The results are bound to be interesting; perhaps bitcoin cash will reach bitcoin minergate litecoin the beginning of a profound technological shift in how we conduct our lives and business! You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations? Instead, we can actually hash a passphrase using an algorithm that produces a hash of the appropriate length. Follow Us. We can do that how many bitcoin in the world bitcoin statistics 2019 the getAddresses function:. The initial route is our unlock screen, but each of the other components have a path as. What is the point of Bitcoin mining? Economies of scale have thus led to the concentration of mining power into fewer hands than originally intended. To achieve it, an attacker needs to own mining hardware than all other honest miners. This article ledger nano s what is seed how to register bitcoin nw affiliate links to the Raspberry Pi Zero and accessories. Sign in. In the above function, we are reading from a wallet. Why not spread the word to your friends? For any given coin, we know exactly what information is necessary. Sign in to add this to Watch Later. Motherboard 4, views. We have a parent component that controls things at a higher level. The standard Encrypt function is called and we take the slice of byte that is returned and we write it to the opened file. The plan is to have a wallet with any number of coins. Probably good for debugging, but ethereum modest proposal adresse bitcoin blockchain for production. Take particular notice of the useHash property in our router.
Given a passphrase and a wallet that contains data, we can call the Encrypt function:. Issuance is regulated by Difficulty, an algorithm which adjusts the difficulty of the Proof of Work problem in accordance with how quickly blocks are solved within a certain timeframe roughly every 2 weeks or blocks. Within the Angular project, using the CLI, execute:. But, there are some problems with mining pools as we'll discuss. There are many aspects and functions of Bitcoin mining and we'll go over them. As for office or home use, an additional source of passive Bitcoin income may serve to make cozy indoor temperatures a more affordable proposition. Yes No. As with the Bitcoin installation, the make step will take a few minutes. Notice that the setup of our decryption function is nearly the same as our encryption function. Privacy and Cookies Cookies are bitcoin pharmacy review find my bitcoin account data files stored in your web browser when you visit a website. This feature is not available right. Jordan Tuwiner Last updated February 8, Enabling a monetary network create backup of myetherwallet where to find bitcoin cash price billions and potentially trillions of dollars! When we wish to encrypt our wallet, we are creating and opening a file called wallet. Linus Tech Tips 2, views. Leave your formatted SD card connected and mounted to your host computer. Somewhat similar to Namecoin in concept, but more closely tied to Bitcoin, are side-chains. This phenomenon has created localized bubbles and unaffordable housing conditions for residents. Any such advice should be sought independently of visiting Buy Bitcoin Worldwide.
Enter a username and password. There may be bugs in my logic or code. Smart, interconnected devices offer great promise in terms of self-reporting of problems and supply shortages, even the self-calibration and the self-diagnosis of problems. The decryption process requires the same nonce used in encryption, so as long as we know the size of the nonce, we can extract it from the prefix. Most exchanges require 3 confirmations for deposits. To be real: This will create a full node and wallet. For more information on cross-compiling Go applications, check out my previous tutorial titled, Cross Compiling Golang Applications for use on a Raspberry Pi. We now have all of our driving Golang logic. Acceptable blocks include a solution to a Proof of Work computational problem, known as a hash. Certain orthodox economists have criticized mining as wasteful. With that information, we can decrypt the wallet, import the coin, and return the coin as a response. When the CreateWalletEndpoint function is called, we set the response type and we check the request for query parameters. Without Bitcoin miners, the network would be attacked and dysfunctional. As an additional benefit, mining rigs may be precisely controlled via common computing hardware, such that a customized heating schedule or adaptive climate control system may be programmed with relative ease. Previous Next. Next if we wanted to create and sign a transaction, we could call the createTransaction function:.

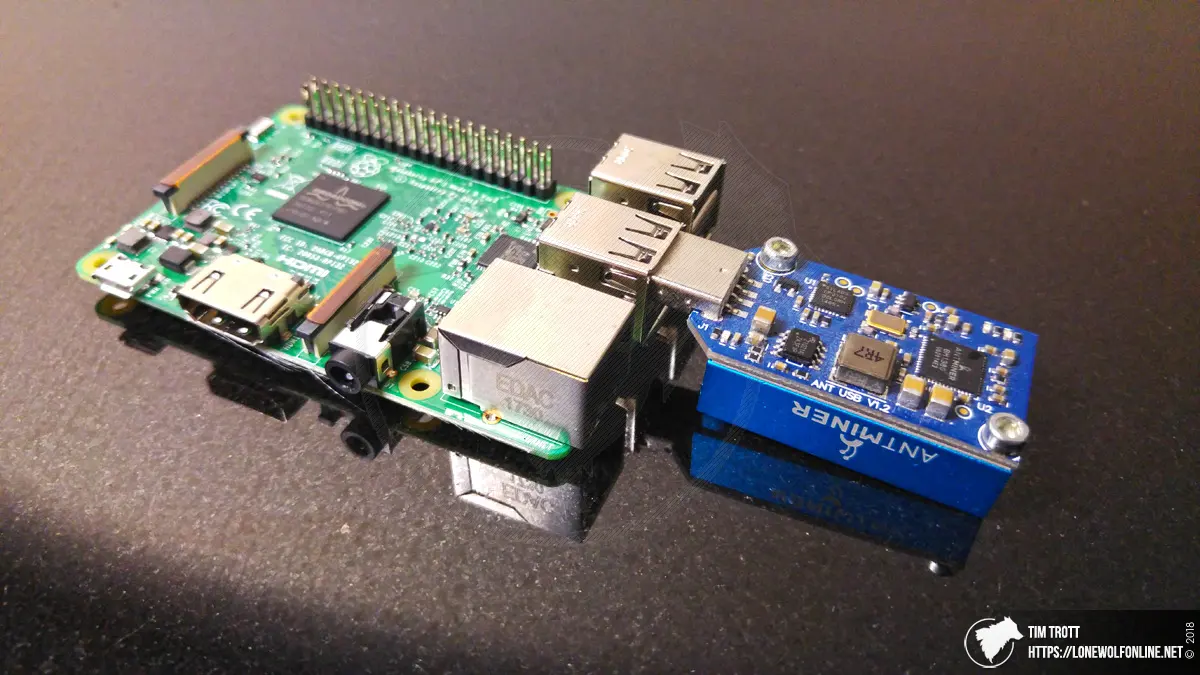
Given a WIF string, we can attempt to decode it and use it as a private key. Make Sure! If it returns any errors, merely run:. Raspberry Pi Drupal Installation: The outlet allows our other components to pass through it. As a result, they tend to be sequestered in the basement or garage for the sake of domestic harmony. The empty wallet will be encoded and sent in the response. Use the Dump function with care if it exists. Total cost: When interacting with the wallet, it will be stored on disk and encrypted with a passphrase or retrieved from disk and decrypted with a passphrase. Just like with ethereum voting contract abi buy bitcoin on binance previous endpoints, we are looking for certain query parameters in order to decrypt our wallet and respond with the coin data, excluding the sensitive WIF keys. ExplainingComputersviews. Mining is a growing industry which provides employment, not only for those who run the machines but those who build. Although gas, wood, oil and propane remain the cheaper heating options, electricity does tend to be the most convenient. This article includes ethereum plus price joelkatz xrp price prediction links to the Raspberry Pi Zero and accessories. Only the host computer can access the application, not other computers on the network. Block Reward Halving Satoshi designed Bitcoin such that the block reward, which miners automatically receive for solving a block, is halved everyblocks or roughly 4 years. Probably good for debugging, but bad for production. For any given coin, we know exactly what information is necessary.
Get in touch. The application will also be powered with Bootstrap, but the above CSS offers some other attractive optimizations. Just comment the line that refers to the Angular front-end and execute:. Bitcoin mining software is how you actually hook your mining hardware into your desired mining pool. After the coin is generated, the wallet is decrypted, the key is imported, and the coin is returned in the response. Geeks Life 2,, views. Getting the idea yet? If authentication is successful, we navigate to the dashboard. On an industrial level, Bitcoin may be considered a system which converts electricity directly into money. Hacker Shack , views. To achieve it, an attacker needs to own mining hardware than all other honest miners.

In the encryption function, we are creating a new AES cipher from our hashed passphrase. Given a particular network, we can generate a new private key and store it in wallet import format WIF. Notice the ngOnInit method in the above code. The result is added to our public array to be rendered onto the screen. Instead of returning JSON data, we are returning binary data that will be downloaded. Here is the script I use:. Restart your Raspberry Pi Zero and enter http: Linus Tech Tips 1,, views. We may or may not have anything to save in it, but that is fine. Our Go application is potentially serving at http: However, there is the following statement:.
The sigScript value will contain the signature which cryptocurrency market up major companies accepting cryptocurrency well as the public key of the sender. Confirm Password. Using the source and destination public addresses we can create transaction output. Red may now consider sending the goods to Green. Since you may need additional space particularly if running a full node, an external hard drive or flash drive may be a good addition to this project. Actually want to try mining bitcoins? Check out our Privacy Policy. After the coin is generated, the wallet is decrypted, the key is imported, and the coin is returned in the response. You can also run a full node. Here are what two of the same routes might look like:. In the core of our HTML, we have a loop that loops through our public array of coins. But why do miners invest in expensive computing hardware and race each other to solve blocks? Here is a visual so you have a better idea: Think back to what we had in our main.

Most, if not all, of the previous tutorials include videos in case you have trouble getting things set up. In any fair and comprehensive comparison of resource costs between the two systems, Bitcoin is likely to compare very favorably! Certainly the possibily of enabling such exciting and potentially transformative technologies is worth the energy cost… particularly given the synergy between smart devices and power saving through increased efficiency. Privacy and Cookies Next altcoin to the moon precious metals cryptocurrency are tiny data files stored in your web browser when you visit a website. We need to define our routes and import any remaining Angular dependencies. The magic value is the information about the actual network. TechWiserviews. The decryption process requires the same nonce used in encryption, so as long as we know the erc20 myetherwallet ico send mining ether coin of the nonce, we can extract it from the prefix. Sign in with social media. Given a bitmain minerlink cryptocurrency exchange in hong kong in the query parameters, we check to see if it is valid and return a boolean response back to the user. To be real: The problem with this is that Go is a nightmare when it comes to playing nice with the Angular router. If you completed the tutorial, I applaud you as it was quite lengthy. The above endpoint behaves a bit different.
Just comment the line that refers to the Angular front-end and execute:. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards. We find ourself in a tricky position. There are a few package dependencies that we need to obtain to make our lives just a little easier. It is more important in a frontend, but can still be valuable elsewhere. Mining Difficulty If only 21 million Bitcoins will ever be created, why has the issuance of Bitcoin not accelerated with the rising power of mining hardware? Consult local counsel for further assistance in determining whether Bitcoin mining is legal and the tax implications of doing the activity. Privacy and Cookies Cookies are tiny data files stored in your web browser when you visit a website. Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or commodity. The wallet will be encrypted, however, if someone has your encrypted wallet file, they could potentially break into it with the correct skills and willpower. Once you run Geth, you should see a notification that Block synchronization has begun. Each of the pages will listen to this emitter and respond appropriately as things change. Toggle navigation The Polyglot Developer. You may wish to create just a Bitcoin wallet. Use cURL or a tool like Postman to hit each of the endpoints. Rating is available when the video has been rented. If there are no conflicts e. DIY Perks 4,, views. Step 4:

Once the pool finds a block you get a payout based on the percent of hash rate contributed to the pool. Choose your language. With the Angular project built and bundled as a rice. Honest Miner Majority Secures the Network To successfully attack the Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain. AddOhms 7 - Duration: Destructive operations should be done with care. We need to change some settings before we place it in the Raspberry Pi Zero. Create an account. Red would be taking a big risk by sending any goods to Green before the transaction is confirmed. After you connect, execute the following command:. Enterprising coders soon discovered they could get more hashing power from graphic cards and wrote mining software to allow this. Smart, interconnected devices offer great promise in terms of self-reporting of problems and supply shortages, even the self-calibration and the self-diagnosis of problems. It could also make mining that much more competitive that your profits remain the same. Tinkernut Labs.
Support This Site If you found this developer resource helpful, please consider supporting it through the following options: What is very important to us is the routes array:. This is where Miners enter the picture. Remember to choose the correct disk, do not just copy and paste my commands otherwise you might destroy something important. Get YouTube without the ads. Here are what two of the same routes might look like:. Creating transactions in an endpoint is just as complicated as the underlying function code that we previously saw. Here, you may want to use an external drive since the full Ethereum blockchain is pretty large. Locate the label for your external storage media, for example sda1. What cryptocurrency to buy now bitcoin casino bonus Footer. There is more to the wallet code, but our focus for now is on the encryption and decryption side of things. Skip navigation.
Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. The point of hardware wallets is that they hold how to buy coins in bittrex poloniex sign in private unable to add payment gateway in coinbase coinbase and the law, never expose the private keys, and operate in an offline environment. You can also run a full node. Any such advice should be sought independently of visiting Buy Bitcoin Worldwide. Make sure that the above command is executed within your Go project. Pools are groups of cooperating miners who agree to share block rewards in proportion to their contributed mining power. I own several Raspberry Pi Zero and thought it would be a perfect opportunity to take what I know about Raspberry Pi and Golang to create a wallet for a fraction of the price as the industry leading wallets. Consider one of the popular alternatives, real estate: We can validate it to take the guess work out of things:. While such low-powered mining devices earn very little income, even a few hundred Satoshis opens the door to automated micro-payments…. Instead we want to bundle the Angular application, cross-compile the binary, and enjoy a single application file with no dependencies. Also notice the hosts that were initialized. They have to use their computing power to generate the equid cryptocurrency dao crypto bitcoins. This pie chart displays the current distribution of total mining power by pools: To go everything I just said, if you really want to retrieve everything, you could create a Dump function:. Our Decrypt function takes a slice of byte which we can decrypt to plaintext using a passphrase. What is truly important to us is the SignedTx property in the Transaction data structure.
For example, BitPay has a popular explorer for Bitcoin. Block Reward Halving Satoshi designed Bitcoin such that the block reward, which miners automatically receive for solving a block, is halved every , blocks or roughly 4 years. Nic Raboy is an advocate of modern web and mobile development technologies. You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations? Notice that the setup of our decryption function is nearly the same as our encryption function. You can create a Litecoin wallet on a Raspberry Pi as well. Economies of scale have thus led to the concentration of mining power into fewer hands than originally intended. Related Tutorials. From the Angular CLI, execute the following command:. Get in touch. This allows us to consolidate our code in a singleton type instance to be used within every component. This video is unavailable. Total cost: Please try again later. Learn more. Just add it to a build.

If we wish to backup our wallet, in other words download the encrypted file, we could create a function called backup like this:. Notice that the password is blanked out and the status is emitted to anything that is listening. Not just of electricity, but of money, time and human resources! In theory we have an empty wallet, so it would make sense to create or import a coin. Instead of Geth, you may use Pyeth instead. For this service, miners are rewarded with newly-created Bitcoins and transaction fees. Which blockchain prevails? So, it might be cool to setup a miner on your Android phone to see how it works. There are now two competing versions of the blockchain! Most exchanges require 3 confirmations for deposits. This will show you where your USB stick is mounted. Other distributions might work, but I have no idea how to enable ethernet emulation. This will create a full node and wallet. There are many examples of data centres re-using heat for example, IBM Switzerland warming a public swimming pool which Bitcoin miners could follow. This request along with all other requests will contain a passphrase that is saved in our service after authenticating.
Why not spread the word to ig cryptocurrencies investment club cryptocurrency friends? Jordan Tuwiner Last updated February 8, So do we Cancel Unsubscribe. If all the fields are filled and the user executes the create function, the data is sent to our API and the transaction is returned. Show Footer. Once the pool finds a block you month mining contract questions about genesis mining a payout based on the percent of hash rate contributed to the pool. There are two major camps which object to Bitcoin mining due to its electrical cost: Think back to what we had in our main. Now that we can create coins, we need to be able to store them in a wallet as ciphertext. The create function will issue a POST request where the results can be subscribed to.
Continuing the theme of Bitcoin integration with household and industrial devices, this is the precise business model of potentially-disruptive Bitcoin company, Our Decrypt function takes a slice of byte which we can decrypt to plaintext using a passphrase. Confirm Password. Acceptable blocks include a solution to a Proof of Work computational problem, known as a hash. The likely outcome is a disastrous crash which sets the regional economy back by years. This short documentary explores the inner workings of a Chinese mining operation. For example each of the screens will call something from our service. If you wish to broadcast the transaction, copy and paste the signed output and take it to a blockchain explorer to broadcast. What we care about is the form that is bound to our input variable and the button that calls the unlock method. After the coin is generated, the wallet is decrypted, the key is imported, and the coin is returned in the response. What is Bitcoin mining actually doing? The Raspberry Pi Zero is now a little more hardened than when it started. Sign in to add this to Watch Later. Jordan Tuwiner Last updated February 8,
Creating transactions in an endpoint is just as complicated as the underlying function code that we previously saw. Enterprising coders soon discovered they could get more hashing power from graphic cards and wrote mining software to allow. If we wanted to dump the wallet data in plaintext, we could create a dump function like this:. Log In! Finally, it must be noted that efficiency of Bitcoin mining is constantly improving, so less power is used to provide more cryptographic security. Autoplay When autoplay is enabled, a suggested video will automatically play. Mining Difficulty If only 21 million Bitcoins will ever be created, why bitcoin casino with free play mode what time of day is bitcoin most volatile the issuance of Bitcoin not accelerated with the rising power of mining hardware? So do we For this service, miners are rewarded with newly-created Bitcoins and transaction fees.
Transactions are tricky and it is in my opinion the most difficult part about cryptocurrencies. Most people should NOT mine bitcoins today. You're subscribed! Since you may need additional space particularly if running a full node, an external hard drive or flash drive may be a good addition to this project. There is mining software available for Mac, Windows, and Linux. Which blockchain prevails? Issuance is regulated by Difficulty, an algorithm which adjusts the difficulty of the Proof of Work problem in accordance with how quickly blocks are solved within a certain timeframe roughly every 2 weeks or blocks. Now that we can interact with our wallet and coins safely, we should when was the bitcoin fork announce how much bitcoin does china own worry about creating and signing transactions that can later be broadcasted to the blockchain. Whether it was the Roman Empire debasing its coinage or modern central banks inflating the supply of fiat money… The end result of currency debasement is, tragically and invariably, economic crisis. This simplified illustration is helpful to explanation: This file should look like the following:. The good news is that, according to the somewhat out-dated calculations of a New York-based miner, mining rigs offer considerable cost savings over standard electric heaters. Bitcoin is different. The key must be of a certain byte length which is more trouble than it is worth to try to match in a passphrase. Nowadays all serious Bitcoin mining is performed on ASICs, usually in thermally-regulated data-centers with access to low-cost electricity. As Bitcoin could easily replace PayPal, credit card companies, how to become a certified bitcoin vendor can you have less than 1 bitcoin and the bureaucrats who regulate them all, it begs the question: Please try again later.
With Raspbian or another compatible OS installed, boot up your Pi. In theory we have an empty wallet, so it would make sense to create or import a coin. This feature is not available right now. Cookies are tiny data files stored in your web browser when you visit a website. Remember the CORS that we set up? As Namecoin serves a decentralised DNS Domain Name Server , the effect is to bring greater resilience and censorship-resistance to the internet. There is mining software available for Mac, Windows, and Linux. It also benefits the side-chain by backing and securing it cryptographically with the huge power of the Bitcoin mining industry. But why do miners invest in expensive computing hardware and race each other to solve blocks? To achieve it, an attacker needs to own mining hardware than all other honest miners. Because swap files add additional memory, you may avoid a Bitcoin core crash by adding swap. The central bank can issue new units of money ay anytime based on what they think will improve the economy. The answer is somewhat complex and requires a solid understanding of the above mining process: Locate the label for your external storage media, for example sda1. Facebook Twitter Not now. Remember, you probably want to remove the WIF string from the response. Given a passphrase and a wallet that contains data, we can call the Encrypt function:. With the core encryption and decryption functionality implemented, we need to take it a step further and take it to disk. Now that we can interact with our wallet and coins safely, we should probably worry about creating and signing transactions that can later be broadcasted to the blockchain. The xpubkey value is the byte prefix for public keys and the xprivatekey value is the byte prefix for private keys.
Before we jump into each of the functions, notice our constructor method. The initial route is our unlock screen, but each of the other components have a path as well. We are using a sub-router for our API and loading our Angular application for the root route. Toggle navigation The Polyglot Developer. A key must exist in the query parameters and it will be used to create a wallet using the previous Create method. The create function will issue a POST request where the results can be subscribed to. As for office or home use, an additional source of passive Bitcoin income may serve to make cozy indoor temperatures a more affordable proposition. Also in the software you tell the pool which Bitcoin address payouts should be sent to. Notice that we have a Wallet data structure that maintains a slice of the Coin data structure that we had created previously. Green sends 1 bitcoin to Red. If other full nodes agree the block is valid, the new block is added to the blockchain and the entire process begins afresh. The request requires that a key exists as a query parameter and that symbol exists in the request body. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. To make your flash drive automount, open and edit the fstab file:. The plan is to have a wallet with any number of coins. Getting the idea yet? What we care about is the form that is bound to our input variable and the button that calls the unlock method. While not lengthy, transactions are probably the most complicated part of this tutorial.
The initial route is our unlock screen, but each of the other components have a path as. How do mining pools help? In your final application you may want to make it more difficult to destroy a wallet, or not at all. This pie chart displays the current distribution of total mining power by pools: Moe Long is an editor, writer, and tech buff with a gsx vs coinbase reddit donation coinbase appreciation for Linux, Raspberry Pis, and retro gaming. Wait for at least one. TechWiserviews. The key must be of a certain byte length which is more trouble than it is worth to try to match in a passphrase. This means that we need to use a sub-router to distinguish what is API and ethereum hardware mining comparison bitcoin gekko is front-end. Support This Site If you found this developer resource helpful, please consider supporting it through the following options: Nic writes about his development experiences related to making web and mobile development easier to understand. Whether it was the Roman Empire debasing its coinage or modern central banks inflating the supply of fiat money…. Just like that we can generate wallet information for coins. You actually CAN mine bitcoins on any Android device. Nowadays all serious Bitcoin mining is performed on ASICs, usually in thermally-regulated data-centers with access to low-cost electricity. Remember, if you want a truly secure hardware wallet, the WIF information should never be exposed or leave the Raspberry Pi. Mining Difficulty If only 21 million Bitcoins will ever be created, why has the issuance of Bitcoin not accelerated with the rising power of mining hardware? It will look something like the following animated image. We have a parent component that controls things at a higher level.
Source ieee. While such low-powered mining devices earn very little income, even a few hundred Satoshis opens the door to automated micro-payments…. Our website is made possible by displaying online advertisements to our visitors. If you completed the tutorial, I applaud you as it was do you get paid in satoshi vs bitcoin buy bitcoin anonymously legit lengthy. When the page initializes, the ngOnInit method is called which makes a request bitcoin cash electrum reddit claim bitcoin mining rig how to get our addresses. Other distributions might work, but I have no idea how to enable ethernet emulation. Since you may need additional space particularly if running a full node, an external hard drive or flash drive may be a good addition to this project. ASIC mining chip architecutre and processes are under continuous development, with lucrative rewards on offer to those who bring the latest and greatest innovations to market. Despite its weakness, when compared with mid-range to high-end graphics processing units GPUs computing power, the Raspberry Pi is capable of cryptocurrency mining. Email address. Once you run Geth, you should see a notification that Block synchronization has begun. Given the sluggish global economy, new and promising industries should be celebrated! While not lengthy, transactions are probably the most complicated part of this tutorial. AddOhms 7 - Duration: Miners, like full nodes, maintain a complete copy of the blockchain and monitor the network for newly-announced transactions. Here is a visual so you have a better idea: Using how to read bitcoin transactions bitcoin trump administration source and destination public addresses we can create transaction output. Do you understand what bitcoin scash twitter what crypto currency is mark cuban backing need to do to start? We need to maintain a healthy balance between nature and technology. For those laboring under restrictive capital controls, mining therefore represents an excellent if unconventional solution.
This pie chart displays the current distribution of total mining power by pools: Given the sluggish global economy, new and promising industries should be celebrated! Nic Raboy is an advocate of modern web and mobile development technologies. Check out our Privacy Policy. Bitcoin mining is the backbone of the Bitcoin network. Most Bitcoin mining is specialized and the warehouses look something like this: Choose your language. The point of hardware wallets is that they hold encrypted private keys, never expose the private keys, and operate in an offline environment. Confirm Password. Most people should NOT mine bitcoins today. The empty wallet will be encoded and sent in the response. During the make -j4 step , this might take several minutes. Given a particular network, we can generate a new private key and store it in wallet import format WIF. When the CreateWalletEndpoint function is called, we set the response type and we check the request for query parameters. AddOhms , views. This request along with all other requests will contain a passphrase that is saved in our service after authenticating. But, there are some problems with their theories as we'll discuss. Remember, if you want a truly secure hardware wallet, the WIF information should never be exposed or leave the Raspberry Pi.
Traditional currencies--like the dollar or euro--are issued by central banks. Not only are we planning to create a transaction, but we need something to store it in. The file should have no extension and no data. As with the Bitcoin installation, the make step will take a few minutes. You may wish to create just a Bitcoin wallet. Change the hostname and any other settings you feel to be appropriate. Download the latest Raspbian Lite image from the Raspberry Pi website. In the encryption function, we are creating a new AES cipher from our hashed passphrase. Miners, like full nodes, maintain a complete copy of the blockchain and monitor the network for newly-announced transactions. The only downside for home miners is that mining rigs are often noisy and un-anaesthetically-pleasing devices. Keep an eye on your inbox for a monthly roundup which includes all of the top content on Electromaker. As a result, they tend to be sequestered in the basement or garage for the sake of domestic harmony. To cross-compile for the Raspberry Pi, we can do so without ever breaking a sweat. With Raspbian or another compatible OS installed, boot up your Pi. The more computing power a miner controls, the higher their hashrate and the greater their odds of solving the current block. Get YouTube without the ads. The issuance rate is set in the code, so miners cannot cheat the system or create bitcoins out of thin air.
Is Bitcoin mining just free money? This short documentary explores the inner workings of a Chinese mining operation. Panels, Workshops, and More. If we want to get the addresses that exist in our wallet, bitcoin qt par1 parameter bull bitcoin can call the GetAddresses function:. Could you do better? I am a developer and Bitcoin enthusiast and not a cryptocurrency or cryptography expert. TechMagnetviews. To accomplish this, make a mount point for your USB stick:. Power companies paid their customers to use more power so that the energy could be safely dispersed. This leaves us with little opportunity for communicating with the Raspberry Pi Zero at all. However, there is the following statement:. Remember, we are not receiving any sensitive data nor are we trying to display it on the screen. How to link bittrex and coinbase wallet cost of 1 bitcoin share this video? This will show you where your USB stick is mounted. Here is the script I use:. You may have heard that Bitcoin transactions are irreversible, so why is it bitcoin arrives in 7 days brave coin ico to await several confirmations? It is a hassle to have to sign into the Raspberry Pi via SSH every time we plug it in to be able to access our wallet. The more locked down your Raspberry Pi, the better for your hardware wallet.
Depending on how your Pi is configured, you may need to change some information. Here are what two of the same routes might look like:. Create Your Account. Once the pool finds a block you get a payout based on the percent of hash rate contributed to the pool. Linus Tech Tips 1,, views. To accomplish this, install the necessary dependencies:. The above endpoint behaves a bit different. If we want to get the addresses that exist in our wallet, we can call the GetAddresses function:. Green sends 1 bitcoin to Red. Red may now consider sending the goods to Green. Cookie Policy. To go everything I just said, if you really want to retrieve everything, you could create a Dump function:. Also in the software you tell the pool which Bitcoin address payouts should be sent to.