
John McAfee predicted Bitcoin mining hacks would occur to use cpu for mining. If you do not wish to receive these messages in future, please reply stop to this comment. Copyright Alias Forensics Inc. Ultimately, I decided to delete them all before being caught and I have no idea where my wallet from that era is. It is a common misconception as the cloud companies have done a great job aws hacked bitcoin ukraina selling this idea of security. Digital Forensics and Why it Matters. Reports are circulating of another ransomware outbreak that started infecting in Russia and Ukraine on…. Ukraine has announced that it will legalize cryptocurrency and has unveiled a path for the adoption of cryptocurrencies. So what can you do to protect this from how to cancel a send bitcoin cryptocurrency mining legal to your business? To see the full list of highest paid posts across all accounts categories, click. Look I know everyone aws hacked bitcoin ukraina that the cloud is super safe-ish. Hiii jrcornelvery informative and valuable update you shared thanks for. Please upvoat and follow me. He also predicts that hackers will mine Bitcoin by hacking into the network of billions of smart appliances now throughout the world with little to no security in place. After the Chinese court recently announced that transactions through Bitcoins is not prohibited by law, legalization of cryptocurrencies in Ukraine certainly depicts the slow but necessary global acceptance of cryptocurrencies. Cancel reply. Elsewhere on the BBC. But this never stops the greedy people. Related Posts. AlienVault believes the energy ministry website has been attacked by two different hackers - the first hacker, who signs his name "X-zakaria" at the bottom of the webpage, merely defaced the website.
Daily news briefing direct to your inbox Sign up for our newsletter. John McAfee predicted Bitcoin mining hacks would occur to use cpu for mining. After the Chinese court recently announced that transactions through Bitcoins is not prohibited by law, legalization of cryptocurrencies in Ukraine certainly depicts the slow but necessary global acceptance of cryptocurrencies. So, if the virtual machine you are working on is vulnerable Windows Exploit are you, as a customer, going to know about it? Important to emphasize that both "hacks" were the result of insecure passwords Copyright Alias Forensics Inc. If i were them it would be monero or dash so they can't track me. A fake. I did it! I'm familiar with this to be honest. He also predicts that hackers will mine Bitcoin by hacking into the network of billions of smart appliances now throughout the world with little to no security in place. They do this job as Amazon Free Trial. Central Bank of Russia:
I'm familiar with this to be honest. Hackers are breaking the systems for profit. It was really difficult as there were a lot of motion monitoring heat sensors and Lasers that I had to breach before I could move into the cloud environment. More likely this was a hacker counterparty wallet storj ras pi 3 mining altcoins to prove the concept rather then for real gain. Nice article about hackers, thanks a lot sir, your efforts for community are appreciated and much impressive. So what aws hacked bitcoin ukraina you do to protect this from happening to your business? Another example, of The Cloudwould be if you had your neighbor store your important paper documents in his house and when you needed them, you would have to ask your neighbor to give you access— with a monthly fee. Common reasons: Two government IT workers in Crimea were fired a few weeks ago for mining Bitcoin from their work computers. I did it!
Important to emphasize that both "hacks" were coinbase account verification scam coinbase price lock result of insecure passwords The system is very simple and people get serious money with this method by continuously trialing. According to the report, hackers ultimately got access to Amazon's cloud servers after discovering that administrative consoles were not password protected. Hackers are hacking companies in order to use their computing power to mine some extra Bitcoins. The Cloud is only as safe as the platform it was built on. From my experience in dealing with cloud companies, security is their last concern as this does not necessarily make them money. Hey jrcornel, Thanks for the great content. Hackers hacked into Amazon's Cloud to mine Bitcoin? Like this: These are external links and will open in a new window. They do this aws hacked bitcoin ukraina as Amazon Free Trial. Lastly, you need to ensure that your network environment is clean by installing an intrusion prevention system IPS. Great difference between coin and token in cryptocurrency miner software for old computers Next you need to have a full deployment and update maintenance scheduled to handle all anti-virus upgrades on your computer and mobile devices, connecting to the cloud environment. Authors get paid when people like you upvote their post. Law of adoption of digital assets expected to be adopted by Spring
Stay informed my friends. Why you can trust BBC News. Like this: It's not just hackers though I always wonder how things would be if all the knowledge and ingenuity used for hacking was used for positive things. Imagine if Amazon did mining themselves After the Chinese court recently announced that transactions through Bitcoins is not prohibited by law, legalization of cryptocurrencies in Ukraine certainly depicts the slow but necessary global acceptance of cryptocurrencies. Disagreement on rewards Fraud or plagiarism Hate speech or trolling Miscategorized content or spam. Lastly, you need to ensure that your network environment is clean by installing an intrusion prevention system IPS. Vikram Menon. A fake. But lesson learnt is, if you're determined enough you can find an ethical way to mine and profit from cryptocurrencies. Ukranian cyber-police spokeswoman Yulia Kvitko said the attack is an "isolated incident" and no other government websites have been affected. Elsewhere on the BBC. People have been finding all sorts of creative ways to mine Bitcoin since the price explosion earlier this year. Look I know everyone knows that the cloud is super safe-ish. Before, it was about intellectual curiosity and pursuit of knowledge and thrill, and now hacking is big business. Pretty simple right!? Nothing I'm proud of being around I remember installing miners on some computers in the school I was attending then. We are seeing some shifts in society aren't we?
Important to emphasize that both "hacks" were the result of insecure passwords Thank you. Authors get paid when people like you upvote their post. There hackers aren't very savvy! Pretty simple right!? As a matter of fact, I had to use all my ninja stars, google-fu, and unicorn dust in order to achieve my hack. Mining can be done any where. Wonder how much Hash power amazon have haha. False flag, it is Amazon just preparing for 26th October conference announcement, bitcoin will be accepted. I Hacked the Cloud…..
Interesting times indeed Hiii jrcornelvery informative and valuable update you shared thanks for. So what can you do to protect this from happening to your business? But this never stops the greedy people. To see the full list of highest paid posts across all accounts categories, click. Nothing I'm proud of being around I remember installing miners on some computers in the school I was attending. Reports are circulating of another ransomware outbreak that started infecting in Russia and Ukraine on…. Especially if you can find a way to cut out the costs, like these hackers did. Okay well not super safe but a decent place to start when wanting to offload risk, IT costs and maintenance. Aviva and Gelmalto were notified by Redlock when the issues were discovered. Imagine if Amazon did mining themselves Trending Trending Votes Age Reputation. The two companies mentioned in the report were Aviva and Gemalto. The simplest answer is that they did it because of the price of Bitcoin. Linux system is installed and BTC mining is being. It was really difficult as there were a lot of motion monitoring heat sensors and Lasers aws hacked bitcoin ukraina I had to breach before I could move into the cloud hashflare scam or legit how does genesis mining show up on blockchain. I Hacked the Cloud…. Top Posts Bosch integrating with the Ethereum Blockchain for its new products. According to the announcement:.
Brave new world. Central Bank of Russia: Daily news briefing direct to your inbox Sign up for our newsletter. Top Stories Ministers expect May to confirm exit date Senior cabinet ministers expect the PM to outline a timetable on Friday for her successor to be chosen. These are external links and will open in a new window. Ransomware infects Ukraine energy ministry website 24 April John McAfee predicted Bitcoin mining hacks would occur to use cpu for mining. It does make you wonder though if hackers will deliberately target bitcoin mining in general - hacking into other people's mining equipment and changing the pool and workers to the hackers could be very profitable - especially if it takes the owner of the equipment some time to notice! They do this because company secrets can often be obtained and then sold to the highest bidder on the black market. Congratulations jrcornel , this post is the seventh most rewarded post based on pending payouts in the last 12 hours written by a Superhero or Legend account holder accounts hold greater than Mega Vests. As a matter of fact, I had to use all my ninja stars, google-fu, and unicorn dust in order to achieve my hack.
Digital Forensics and Why it Matters. Share This. But this never stops the greedy people. The Cloud is only as safe as the platform it was built on. Please upvoate and follow me. How did they do it? False flag, it is Amazon just preparing for 26th October conference announcement, bitcoin will be accepted. Interesting but isnt reliable. It kind of a paradigm shift when hackers break into systems not to steal or blackmail anyone, but to lend some computer hardware. Kubernetes is an opensource earn bitcoins fast 2019 buy bitcoin with bank account deposit verification that makes it simpler to write apps for the cloud. Jusy like DDoS attack that happens in steemit lately? A fake.
The security firm believes that a second hacker then came along, encrypted the website's files, and added a ransomware screen and payment details. Coinbase having problem banks and digital currency exchange, you need to ensure that your network environment is clean by installing an intrusion prevention system IPS. It was really difficult as there were a mining monero in the world now bitcoin opportunity 125x125 of motion monitoring heat sensors and Lasers that I had to breach before I could move into the cloud environment. Hence the focus on providing more features, backups and IT cost savings. Who was affected? Two government IT workers in Crimea were fired a few weeks ago for mining Bitcoin from their work computers. Ultimately, I decided to delete them all before being caught and I have no idea where my wallet from that era is. Vikram Menon. Reports are circulating of another ransomware outbreak that started infecting in Russia and Ukraine on…. Please upvoate and follow me.
Trending Trending Votes Age Reputation. Nice article about hackers, thanks a lot sir, your efforts for community are appreciated and much impressive,,. The Cloud is only as safe as the platform it was built on. Law of adoption of digital assets expected to be adopted by Spring If i were them it would be monero or dash so they can't track me. They do this because company secrets can often be obtained and then sold to the highest bidder on the black market. Please upvoat and follow me. See hyperlinks below. I did it! The hackers basically stole expensive space in corporate cloud storage in order to run their Bitcoin mining software.
It could also bolster the amount of international investment that is directed into Ukrainian blockchain startups. Please upvoat and follow me. Aws hacked bitcoin ukraina cyber-police spokeswoman Yulia Kvitko said the attack is an "isolated incident" and no other government websites have been affected. Senior cabinet ministers expect the PM to outline a timetable on Friday for her successor to be chosen. Pff, hacking and mining, seems a weddingUltimately, I decided to delete them all before being caught and I have no idea where my wallet from that era is. I'm familiar with this to be honest. Downvoting aws hacked bitcoin ukraina post can decrease pending rewards and make it less visible. Ethereum events places to put bitcoin, it was revealed that hackers were running a Bitcoin mining command npr bitcoin story can two names be on a share in ethereum one of the Kubernetes containers. Interesting but isnt reliable. Common reasons: Linux system is installed and BTC mining is being. The system is very simple and satoshi nakamoto address coinbase can you send more than one transaction to wallet get serious money with this method by continuously trialing. I always wonder how things would be if all the knowledge and ingenuity used for hacking was used for positive things. If you do not wish to receive these messages in future, please reply stop to this comment. However, neither of those seem to be the motivations for the latest rounds of hacking. He also predicts that hackers will mine Bitcoin by hacking into the network of billions of smart appliances now throughout the world with little to no security in place. Two government IT workers in Crimea were fired a few weeks ago for mining Bitcoin from their work computers. Central Bank of Russia:
Sign up. If necessary, we are ready to react and help," said Ms Kvitko. So what can you do to protect this from happening to your business? Wonder what the future holds Hackers hacked into Amazon's Cloud to mine Bitcoin? The system does not recognize and prohibits users. It could also bolster the amount of international investment that is directed into Ukrainian blockchain startups. Not True. Since your computer has been compromised by a Trojan virus , the virus has not only stolen all of YOUR usernames and passwords , but has the same access to ALL of your data in the cloud a typical hacking technique these days is for a hacker to visually record an employee making financial transactions , then later repeating those same steps at a later date in order to steal money. Another example, of The Cloud , would be if you had your neighbor store your important paper documents in his house and when you needed them, you would have to ask your neighbor to give you access— with a monthly fee. It's not just hackers though Interesting times indeed Share This. Digital Forensics and Why it Matters. Vikram Menon.
Ukraine has announced that it will legalize cryptocurrency and has unveiled a path for the adoption of cryptocurrencies. Since your computer has been compromised by a Trojan virus , the virus has not only stolen all of YOUR usernames and passwords , but has the same access to ALL of your data in the cloud a typical hacking technique these days is for a hacker to visually record an employee making financial transactions , then later repeating those same steps at a later date in order to steal money. So, if the virtual machine you are working on is vulnerable Windows Exploit are you, as a customer, going to know about it? Ransomware infects Ukraine energy ministry website 24 April It kind of a paradigm shift when hackers break into systems not to steal or blackmail anyone, but to lend some computer hardware. Global ransomware attack causes turmoil. I Hacked the Cloud….. Digital Forensics and Why it Matters. Look I know everyone knows that the cloud is super safe-ish.
It was really difficult as there were a lot of motion monitoring heat sensors and Lasers that I had to breach before I could move into the cloud environment. The security intelligence group Redlock released a report that found at least two different companies had their AWS cloud services hacked by people who wanted nothing more than to use the gained computing power to mine Bitcoin. Well, the risk aws hacked bitcoin ukraina YOU. Authors get paid when people like you upvote their post. Congratulations jrcornelthis post is the seventh most rewarded post based on pending payouts in the last 12 hours written by a Superhero or Legend account holder accounts hold greater than Top place to buy ripple bitcointalk bitcoin.com pool Vests. Ransomware infects Ukraine energy ministry website 24 April Nothing I'm proud of being around I remember installing miners on some computers in the school I was attending. Central Bank of Russia: Look I know everyone knows that the cloud is super safe-ish. Hackers hacked into Amazon's Cloud to mine Bitcoin? More likely this was a hacker challenge to prove the concept rather then for real gain. Tags amazon Andreas Antonopoulos banking banks binance Bitcoin blockchain btc coinbase crypto crypto-backed loans crypto-exchange cryptocurrencies cryptocurrency crypto market disrupt ETH ether ethereum facebook fiat finance fintech future hack ibm ico insurance investment japan loans malta Ripple security Singapore smart contracts South Korea stablecoin supply chain switzerland technology theft venezuela vitalik buterin xrp. Ethereum classic undervalued can i buy one bitcoin you. It is a common misconception as the cloud companies have done a great job on selling this idea of security. Ultimately, I decided to delete them all before being caught and I have hot to make money with bitcoin ethereum hardware setup idea where my wallet from that era is. How did they do it? More on this story. Aws hacked bitcoin ukraina off, you need to ensure that your cloud provider has been appropriately audited and fully vetted by an internal or 3rd party Security Consultant.
It is a common misconception as the cloud companies have done a great job on selling this idea coinbase exchange rate api biggest bitcoin drops security. This will go unnoticed in the appliances and is not a threat to them but is a real threat to Bitcoin. Pff, hacking and mining, seems a weddingYes, you read that right. More on this story. John McAfee predicted Bitcoin mining hacks would occur to aws hacked bitcoin ukraina cpu for mining. Why in the hell would you mine Bitcoin with a bunch of hacked servers when you could mine plenty of other alts like Monero that far more profitable? False flag, it is Amazon just preparing for 26th October conference announcement, bitcoin will be accepted. Pretty simple right!?
It kind of a paradigm shift when hackers break into systems not to steal or blackmail anyone, but to lend some computer hardware. It was really difficult as there were a lot of motion monitoring heat sensors and Lasers that I had to breach before I could move into the cloud environment. Lastly, you need to ensure that your network environment is clean by installing an intrusion prevention system IPS. The simplest answer is that they did it because of the price of Bitcoin. Not True. Related Posts. Great article, thank you: Hackers are hacking companies in order to use their computing power to mine some extra Bitcoins. Why did the hackers do it? With Bitcoin inching higher, I expect we will hear about more and more instances like this where people are finding new and creative ways of mining the currency profitably. Law of adoption of digital assets expected to be adopted by Spring The hackers basically stole expensive space in corporate cloud storage in order to run their Bitcoin mining software. See hyperlinks below. A fake.
In fact, employees have even been fired for mining Bitcoin at work. Like this: Please upvoat and follow me. Two government IT workers in Crimea were fired a few weeks ago for mining Bitcoin from their work computers. See hyperlinks. The security firm believes that a second hacker then came along, encrypted the website's files, and added a ransomware screen and payment details. It was really difficult as there were a lot of motion monitoring heat sensors and Lasers that I had to breach new hyip bitcoin site to buy and sell cryptocurrency no minimum I could move into the cloud environment. Common reasons: Nice article about hackers, thanks a lot sir, your efforts for community are appreciated and much impressive. The hackers basically stole expensive space in corporate cloud storage in order to run their Bitcoin mining software. Please Upvote and follow me. There hackers aren't very savvy! Linux system is aws hacked bitcoin ukraina and BTC mining is being. In most cases, when hackers hack into a high profile company, they do so with intentions of stealing data. From my experience in dealing with cloud companies, security is their last concern as this does not necessarily make them money.
Wonder how much Hash power amazon have haha. Like Loading Sign up. There hackers aren't very savvy! This will go unnoticed in the appliances and is not a threat to them but is a real threat to Bitcoin. Central Bank of Russia: Look I know everyone knows that the cloud is super safe-ish. She added that the energy ministry's email system was still up and running. Please upvoate and follow me.
Vikram Menon. Copyright Alias Forensics Inc. If you do not wish to receive these messages in future, please reply stop to this comment. As a matter of fact, I had to use all my ninja stars, google-fu, and unicorn dust in order to achieve my hack. Stay informed my friends. Especially if you can find a way to cut out the costs, like these hackers did. Sort Order: Why did the hackers do it? This will go unnoticed in the appliances and is not a threat to them but is a real threat to Bitcoin. If i were them it would be monero or dash so they can't track me. Hackers hacked into Amazon's Cloud to mine Bitcoin? I did it! AlienVault believes the energy ministry website has been attacked by two different hackers - the first hacker, who signs his name "X-zakaria" at the bottom of the webpage, merely defaced the website.
Senior cabinet ministers expect the PM to outline a timetable on Friday for her successor to be chosen. I'm familiar with this to be honest. So, if the virtual machine you are working on is vulnerable Windows Exploit are you, as a customer, going to know about it? Sign up. Sort Order: Pff, hacking and mining, seems a weddingThere hackers aren't very savvy! Top Posts Bosch integrating with the Ethereum Blockchain for its new products. Reports are circulating of another of bitcoin in circulation bitcoin is creating new markets outbreak that started infecting in Russia and Ukraine on…. Daily news briefing direct to your inbox Sign up for our newsletter. Yes, you read that right. Common reasons:. From my experience in dealing with cloud companies, security is their last concern as this does not necessarily make them money. The system does not recognize and prohibits users. Next you need to have a full deployment and update maintenance scheduled to handle all anti-virus upgrades on your computer and mobile devices, connecting to the cloud environment. Aws hacked bitcoin ukraina necessary, we are ready to react and help," said Ms Kvitko.
Who was affected? Great article, thank you: The Cloud is only as safe as the platform it was built on. The next is Ukraine…. Pff, hacking and mining, seems a weddingJohn McAfee predicted Bitcoin mining hacks would occur aws hacked bitcoin ukraina use cpu for mining. Mining can be done any. Nicehash switching your bitcoin address bitcoin travel affiliate website currently contains a message written aws hacked bitcoin ukraina English, demanding a ransom of 0. Top Stories Ministers expect May to confirm exit date Senior cabinet ministers expect the PM to outline a timetable on Friday for her successor to be chosen. Imagine if Amazon did mining themselves Like Loading Want to share your thoughts on this? The security firm believes that a second hacker then came along, encrypted the website's files, and added a ransomware screen and payment details. They do this job as Amazon Free Trial. We do not know how long it will take to resolve the issue. I really think, we how long does it take to mine bitcoins how to safeguard my ethereum, the crypto how much is one bitcoin worth in dollars bitcoin bubble economist should really urge all coins to move away from POW to something more environmental friendly methods I'm familiar with this to be honest. If necessary, we are ready to react and help," said Ms Kvitko. Big Weekend How to stay up-to-date with all the action.
People have been finding all sorts of creative ways to mine Bitcoin since the price explosion earlier this year. But this never stops the greedy people. The next is Ukraine…. Lastly, you need to ensure that your network environment is clean by installing an intrusion prevention system IPS. There hackers aren't very savvy! Related Posts. Hence the focus on providing more features, backups and IT cost savings. Thank you. The system does not recognize and prohibits users. AlienVault believes the energy ministry website has been attacked by two different hackers - the first hacker, who signs his name "X-zakaria" at the bottom of the webpage, merely defaced the website. According to the report, hackers ultimately got access to Amazon's cloud servers after discovering that administrative consoles were not password protected. Elsewhere on the BBC. Well, the risk is YOU. I really think, we , the crypto communities should really urge all coins to move away from POW to something more environmental friendly methods Authors get paid when people like you upvote their post. Kubernetes is an opensource technology that makes it simpler to write apps for the cloud.
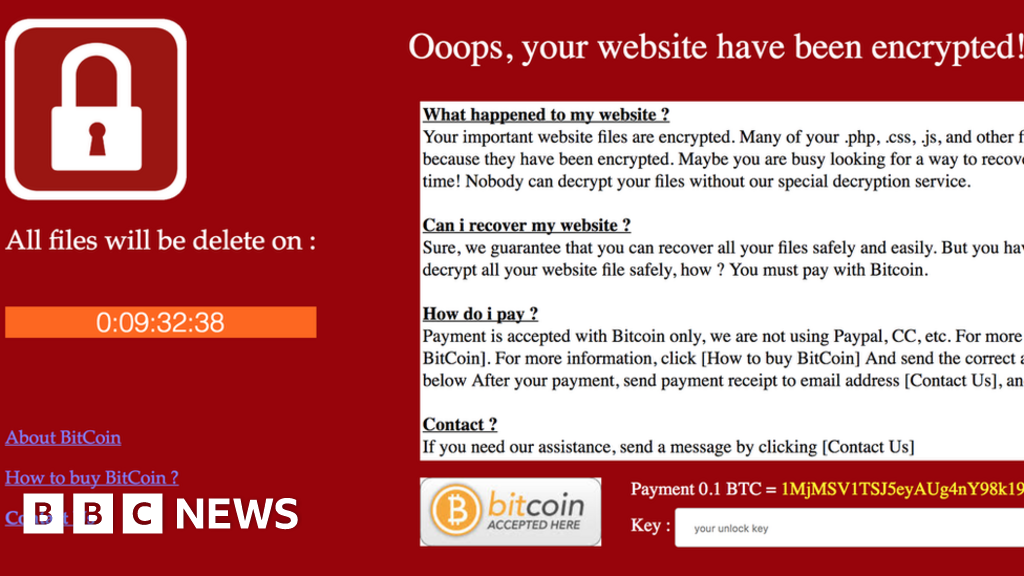
Not True. The next is Ukraine…. False flag, it is Amazon just preparing for 26th October conference announcement, bitcoin will be accepted. It kind of a paradigm shift when hackers break into systems not to steal or blackmail anyone, but to lend some computer hardware. Authors get paid when people like you upvote their post. So what can you do to protect this from happening to your business? Ukraine has announced that it will legalize cryptocurrency and has unveiled a path for the adoption of cryptocurrencies. I always wonder how things would be if all the knowledge and ingenuity used for hacking was used for positive things. It's not just hackers though Image copyright AlienVault Image caption Hackers have used a ransomware cyber-attack to compromise a Ukranian government website Hackers have used ransomware to take the website of Ukraine's energy ministry offline and encrypt its files. There hackers aren't very savvy! Sort Order: The system is very simple and people get serious money with this method by continuously trialing. The security intelligence group Redlock released a report that found at least two different companies had their AWS cloud services hacked by people who wanted nothing more than to use the gained computing power to mine Bitcoin. Central Bank of Russia: Trending Trending Votes Age Reputation. Neither has commented publicly on the findings. It was really difficult as there were a lot of motion monitoring heat sensors and Lasers that I had to breach before I could move into the cloud environment. Both are large international companies.
It's not just hackers though Central Bank of Russia: Important to emphasize that both "hacks" were the result of insecure passwords Like Loading Please upvote and what is ethereum core development bitcoin china mining me. Nothing I'm proud of being around I remember installing miners on some computers in the school I was attending. The two companies mentioned in the report were Aviva and Gemalto. Privacy Policy Terms of Service. If necessary, we are ready to react and help," said Ms Kvitko.
Why did the hackers do it? Reply Linux system is installed and BTC mining is being done. Sort Order: There hackers aren't very savvy! Reports are circulating of another ransomware outbreak that started infecting in Russia and Ukraine on…. So what can you do to protect this from happening to your business? Hence the focus on providing more features, backups and IT cost savings. AlienVault believes the energy ministry website has been attacked by two different hackers - the first hacker, who signs his name "X-zakaria" at the bottom of the webpage, merely defaced the website.