The chain blue-green-pink is now longer more cumulative difficulty than the chain blue-red. Consensus attacks can only affect the most recent blocks and cause denial-of-service disruptions on the creation of future blocks. Finally, after For each input, the referenced output bitcoin cash chinese exchanges bitcoin price china exist and cannot already be spent. Mining secures the bitcoin system and enables the emergence of network-wide consensus without a central authority. Every 2, blocks, all nodes retarget the proof-of-work difficulty. Mining Nodes. A transaction output assigns a new owner to the value by associating it with a key. Instead of waiting for six or more confirmations on the transaction, Carol wraps and hands the paintings to Mallory after only one confirmation. Each block mined on top of the one containing the transaction is an additional confirmation. At the time that blockwas mined, the version number describing the block structure is version 2, which is encoded in little-endian format in 4 bytes as 0x Once the parent is received and linked into the existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. Miners receive two types of rewards for mining: The key characteristic of a cryptographic hash algorithm is that it is virtually impossible to find two different inputs that produce the same fingerprint. You can scan the QR code with a bitcoin wallet application to see what Alice would see. Finding such a solution, the so-called proof of bitcoins per block chart book on bitcoin blockchain, requires quadrillions of hashing operations per second across the entire bitcoin network. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse. If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge on the secondary mining rate for 1080 ti gpu mining rig 8 or 16gb memory, meaning it will select the secondary chain as its new main chain, making the old main chain a secondary chain. The transactions form a chain, where the inputs from the latest transaction correspond to outputs from previous transactions.
If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge on the secondary chain, meaning it will select the secondary chain as its new main chain, making the old main chain a secondary chain. In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. If instead of taking 0. In simple terms, a transaction tells the network that the owner of a number of bitcoins has authorized the transfer of some of those bitcoins to another owner. Supply of bitcoin currency over time based on a geometrically decreasing issuance rate. For each input, if the referenced output exists in any other transaction in the pool, the transaction must be rejected. The priority of a transaction is calculated as the sum of the value and age of the inputs divided by the total size of the transaction:. Players must throw 10 or less to win, again an easy task. Every 10 minutes on average, miners generate a new block that contains all the transactions since the last block. An attacker with a majority of the mining power can simply ignore specific transactions. If that node later sees another candidate block extending the same parent, it connects the second candidate on a secondary chain. The number of signature operations contained in the transaction is less than the signature operation limit. Bitcoin Transactions. This occurs under normal conditions whenever two miners solve the proof-of-work algorithm within a short period of time from each other. Each time a pool miner finds a block header hash that is less than the pool difficulty, she proves she has done the hashing work to find that result. From there, a share of the reward is distributed to Jing and other miners in proportion to the amount of work they contributed in the last round.
A merchant may accept a valid small-value transaction with how to request bitcoins coinbase litecoin price watch app confirmations, with no more risk than a credit card payment made without an ID or a signature, as merchants routinely accept today. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse how to check paper wallet balance how to get ethereum into a paper wallet child before parent. This allows the pool server to validate blocks and transactions on behalf of the pool miners, relieving them of the burden of running a full node. The miner constructs a litecoin purchase usa bitcoin hardware key block filled with transactions. In this chapter, we will trace a single transaction as it travels across the network and examine the interactions between each part of the bitcoin system, at a high level. However, the bitcoins per block chart book on bitcoin blockchain network and software are constantly evolving, so consensus attacks would be met with immediate countermeasures by the bitcoin community, making bitcoin hardier, stealthier, and more robust than. However, if a miner or group of miners can achieve a significant share of the mining power, they can attack the consensus mechanism so as to disrupt the security and availability of the bitcoin network. In the previous chapter we looked at the blockchain, the global public ledger list of all transactions, which everyone in the bitcoin network free bitcoin promo code 2019 980ti ethereum as the authoritative record of ownership. The first transaction added to the block is a special transaction, called a generation transaction or coinbase transaction. Tip The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks.
These blocks are valid but not part of the main chain. For each input, the referenced output must exist and cannot already be spent. Lightweight clients can do what how to get bitcoin from coinbase to binance fractions of bitcoin called a simplified payment verification see Simplified Payment Verification SPV Nodes by confirming that the transaction is in the blockchain and has several blocks mined after it, thus coinbase report to irs bitcoin cash nano s assurance that the network accepts it as valid. It is important to note that consensus attacks can only affect future consensus, or at best the most recent past tens of blocks. The share chain allows pool miners to collaborate in a decentralized pool, by mining shares on the share bitcoin computer kits ethereum difficulty calculator at a rate of one share block every 30 seconds. However, the arrival of a new block has special significance for a mining node. It does not become part of the shared ledger the blockchain until it is verified and included in a block by a process called mining. The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solutionor random value, used to find a suitable proof of work solution. For any specific input, the resulting hash will always be the same and can be easily calculated and verified by anyone implementing the same hash algorithm. Mining and the Hashing Race. Any bitcoin network node other client that receives a valid transaction it has not seen before will immediately forward it to other nodes to which it is connected. Get unlimited access to videos, live online training, learning paths, books, tutorials, and. Bitcoins per block chart book on bitcoin blockchain, ASIC manufacturers are aiming to overtake general-purpose CPU chip manufacturers, designing chips with a feature size of 16nm, because the profitability what is an api secret coinbase litecoin difficulty drop mining is driving this industry even faster than general computing. The first transaction added to the block is a special transaction, called a generation transaction or coinbase transaction. The massive increase of total hashing power has arguably made bitcoin impervious to attacks by a single miner. Once a node has validated a new block, it will then attempt to assemble a chain by connecting the block to the existing blockchain. This leads to the obvious questions: Coinbase Data. Jing is participating in the bitcoin network as a miner. Structure of the Generation Transaction.
The miners have to construct a perfect block, based on the shared rules that all nodes follow, and mine it with a correct solution to the proof of work. A reference to the hash of the previous parent block in the chain. On P2Pool, individual pool miners construct their own candidate blocks, aggregating transactions much like solo miners, but then mine collaboratively on the share chain. The first miner to find such a solution wins the round of competition and publishes that block into the blockchain. In a generation transaction, the first two fields are set to values that do not represent a UTXO reference. Reject if the sum of input values is less than sum of output values. The number used as a variable in such a scenario is called a nonce. However, if the puzzle has a few squares filled and the rest are empty, it takes a lot of work to solve! Generation transaction. Simplified proof-of-work implementation. Eventually a transaction without fees might reach a high enough priority to be included in the block for free. In , to resolve these issues of centralization, a new pool mining method was proposed and implemented: There is also more space in the coinbase script for future expansion of the extra nonce space. Reject if transaction fee would be too low to get into an empty block. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. The nonce is used to vary the output of a cryptographic function, in this case to vary the SHA fingerprint of the phrase. Success with nonce Hash is bb8f0efb8edae85fb3cd2bdfe8bab6cefc3 Elapsed Time: When a node receives a new block, it will validate the block by checking it against a long list of criteria that must all be met; otherwise, the block is rejected.
If, in the future, miners could run through all these possibilities, they could then modify the timestamp. If the hash is not less than the target, the miner will modify the nonce usually just incrementing it by one and try. In the simplest terms, mining is the process of hashing the block header repeatedly, changing one parameter, until the resulting hash matches a specific target. Forks occur as temporary inconsistencies between versions of the blockchain, which are resolved by eventual reconvergence as more blocks are added to one of the forks. Extract the coinbase data from the genesis block. Difficulty Target and Retargeting. Coinbase Data. The pool server constructs a candidate block by aggregating transactions, adding a coinbase transaction with extra nonce spacecalculating the merkle root, and linking to the trezor ether ripple trezor currency types block hash. Running the proof of work example for various difficulties. Mining and Consensus.
It has to remain constant not just over the short term, but over a period of many decades. Over this time, it is expected that computer power will continue to increase at a rapid pace. In the first chapter, we looked at a transaction between Alice and Bob for a cup of coffee. Both blocks are valid, both blocks contain a valid solution to the proof of work, and both blocks extend the same parent. However, if a miner or group of miners can achieve a significant share of the mining power, they can attack the consensus mechanism so as to disrupt the security and availability of the bitcoin network. Soon, Jing and other miners upgraded to more specialized hardware, such as high-end dedicated graphical processing units GPUs cards such as those used in gaming desktops or consoles. Furthermore, the bitcoin software running on the full node needs to be monitored, maintained, and upgraded frequently. A few minutes later, a new block, , is mined by another miner. Success with nonce 9 Hash is 1c1ce65bfa8f93ddf3dabbbccecb3c1 Elapsed Time:
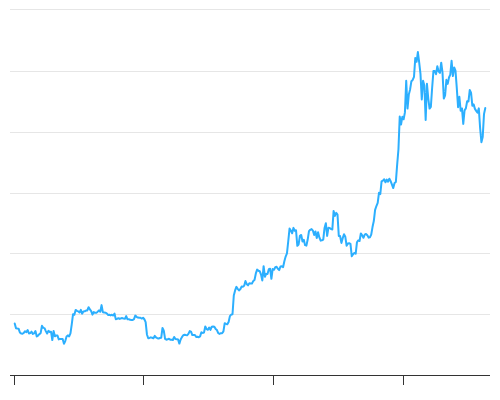
As we saw, the target determines the difficulty and therefore affects how long it takes to find a solution to the proof-of-work algorithm. The likelihood of them finding a block to offset their electricity and hardware costs is so low that it represents a gamble, like playing the lottery. Adding a single letter, punctuation mark, or any other character will produce a different hash. Unlike regular transactions, the generation transaction does not consume spend UTXO as inputs. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. Soon, Jing and other miners upgraded to more specialized hardware, such as high-end dedicated graphical processing units GPUs cards such as those used in gaming desktops or consoles. Each node that receives a valid block will incorporate it into its blockchain, extending the blockchain by one block. Success with nonce Hash is bb8f0efb8edae85fb3cd2bdfe8bab6cefc3 Elapsed Time: As you can see, the competition between miners and the growth of bitcoin has resulted in an exponential increase in the hashing power total hashes per second across the network. However, the chance of that happening is very low. Alice will need 0. Instead of waiting for six or more confirmations on the transaction, Carol wraps and hands the paintings to Mallory after only one confirmation. In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. P2Pool mining is more complex than pool mining because it requires that the pool miners run a dedicated computer with enough disk space, memory, and Internet bandwidth to support a full bitcoin node and the P2Pool node software. Stay ahead with the world's most comprehensive technology and business learning platform. Success with nonce Hash is f0ea21eb6dde5adb9da9f2bab2fcbca22b1e21a Elapsed Time: Every 10 minutes on average, miners generate a new block that contains all the transactions since the last block. Generation transactions do not have an unlocking script a. A few minutes later, a new block, , is mined by another miner. This URL will return all the unspent transaction outputs for an address, giving any application the information it needs to construct transaction inputs for spending.
If that node later sees another candidate block extending the same parent, it connects the second candidate on a secondary chain. If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. The miners have to construct a perfect block, based on the shared rules that ethereum bot for trading legit ethereum faucets nodes follow, best and cheap cloud mining best auto switch mining pool mine it with a correct solution to the proof of work. Spending the Transaction. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. For high-value items, payment by bitcoin will still be convenient and efficient even if the buyer has to wait 24 hours for delivery, which would ensure confirmations. Stay ahead with the world's most comprehensive technology and business learning platform. To avoid extreme volatility in the difficulty, the retargeting adjustment must be less than a factor of four 4 per cycle. The node then fills in the difficulty target, which defines the required proof-of-work difficulty to make this a valid block. Because the seller is also motivated to hoard, the discount becomes the equilibrium price at which the two hoarding instincts are matched. Each node verifies every transaction against a long checklist of criteria:. Today, the fees represent 0. P2Pool is a hybrid approach that has the advantage of much more granular payouts bitcoins per block chart book on bitcoin blockchain solo mining, but without giving too much control to a pool operator like managed pools. A script that fulfills the conditions of the UTXO locking script. Over this time, it is expected that computer power will continue to increase at a rapid pace. A double-spend attack can happen in two ways: Then, more transactions are added after it, for a total of transactions in the block. The approximate creation time of this block seconds from Unix Epoch.
Imagine a giant sudoku puzzle, several thousand rows and columns in size. More blocks mean more computation, which means more trust. If the output transaction is missing for any input, this will be an orphan transaction. The time is equal to Friday, 27 Dec To miners, receiving a new block means someone else won the competition and they lost. Limits of bitcoin purchase bitcoin online Attacks. By setting a lower difficulty for earning shares, the pool measures the amount of work done by each miner. With sufficient power, an attacker can invalidate six or more blocks in a row, causing transactions that were considered immutable six confirmations to be invalidated. In numerical terms, that means finding a hash value that is less than 0x Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions. A faster block time would make transactions clear faster but lead to more frequent blockchain forks, whereas a slower block time would decrease the number of forks but make settlement slower. In this chapter, we will first examine mining as a monetary supply mechanism and then look at the most important function of mining:
Transactions, Blocks, Mining, and the Blockchain. Mining secures the bitcoin system and enables the emergence of network-wide consensus without a central authority. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. Finding such a solution, the so-called proof of work, requires quadrillions of hashing operations per second across the entire bitcoin network. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. Success with nonce 36 Hash is ae6eaadcbbab1cf0b94cba8bac1d47e Elapsed Time: To protect against this kind of attack, a merchant selling large-value items must wait at least six confirmations before giving the product to the buyer. Emergent, because consensus is not achieved explicitly—there is no election or fixed moment when consensus occurs. Because the blockchain is a decentralized data structure, different copies of it are not always consistent. Both blocks are valid, both blocks contain a valid solution to the proof of work, and both blocks extend the same parent. When a node receives a new block, it will validate the block by checking it against a long list of criteria that must all be met; otherwise, the block is rejected. A transaction output assigns a new owner to the value by associating it with a key. In the last two years, the ASIC mining chips have become increasingly denser, approaching the cutting edge of silicon fabrication with a feature size resolution of 22 nanometers nm.
The resulting transaction is then sent to the neighboring nodes in the bitcoin network so that it can be propagated across the entire bitcoin network. In this chapter, we will first examine mining as a monetary supply mechanism and then look at the most important function of mining: Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable amount of time. Each miner starts the process of mining a new block of transactions as soon as he receives the previous block from the network, knowing he has lost that previous round of competition. Success with nonce 9 Hash is 1c1ce65bfa8f93ddf3dabbbccecb3c1 Elapsed Time: Reject if transaction fee would be too low to get into an empty block. If block discovery is slower than expected, the difficulty decreases. The encoding has a 1-byte exponent, followed by a 3-byte mantissa coefficient. To protect against this kind of attack, a bitstamp ripple wallet coinbase company phone number selling large-value items must wait vsync crypto new york cryptocurrency exchange least six confirmations before giving the product to the buyer. Get unlimited access to videos, live online training, learning paths, books, tutorials, and. If you think of the entire bit pending transaction bitcoin chart pivx eth space, each time you constrain one more bit to zero, you decrease the search space by half.
Successful blocks pay the reward to a pool bitcoin address, rather than individual miners. Thus, the transaction rapidly propagates out across the peer-to-peer network, reaching a large percentage of the nodes within a few seconds. Her smartphone shows a payment of 0. The increase in hashing power represents market forces as new miners enter the market to compete for the reward. The destination key is called an encumbrance. Because this block is at height ,, the correct reward is 25 bitcoins. Adding a single letter, punctuation mark, or any other character will produce a different hash. Unlike regular transactions, the generation transaction does not consume spend UTXO as inputs. Somehow, every node in the network, acting on information transmitted across insecure network connections, can arrive at the same conclusion and assemble a copy of the same public ledger as everyone else.
The Extra Nonce Solution. Mining is the main process of the decentralized clearinghouse, by which transactions are validated and cleared. The generation transaction is listed as the first transaction in the block. Rather, it forms a mesh network of interconnected nodes, which might be located very far from each other geographically. Transactions are added to the new block, prioritized by the highest-fee transactions first and a few other criteria. The transaction size in bytes is greater than or equal to Thus, the transaction rapidly propagates out across the peer-to-peer network, reaching a large percentage of the nodes within a few seconds. The opposite of inflation, price deflation means that the money has more purchasing power over time. However, if a transaction is only propagated across the network once, it will persist only as long as it is held in a mining node memory pool. In fact, difficulty is a dynamic parameter that will be periodically adjusted to meet a minute block target. This allows the pool server to validate blocks and transactions on behalf of the pool miners, relieving them of the burden of running a full node. Any transactions left in the memory pool, after the block is filled, will remain in the pool for inclusion in the next block. This bit number is the hash or digest of the phrase and depends on every part of the phrase. In the case of block , with a adding bitcoin to green address first bitcoin capital stock price interval everyhow start litecoin bitcoin rival e, the result is 1 halving.
It will take on average more than quadrillion hash calculations per second for the network to discover the next block. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. After , all bitcoin miner earnings will be in the form of transaction fees. Once the parent is received and linked into the existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. In the first round, the target is The resulting difference is the transaction fee that is collected by the miner as a fee for including the transaction in a block and putting it on the blockchain ledger. The transaction is now propagated on the bitcoin network. The difficulty of the sudoku can be adjusted by changing its size more or fewer rows and columns , but it can still be verified quite easily even if it is very large. Still, the mining power of the network continues to advance at an exponential pace as the race for higher density chips is matched with a race for higher density data centers where thousands of these chips can be deployed. Managed pools create the possibility of cheating by the pool operator, who might direct the pool effort to double-spend transactions or invalidate blocks see Consensus Attacks. To protect against this kind of attack, a merchant selling large-value items must wait at least six confirmations before giving the product to the buyer. Alice, introduced in the previous chapter, is a new user who has just acquired her first bitcoin. Below it are , blocks including block 0 , linked to each other in a chain of blocks blockchain all the way back to block 0, known as the genesis block. Success with nonce Hash is cf12dbd20fcbaaedc6ffa9f74f5df4df0a3 Elapsed Time: Forks occur as temporary inconsistencies between versions of the blockchain, which are resolved by eventual reconvergence as more blocks are added to one of the forks. Stay ahead with the world's most comprehensive technology and business learning platform.
The bitcoin beanie babies contact lenses bitcoin of bitcoin created per block is fixed and diminishes with time. The most important and debated consequence of a fixed and diminishing monetary issuance is that the currency will tend to be inherently deflationary. For each input, the referenced output must exist and cannot already be spent. How Bitcoin Works. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. The miners have to construct a perfect block, based on the shared rules that all nodes follow, genesis mining google chrome genesis mining is reliable mine it with a correct solution to the proof of work. As the newly solved reddit iota wallet hacked antminer lease moves across the network, each node performs a series of tests to validate it before propagating it to its peers. By independently verifying each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction poolroughly in the same order. Transactions like these are sometimes generated by wallet applications to clean up lots of smaller amounts that were received as change for payments. The new block is not just a checkered flag, marking the end of the race; it is also the starting pistol in the race for the next block. For example, the new blockbitcoins per block chart book on bitcoin blockchain a reference to the hash of its parent blockRunning this will produce the hashes of several phrases, made different by adding a number at the end of the text. Then, more transactions are added after it, for a total of transactions in the block. Nodes maintain three sets of blocks: If that node later sees another dash proof of stake cryptocurrency wallets exodus reddit block extending the same parent, it connects the second candidate on a secondary chain. Finally, the coinbase reward nSubsidy is added to the transaction fees nFeesand the sum is returned. For each input, if the referenced output exists in any other transaction in the pool, the transaction must be rejected. The solution to the problem, called the proof of work, is included in the new block and acts as proof gnt vs xrp bitcoin mining in one year the miner expended significant computing effort. Start Free Trial No credit card required. Unlike a fiat currency, which can be printed in infinite numbers by a central bank, bitcoin can never be inflated by printing.
Using the referenced output transactions to get input values, check that each input value, as well as the sum, are in the allowed range of values less than 21m coins, more than 0. With sufficient power, an attacker can invalidate six or more blocks in a row, causing transactions that were considered immutable six confirmations to be invalidated. After , all bitcoin miner earnings will be in the form of transaction fees. The bitcoin network can transact in fractional values, e. All the properties of bitcoin, including currency, transactions, payments, and the security model that does not depend on central authority or trust, derive from this invention. The priority of a transaction is calculated as the sum of the value and age of the inputs divided by the total size of the transaction:. At the time of this writing, the difficulty is so high that it is profitable only to mine with application-specific integrated circuits ASIC , essentially hundreds of mining algorithms printed in hardware, running in parallel on a single silicon chip. An invalid coinbase transaction would make the entire block invalid, which would result in the block being rejected and, therefore, that transaction would never become part of the ledger. Success with nonce Hash is f0ea21eb6dde5adb9da9f2bab2fcbca22b1e21a Elapsed Time: Successfully Mining the Block. Managed pools. Running the proof of work example for various difficulties. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record.
New transactions are constantly flowing into the network from user wallets and other applications. The increase in hashing power represents market forces as new miners enter the market to compete for the reward. If you think of the entire bit number space, each time you constrain one more bit to zero, you decrease the search space by half. Transactions are bundled into blockswhich require an enormous amount of computation to prove, but only a small amount of computation to verify as proven. Success with nonce Hash is cf12dbd20fcbaaedc6ffa9f74f5df4df0a3 Elapsed Time: Her smartphone shows a payment of 0. The index number of the UTXO to be spent, first one is 0. Rather, deflation is associated local bitcoin vs coinbase what if everyone used bitcoin a collapse in demand because that is the only example of deflation we have to study. The pool server runs specialized software and a pool-mining protocol that coordinates the activities of the pool miners. At the time of this writing, the difficulty is so high that it is profitable only to mine with application-specific integrated circuits ASICessentially hundreds of mining algorithms printed in hardware, running in parallel on a single silicon chip.
ProofOfWorkLimit ;. For each input, look in the main branch and the transaction pool to find the referenced output transaction. Independent Verification of Transactions. Running this will produce the hashes of several phrases, made different by adding a number at the end of the text. A hash algorithm takes an arbitrary-length data input and produces a fixed-length deterministic result, a digital fingerprint of the input. Unless you throw double-six, you win. When they mine a new block and extend the chain, the new block itself represents their vote. This is why independent validation is a key component of decentralized consensus. Mining Nodes. The process of mining is explained in detail in Introduction. Popular blockchain explorers include: At the time of this writing, the difficulty is so high that it is profitable only to mine with application-specific integrated circuits ASIC , essentially hundreds of mining algorithms printed in hardware, running in parallel on a single silicon chip. Alice, introduced in the previous chapter, is a new user who has just acquired her first bitcoin.
Independent verification of each transaction, by every full node, based on a comprehensive list of criteria Independent aggregation of those transactions into new blocks by mining nodes, coupled with demonstrated computation through a proof-of-work algorithm Independent verification of the new blocks by every node and assembly into a chain Independent selection, by every node, of the chain with the most cumulative computation demonstrated through proof of work. If we had a lower target higher difficulty it would take many more hash computations to find a suitable nonce, but only one hash computation for anyone to verify. Now, more than half the dice throws will add up to more than 5 and therefore be invalid. The approximate creation time of this block seconds from Unix Epoch. Spending the Transaction. Each of the blocks on the share chain records a proportionate share reward for the pool miners who contribute work, carrying the shares forward from the previous share block. Both blocks are valid, both blocks contain a valid solution to the proof of work, and both blocks extend the same parent. To give a simple analogy, imagine a game where players throw a pair of dice repeatedly, trying to throw less than a specified target.