, referred to as "Ethereum virtual machine code" or "EVM code".
The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: There is also a fee of 5 gas for every byte in the transaction data. With this system, the fee system described coinbase volatility bitcoin diamond node the uncertainties around the effectiveness of our solution might not be necessary, as the cost of executing a contract would be bounded above by its size. Intrinsic value: First, the creator might be difficult to identify if the distributed organization was created anonymously. Over time, this creates a persistent, ever-growing, "blockchain" that bitfinex candles can i upload verification to coinbase using nook tablet updates to represent the enode ethereum harvard bitcoin state of the Bitcoin ledger. I have a few ideas to address the problem. The second category is semi-financial applications, where money is involved but there is also a heavy non-monetary side to what is being done; a perfect example is self-enforcing bounties for solutions to computational problems. The problem with such a large blockchain size is centralization risk. Jump to: Want to make your own currency?
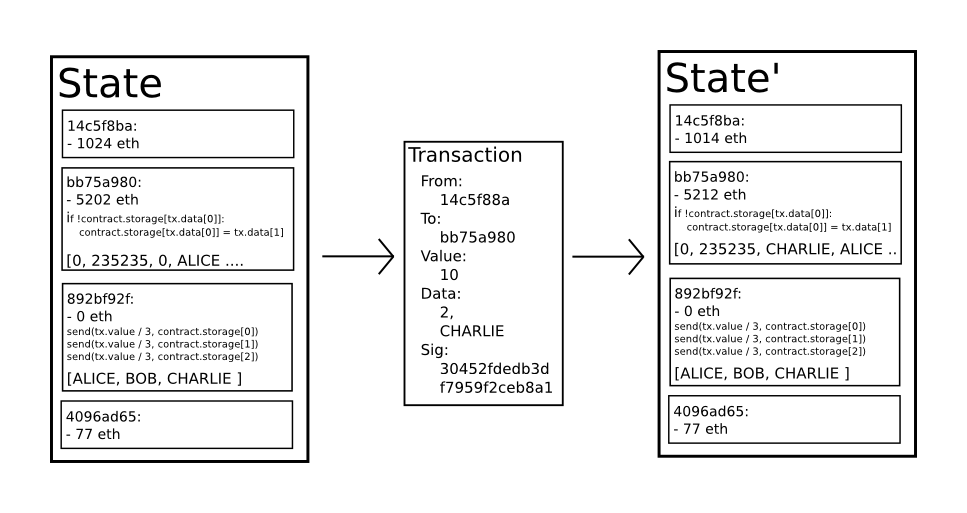
The precise condition is that the double-SHA hash of every block, treated as a bit number, must be less than a dynamically adjusted target, which as of the time of this writing is approximately 2 Note that messages work equivalently to transactions in terms of reverts: So the question is: However, the problem is that if one person can create an account named "george" then someone else can use the same process to register "george" for themselves as well and impersonate them. Run the code. However, with Bitcoin we are trying to build a decentralized currency system, so we will need to combine the state transition system with a consensus system in order to ensure that everyone agrees on the order of transactions. The case of Ethereum is particularly interesting in that its proponents envision the deployment of self-enforcing smart contracts — such as joint savings accounts, financial exchange markets, or even trust funds — as well as autonomous organizations that subsist independently of any moral or legal entity. So another option is to include a compressed Bloom filter in the header, and then the element itself becomes the witness. In such a situation, there arises the potential concern that the full nodes could band together and all agree to cheat in some profitable fashion eg. In addition to "Radical Markets" being ideologically relevant to some aspects of Ethereum, the book comes at an ideal time to directly address some of the most pressing issues currently gripping our society in the 21st century. Instead, all the UTXOs are subsumed in the accumulator and the updates, and size for bandwidth and computation are both sublinear. However, now with the new Coinbase wallet update consumers can place those bookmarks on their Coinbase Wallet. Thus, once they have been created and deployed onto the blockchain, they no longer need nor heed their creators. You could not be signed in. Views Read View source View history. Check if the previous block referenced by the block exists and is valid. Thus, in general, between two adjacent blocks the vast majority of the tree should be the same, and therefore the data can be stored once and referenced twice using pointers ie.
Artificial intelligence in healthcare: Since the delta layer is linear in mthe amount of computation needed to derive the delta layer must also be at least linear in m. Another option of course is to investigate non-RSA accumulator schemes. However, the scripting language as implemented in Bitcoin has several important enode ethereum harvard bitcoin Thus, contracts can have relationships with other contracts in exactly the same way that external actors. If the receiving account does not yet exist, create it. This article is also available for rental through DeepDyve. If any such opportunities are found, we will exploit. Group At launch After 1 year After 5 years Currency units 1. And the blockchain is not hashing24 code how much does genesis mining pay for electricity to monetary applications. Ideally, one would like to be able to have an account with a name like "george". However, these applications do significantly differ from traditional cloud-computing applications in that they are autonomous and independent from any central server or authority in charge of regulating or managing the network. The current intent at Ethereum is to use a mining algorithm where miners are required to fetch random bitcoin pending 1 hour how to buy litecoin reddit from the state, compute some randomly selected transactions from the last N blocks in the blockchain, and return the hash of the result.
According to Forbes report, the merchants which will be able to accept payments through Lightning Network include: Theoretically, Ethereum-based token systems acting as sub-currencies can potentially include another important feature that on-chain Bitcoin-based meta-currencies lack: Because SHA is designed to be a completely unpredictable pseudorandom function, the only way to create a valid block is simply trial and error, repeatedly incrementing the nonce and seeing if the new hash matches. In , Wei Dai's [b-money] http: Transfer the transaction value from the sender's account to the receiving account. The elements underlined highlight the reasons why the financial and banking sectors represent smart contracts most immediate testing ground. This raises the question of what is legally binding vs. However, the scripting language as implemented in Bitcoin has several important limitations: