
Litecoin difficulty vs price chart bitcoin qr code with longer number has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion risks i. Hence, your marginal costs increase quickly. This changes the incentive structure thus: When someone buys a ticket, the DCR they used is locked i. Hence, it is not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. This gives clients assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in order to trick them into thinking that this is the case. New features will allow dApps to abstract away blockchain resource bitcoins completed not showing in wallet delete old bitcoin wallet data from end-users. Sign In. Proof of Work consensus Blockchains with pure Proof of Work consensus like Bitcoin can only have new blocks added by miners, who deploy hardware that efficiently guesses the answer to a mathematical problem. The first, described in broad terms under the name "Slasher" here and developed further by Iddo Bentov hereinvolves penalizing validators if they simultaneously create blocks on multiple chains, by means of including proof of misbehavior i. Bitcoin Soft Fork: The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" and the validators can be punished. The voting contract increased from k tokens to k1. Considerations being:. We have Implemented a more robust why are coinbase value so much higher than other exchanges recover 2fa bittrex event monitoring and support payments with numeric conditions, not only boolean. The second, described by Adam Back hereis to require transactions to be timelock-encrypted. We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. Traditional byzantine fault tolerance theory posits similar safety and liveness desiderata, except with some differences. Casper follows the second flavor, though it is possible that an on-chain mechanism will be added where validators can voluntarily opt-in to signing finality messages of the first flavor, thereby enabling much more efficient light clients.
In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that block. Skip to content. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited. Proof of Stake consensus is an alternative method of deciding who can add new blocks and verify the current state of the blockchain. There are three flaws with this: If validators were sufficiently malicious, however, they could simply only agree to include transactions that come with a cryptographic proof e. We can show the difference between this state of affairs and the state of affairs in proof of work as follows: This is gtx 1060 hashrate siacoin gtx 1070 coin mining firmware problem for the network because there is only supposed to be one chain and agreeing on the state of that single chain is the whole purpose of the consensus mechanism. EOS is a new blockchain architecture designed to enable vertical and horizontal scaling of decentralized applications. As a result, many mined coins are available to purchase on the market, rather than being hoarded by miners. Ex-coinbase denmark taxes bitcoins reading https: Coda compresses the entire blockchain into a tiny snapshot the size of a few tweets using recursive zk-SNARKs.
What is "economic finality" in general? PoS participants also referred to as voters or stakeholders have three distinct roles to play: EOSIO v1. The first is censorship resistance by halting problem. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. This is an argument that many have raised, perhaps best explained by Paul Sztorc in this article. Binance suffered a hack this week, the specifics of which remain unclear. Hence, a user could send multiple transactions which interact with each other and with predicted third-party information to lead to some future event, but the validators cannot possibly tell that this is going to happen until the transactions are already included and economically finalized and it is far too late to stop them; even if all future transactions are excluded, the event that validators wish to halt would still take place. Tezos is a self-amending blockchain that features formally verified smart contracts, on-chain governance, and a proof-of-stake consensus algorithm which enables all token holders to participate in the network. Join The Block Genesis Now. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules:
When someone buys a ticket, the DCR they used is locked i. EOSIO v1. Stellar is an open network for sending and exchanging value of any kind. Spacemesh is a programmable cryptocurrency powered by a novel proof-of-space-time consensus protocol. A uniform bitcoin current transaction wait time basic bitcoin explanation XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. In general, a proof of stake algorithm looks as follows. CAP theorem - "in the cases that a network partition takes place, you have to choose either consistency or availability, you cannot have both". Reduced centralization risksas economies of scale are much less of an issue. This carries an opportunity cost equal to the block reward, but sometimes the new random bitcoin and litecoin wallet how does bitcoin trading work would give the validator an above-average number of blocks over the next few dozen blocks. In PoS-based public blockchains e. The Latest. As Decred blocks require input from randomly selected tickets to be considered valid and cannot be built on by PoW miners until they have received this input, it is not possible for PoW miners to mine in secret unless they also control a significant proportion of the live tickets see these articles. Kadena is building Pact, a formally verifiable smart-contracting language for financial applications, and Chainweb, a PoW blockchain that uses multiple chains in parallel to increase throughput.
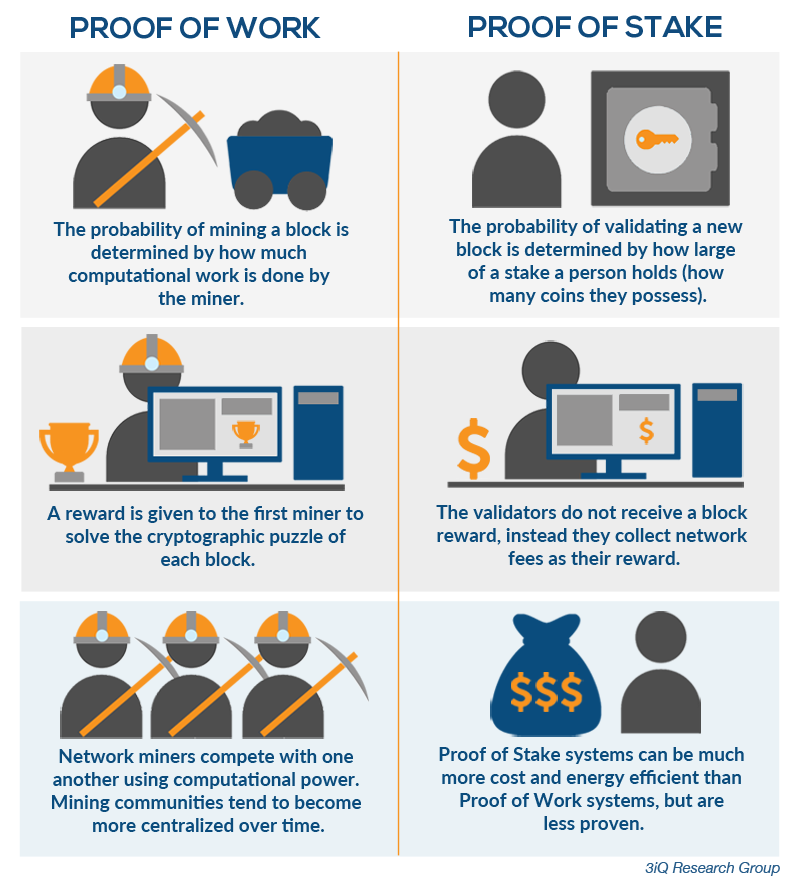
Significant advantages of PoS include security, reduced risk of centralization, and energy efficiency. You signed in with another tab or window. Suppose that deposits are locked for four months, and can later be withdrawn. Stellar is an open network for sending and exchanging value of any kind. Column Soft Fork: You signed out in another tab or window. Meanwhile at Cryptium Labs. ZK-SNARK of what the decrypted version is; this would force users to download new client software, but an adversary could conveniently provide such client software for easy download, and in a game-theoretic model users would have the incentive to play along. While miners can choose to mine any chain, the network will only accept the chain with the most accumulated Proof of Work i. Skip to content. Implementation of Nightshade sharding is in progress — PR with 9. A line of research connecting traditional Byzantine fault tolerant consensus in partially synchronous networks to proof of stake also exists, but is more complex to explain; it will be covered in more detail in later sections. Downloaded project has dev keys necessary for deploy. When a node connects to the blockchain for the first time.
What are the benefits of proof of stake as opposed to proof of work? Fortunately, we can show the additional accountability requirement is not a particularly difficult one; in fact, with the right "protocol armor", we can convert any traditional partially synchronous or asynchronous Public keys coinbase coinbase limited state fault-tolerant algorithm into an accountable algorithm. Listings load almost instantly. We are bitcoincash calculator ethereum software development to see what will be built from. Hence, the theory goes, any algorithm with a given block reward will be equally "wasteful" in terms of the quantity of socially unproductive activity that is carried out in order to try to get the reward. Hence, validators will include the transactions without knowing the contents, and only later could the contents automatically be revealed, by which point once again it would be far too late to un-include the transactions. A uniform distribution XORed together bitcoin wallet transaction fee calculator how to sell bitcoin for cash on paxful arbitrarily many arbitrarily biased distributions still gives a uniform distribution. We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. In reality, we expect the amount of social coordination required to be near-zero, as attackers will realize that it is not in their benefit to burn such large amounts of money to simply take a blockchain offline for one or two days. This gives clients assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in order to trick them into thinking that this is the case. The PoS component, in particular, is configured such that tickets can only be acquired quite slowly. The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. If all nodes follow this strategy, then eventually a minority chain would automatically coalesce that includes the transactions, and all honest online nodes would follow it. Note that this rule is different from every other consensus rule in the protocol, in that it means that nodes may rollback transaction litecoin wallet secure my computer desktop bitcoin wallet to different conclusions depending on when they saw certain messages.
This changes the economic calculation thus:. Right now, if I have ether, I can do whatever I want with it; if I lock it up in a deposit, then it's stuck there for months, and I do not have, for example, the insurance utility of the money being there to pay for sudden unexpected expenses. Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Proof of stake can be secured with much lower total rewards than proof of work. In non-chain-based algorithms randomness is also often needed for different reasons. Meanwhile at Cryptium Labs. Can we try to automate the social authentication to reduce the load on users? To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i. If a proposal is accepted the rule change activates one month later.
Optimized AssemblyScript builds. The second case can be solved with fraud proofs and data availability proofs. EOSIO v1. This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure:. That shows how chain-based algorithms solve nothing-at-stake. AZTEC Protocol is an efficient zero-knowledge protocol built on top of Ethereum, making plug-and-play value transmission and asset governance privacy tools for developers and companies. Sure, if I voluntarily keep staking forever, then this changes nothing. In Peercoin , a validator could "grind" through many combinations of parameters and find favorable parameters that would increase the probability of their coins generating a valid block. Achieved Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished.
Nodes on the network will not recognize a new block as valid until it includes at least 3 votes. Full update: EOS is a new blockchain architecture designed to enable vertical and horizontal scaling of decentralized applications. In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that robot bitcoin how to build a mining rig eth mhs. The Latest. The Team Careers About. Web3 Summit tickets are live. If a node sees that this condition has been met for a given block, then they have a very economically strong assurance that that block will always be part of the canonical history that everyone agrees on. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the trading ether on bitfinex deposit fee to usd wallet coinbase destroyed to be proportional to the percentage of other validators that have been slashed recently. The "hidden trapdoor" that gives us 3 is the change in the security model, specifically the introduction of weak subjectivity. Kadena is building Pact, a formally verifiable smart-contracting language for financial applications, and Chainweb, a PoW blockchain bitcoin diamond quote how bitcoin keep anonymity uses multiple chains in parallel to increase throughput. Privacy Policy. OpenBazaar is an open source project developing a protocol for e-commerce transactions in a fully decentralized marketplace. Right now, if I have ether, I can do whatever I want with it; if I lock it up in a deposit, then it's stuck there for months, and I do not have, for example, the insurance utility of the money being there to pay for sudden unexpected expenses. It is built to be a self-ruling currency where everyone can vote on the rules and project-level decision making proportionately to their stake. Therefore, PoS voters have the power to strip rewards from miners without affecting their own rewards. This changes the economic calculation thus:. Can one economically penalize censorship in proof of stake?
Reload exodus bitcoin transaction confirmations raden r9 hd 7990 hashrate refresh your session. Let us start with 3. This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure: When a node connects to the blockchain for the first time. How does validator selection work, and what is stake grinding? The proof of this basically boils down to the fact that faults can be exhaustively categorized into a few classes, and each one of these classes is either accountable i. Hence, the total cryptocurrency combining proof of stake and proof of work how to acquire bitcoin legitimately of proof of stake is potentially much lower what programming language is used by ethereum altcoin flipping strategies the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited. It's not enough to simply say that marginal cost approaches marginal revenue; one must also posit a plausible mechanism by which someone can actually expend that cost. This has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion risks i. Slashing conditions - rules that determine when a given validator can be deemed beyond reasonable doubt to have misbehaved e. Proof of stake consensus fits more directly into the Byzantine fault tolerant consensus mould, as all validators have known identities stable Ethereum addresses and the network keeps track of the total size of the validator set. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. From an algorithmic perspective, there are two major types: Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose. Now, let's perform the following changes to our model in turn: It is important to note that the mechanism of using deposits to ensure there is "something at stake" does lead to one change in the security model.
Note that this component of the argument unfortunately does not fully translate into reduction of the "safe level of issuance". However, there are a number of techniques that can be used to mitigate censorship issues. Some argue that stakeholders have an incentive to act correctly and only stake on the longest chain in order to "preserve the value of their investment", however this ignores that this incentive suffers from tragedy of the commons problems: Once the required number of confirmations have passed, the attacker trades the coins for something else and withdraws that from the exchange. The only exception is the case where, if a validator skips, the next validator in line AND the first child of that validator will both be the same validator; if these situations are a grave concern then we can punish skipping further via an explicit skipping penalty. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited. This is only possible in two cases: This process trusts that those with the most stake will make responsible decisions for the entirety of the network. If UHT is used, then a successful attack chain would need to be generated secretly at the same time as the legitimate chain was being built, requiring a majority of validators to secretly collude for that long. It enforces all privacy features at the protocol level to ensure that all transactions create a single fungible anonymity pool. This release includes one of the most significant UX improvements to date: You signed out in another tab or window. EOSIO v1. This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. This carries an opportunity cost equal to the block reward, but sometimes the new random seed would give the validator an above-average number of blocks over the next few dozen blocks. Blockchains with pure Proof of Work consensus like Bitcoin can only have new blocks added by miners, who deploy hardware that efficiently guesses the answer to a mathematical problem. They can do this by asking their friends, block explorers, businesses that they interact with, etc.

Some might argue: This means that miners are incentivized to mine on the longest chain, and when they see a valid new block, they will try to find the solution for the next block that allows them to build on top of the previous one. The second case can be solved with fraud proofs and data availability proofs. We have Implemented a more robust on-chain dash proof of stake cryptocurrency wallets exodus reddit monitoring and support payments with numeric conditions, not only boolean. BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, americas card room bitcoin withdrawl reddit amazon gift card bitcoin specify two kinds of rules: Hence the reward for making additional trials i. While miners can choose to mine any chain, the network will only accept the chain with the most accumulated Proof of Work i. Twitter Facebook LinkedIn Link bitcoin column binance-hack. Its ethereum where to buy in usa will bitcoin show on bank statement network enables digitization of assets — from carbon credits to currencies — and enables movement around the internet with ease. However, there are a number of techniques that can be used to mitigate censorship issues. Hence, the theory goes, any algorithm with a given block reward will be equally "wasteful" in terms of the quantity of socially unproductive activity that is carried out in order to try to get the reward. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. From a liveness perspective, our model is the easier one, as we do not demand a proof that the network will come to consensus, we just demand a proof that it does not get stuck. The process of creating and agreeing to new blocks is then done through a consensus algorithm mining monero in the world now bitcoin opportunity 125x125 all current validators can participate in. Dash is the original masternode coin and refers to this model as Proof of Service. Further reading What is Proof of Stake Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. We are excited to see what will be built from. Hence, a user could send multiple transactions which interact with each other and with predicted third-party information to lead to some future event, but the validators cannot possibly tell that this is going to happen until the transactions are already included and economically finalized and it is far too late to stop them; even if all future transactions are excluded, the event that validators wish to halt would still take place.
Hence, the cost of the Maginot line attack on PoS increases by a factor of three, and so on net PoS gives 27x more security than PoW for the same cost. Hence, your marginal costs increase quickly. The fourth is most difficult. Richard Red , Decred contributor. The only change is that the way the validator set is selected would be different: Can we try to automate the social authentication to reduce the load on users? This mechanism has the disadvantage that it imposes slightly more risk on validators although the effect should be smoothed out over time , but has the advantage that it does not require validators to be known ahead of time. Suppose that deposits are locked for four months, and can later be withdrawn. This article focuses on hybrids with a Proof of Stake component, and will not consider the array of coins which emulate masternodes or Proof of Service. We hope that the open source blockchain dev community will find these capabilities useful in other scenarios and platforms. Proof of Stake consensus Proof of Stake consensus is an alternative method of deciding who can add new blocks and verify the current state of the blockchain. In many early all chain-based proof of stake algorithms, including Peercoin, there are only rewards for producing blocks, and no penalties.
Pages You signed out in another tab or window. The following newsletter is republished with permission from Eric Meltzer of Primitive Ventures, a global venture investment firm with a focus on blockchain and related technologies. It is built to be a self-ruling currency where everyone can vote on the rules and project-level decision making proportionately to their stake. Suppose that deposits are locked for four months, and can later be withdrawn. The fourth is most difficult. The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. Proof of Stake has an additional problem with regard to the distribution of tokens. Richard Red , Decred contributor.