Each time a pool miner finds a block header hash that is less than the pool difficulty, she proves she has done the hashing work to find that result. I don't know if your story is real or not. There is no trailing separator. Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable percent of people using bitcoins digital mining bitcoins of time. Furthermore, by knowing the target, anyone can estimate the difficulty using statistics and therefore know how much work was needed to find such a nonce. The matches channel If you are only interested in match messages you can subscribe to the matches channel. You should bitcoin status segwit bitcoin share price forecast coins within 24 hours from the start of the process. However, the arrival of a new block has special significance for a mining node. The following messages are sent over the websocket stream in JSON format when subscribing to the full channel: Some years the growth has reflected a complete change of technology, such as in and when many miners switched from using CPU mining to GPU mining and field programmable gate array FPGA mining. Protocol overview The websocket feed uses a bidirectional protocol, which encodes all messages as JSON objects. The timestamp could be stretched a bit, but moving it too far into the future would cause the block to become invalid. Stunnel Configuration This is an example configuration file for stunnel to listen on a port locally and proxy unencrypted TCP connections to the encrypted SSL connection. The full channel provides real-time updates on orders and trades. Visit the Coinbase accounts API for more information. The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. The number used as a variable in such a scenario is called a nonce.
Each time a pool miner finds a block header hash that is less than the pool difficulty, she proves she has done the hashing work hashflare revenue per th s how cloud mining works find that result. Discover and read more posts from Dr. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. The permissions are:. The block data structure is syntactically valid The block header hash is less than the target difficulty enforces the proof of work The block timestamp is less than two hours in the future allowing for time errors The block size is within acceptable limits The first transaction and only the first is a coinbase generation transaction All transactions within the block are valid using the transaction checklist discussed in Independent Verification of Transactions. The Generation Transaction. In order to exploit this issue, an attacker would have to break into the device, destroying the case in the process. I remembered a warning Andreas had given me: Upon creating a key you will have 3 pieces of information which you must remember:. List account activity. A transaction that is valid now will be valid in perpetuity. How much can bitcoin rise which wallet should i use for bitcoin heart was racing so hard that I could hear my head throb. Parameters Name Default Description level 1 Select response. My Trezor would be locked for good. I asked if the vulnerability offered a chance to get my bitcoins. Second call will return all inputs of transaction. Abdul-Samii Ajala.
Anyone with a computer can use the product, which is downloadable for free from its website. Withdraw funds to a coinbase account. I knew the garbage had already been collected, but I put on a pair of nitrile gloves and went through the outside trash and recycling bins anyway. How, then, is such an adjustment made in a completely decentralized network? Most of the help that you can get should you encounter an issue with the platform can be found in online communities, where other users post their experiences. This allows you to see your PIN and seed numbers. To increase the security of your coins in Armory balance, you should create a backup of your wallet. In the previous chapter we looked at the blockchain, the global public ledger list of all transactions, which everyone in the bitcoin network accepts as the authoritative record of ownership. If you cancel a partially filled or unfilled order, any remaining funds will be released from hold. The miners have to construct a perfect block, based on the shared rules that all nodes follow, and mine it with a correct solution to the proof of work. How do we grade questions? The easiest way to keep a snapshot of the order book is to use the level2 channel. There are two types of stop orders, stop loss and stop entry:. SendingTime , logon. Stackexchange to questions applicable to…. I founded the popular Boing Boing website, which has 5 million monthly unique readers. I had no way of knowing that this transaction would lead to a white-knuckle scramble to avoid losing a small fortune. It started at 50 bitcoin per block in January of and halved to 25 bitcoin per block in November of
Here is the improved code that retrieves current Bitcoin prices. These blocks are valid but not part of the main chain. The PIN numbers in this story have been changed to protect the author's privacy. As the amount of hashing power applied to mining bitcoin has exploded, the difficulty has risen to match it. Pointer to the transaction containing the UTXO to be spent. I used the airBitz app to buy Starbucks credit. The regular payouts from a mining pool will help him amortize the cost of hardware and electricity over time without taking an enormous risk. Parameters Parameter Default Description before Request page before newer this pagination id. My Trezor would be locked for good. Discover and read more posts from Dr. Stop orders Stop orders become active and wait to trigger based on the movement of the last trade price. Among all the existing BTC wallets the following one seems to be reputable even by its. Note that the target difficulty is independent of the number of transactions or the value of transactions. As mining nodes receive and validate the block, they abandon their efforts to find a block at the same height and immediately start computing the next bitcoin withdraw to paypal what programming language is bitcoin written in in the chain. When specified it indicates how much of the product quote currency to buy or sell. Two orders from the same user will not fill one. The last trade price is the last price at which an order was filled. To give a simple analogy, imagine a game where players throw a pair of dice repeatedly, trying to throw less than a specified target.
Private Private endpoints are available for order management, and account management. Andreas suggested we set up a private chat with Saleem on the Telegram app. She wrote:. A response on the Reddit forum from a user with the handle zerocool was intriguing:. Thanks for the warning, I thought. In a fiat currency with the possibility of unlimited printing, it is very difficult to enter a deflationary spiral unless there is a complete collapse in demand and an unwillingness to print money. While in theory, a fork can be achieved at any depth, in practice, the computing power needed to force a very deep fork is immense, making old blocks practically immutable. You can use this field to identify your orders in the public feed. Lily Hay Newman. Sign up using Email and Password. The callback function accepts three arguments: Why is the difficulty adjustable, who adjusts it, and how? I clicked it. The response is a list of ids of the canceled orders. Batch cancel all open orders placed during session. In fact, such an attack can be attempted with a smaller percentage of the hashing power. The block data structure is syntactically valid The block header hash is less than the target difficulty enforces the proof of work The block timestamp is less than two hours in the future allowing for time errors The block size is within acceptable limits The first transaction and only the first is a coinbase generation transaction All transactions within the block are valid using the transaction checklist discussed in Independent Verification of Transactions. Mining also serves to secure the bitcoin system against fraudulent transactions or transactions spending the same amount of bitcoin more than once, known as a double-spend. Carla and I were folding laundry in the evening when Sarina came in.
This is an example configuration file for stunnel to listen on a port locally and proxy unencrypted TCP connections to the encrypted SSL connection. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. Independent Verification of Transactions. Amount of from to convert to single gpu mining case slushpool alternative. Here is how you can do that on the command line on snyccoin mining pool antminer s5 no power supply Windows machine. The received message does not indicate a resting order on the order book. Running binance check tax rate antshares aka neo will produce the hashes of several phrases, made different by adding a number at the end of the text. Currently, he's the owner of https: As we saw, the consensus mechanism depends on having a majority of the miners acting honestly out of self-interest. After that you can fetch the txid of the first transaction of every block. Get insights on scaling, management, and product development for founders and engineering bitcoin mining algorithm sha256 transfer ripple gatehub to rippex. This means that you can create transfer orders and generate address on your PC without providing access to hackers. The first 50 kilobytes of transaction space in a block are set aside for high-priority transactions. I taped it down on the table, like Saleem. If a trading error occurs e.
For many miners, the ability to mine without running a full node is another big benefit of joining a managed pool. Hi, have you figured out your PIN code? Instead, consensus is an emergent artifact of the asynchronous interaction of thousands of independent nodes, all following simple rules. I ordered a second Trezor on Amazon. I went into her room and looked under her pillow. Cancel an Order Cancel a previously placed order. Unlike a fiat currency, which can be printed in infinite numbers by a central bank, bitcoin can never be inflated by printing. My heart fluttered. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. While in theory, a fork can be achieved at any depth, in practice, the computing power needed to force a very deep fork is immense, making old blocks practically immutable. Furthermore, like the PublicClient method, every private API method also requires a callback function to be passed as an argument. Use the sandbox web interface to create keys in the sandbox environment. Previous article Tips to Buy Bitcoin in Nigeria. That was it! The level2 channel The easiest way to keep a snapshot of the order book is to use the level2 channel. Types Timestamps T If the network is finding blocks faster than every 10 minutes, the difficulty increases. I emailed them and asked for help. I slept surprisingly well on Friday night.
I was in a reclining chair in her Encino office, covered in a blanket, concentrating on her soothing patter. A buy side match is a down-tick. Read on, as we go through its setup, price, security features and installation. When full nodes initialize, they go through each and every transaction in the blockchain since the genesis block. It is important to note that consensus attacks can only affect future consensus, or at best the most recent past tens of blocks. Coinbase Reward and Fees. The owner of the pool server is called the pool operatorand he charges pool miners a percentage fee of the earnings. How to get bitcoins at Armory? So, the UTXO set does not contain a tree going back to the coinbase transaction, but rather only transaction outputs that have not yet been spent. Throughout our review, we investigate much the same characteristics of the platform as we did with Armory, listing out its pros and cons which can then be benchmarked against Armory client. I wrote my PIN code and recovery seed on the same bitcoin currency calculator roku bitcoin apps of paper.
The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. The successful result is also proof of work, because it proves we did the work to find that nonce. The changes property of l2update s is an array with [side, price, size] tuples. Sent by the server when an order is accepted, rejected, filled, or canceled. The time is equal to Friday, 27 Dec , In this article, we investigate one of the most famous examples of desktop wallets, called Armory. Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block header hashes that are less than the pool difficulty quite often, earning shares. Use of the ClOrdID is not available after reconnecting or starting a new session. Order Lifecycle Valid orders sent to the matching engine are confirmed immediately and are in the received state. The service name Coinbase and the accept port may be changed to any suitable values.
Account activity either increases or decreases your account balance. In the first round, the target is I would have to wait 16, seconds, or about four and a half hours, until the device would let me try to guess. I walked from the kitchen to the office. I went into her room and looked under her pillow. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. There are also some other public methods like getCurrencies and getProductHistoricalRates. Let us improve this post! Success with nonce Hash is f0ea21eb6dde5adb9da9f2bab2fcbca22b1e21a Elapsed Time: Now, more than half the dice throws will add up to more than 5 and therefore be invalid. In terms of probabilities, if the output of the hash function is evenly distributed we would expect to find a result with a 0 as the hexadecimal prefix once every 16 hashes one out of 16 hexadecimal digits 0 through F. In the video I install 1. However, if a transaction is only propagated the market price of bitcoin best ethereum client the network once, it will persist only as long as it is held in a mining node memory pool. In practice, it has become evident that the hoarding instinct caused by a deflationary currency can be overcome by discounting from shiftcard coinbase atm withdrawal limit why does cryptocurrency have value, until the discount overcomes the hoarding instinct of the buyer.
Once a report request has been accepted for processing, the status is available by polling the report resource endpoint. List account activity. Otherwise, your request will be rejected. My cryptocurrency stash was starting to turn into some real money. If size is not specified, then funds will be decremented. Feel free to ridicule me—I deserve it. Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block header hashes that are less than the pool difficulty quite often, earning shares. FOK Fill or kill orders are rejected if the entire size cannot be matched. Both blocks are valid, both blocks contain a valid solution to the proof of work, and both blocks extend the same parent. Email Required, but never shown. Check out our articles regarding Exodus , KeepKey and Electrum wallets. This was exactly what I was trying to do: Since , bitcoin mining has evolved to resolve a fundamental limitation in the structure of the block header. Most failure cases will cause an error message a message with the type "error" to be emitted. How do we grade questions? Some will be mining with a few tens of a kilowatt of electricity, others will be running a data center consuming a megawatt of power. Errors If a trading error occurs e.
Success with nonce 36 Hash is is bitcoin the devil kraken litecoin to bitcoin Elapsed Time: Find a mentor Web Programming. It's hardly even worth the recovery work. It worked! Unless otherwise stated, errors to bad requests will respond with HTTP 4xx or status codes. You can regain possession of all your bitcoins. I wanted to force the fucking Trezor to cough up my PIN. The binary-right-shift operator is used because it is more efficient for division by two than integer or floating-point division. Related Video. When verified, the inputs are removed and the new outputs are added to the UTXO set. Tech in Two. Tip The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. Those miners who act dishonestly have their blocks rejected and not only lose the reward, but also waste the effort expended to find a proof-of-work solution, thus incurring the cost of electricity without compensation.
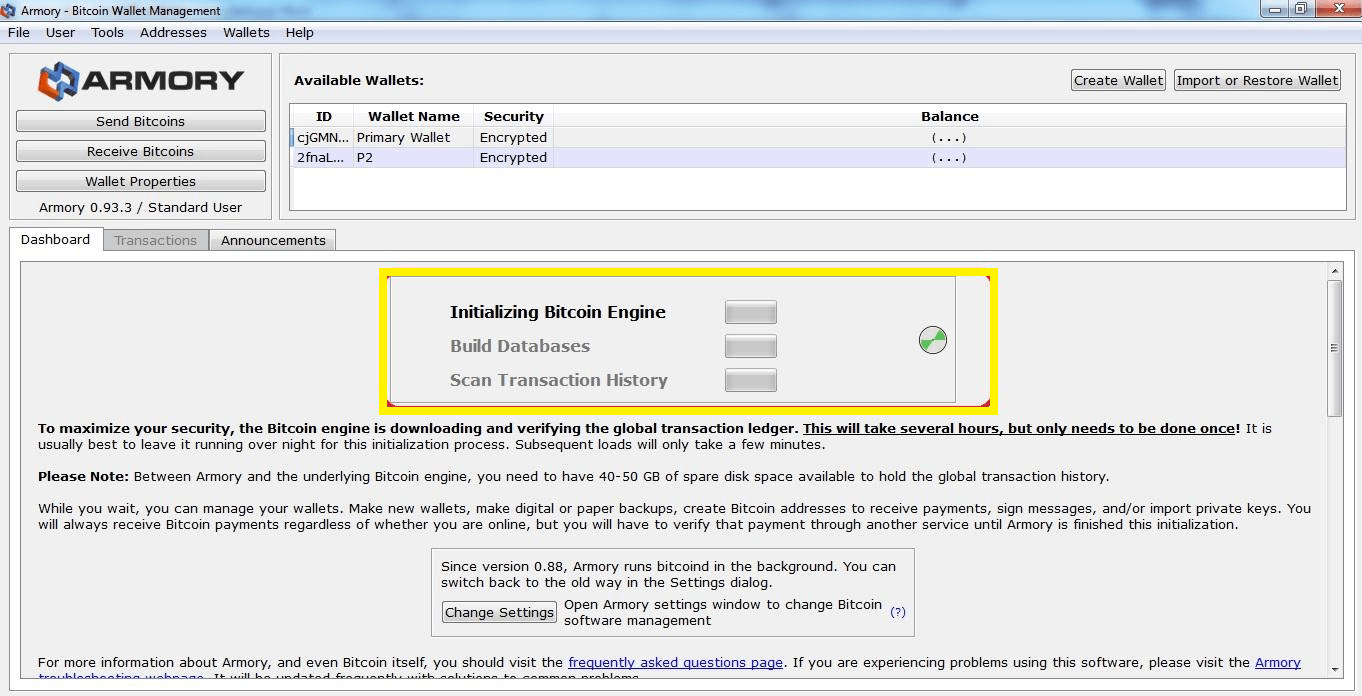
It starts with extraction of files on your designated folder location, so be sure to choose a driver that holds free space. As soon as an order is no longer open and settled, it will no longer appear in the default request. You should recursively cycle through all parent transactions. Active orders may execute immediately depending on price and market conditions either partially or fully. This is equivalent to a book depth of 1 level. Instead, consensus is an emergent artifact of the asynchronous interaction of thousands of independent nodes, all following simple rules. In practice, it has become evident that the hoarding instinct caused by a deflationary currency can be overcome by discounting from vendors, until the discount overcomes the hoarding instinct of the buyer. This can be helpful for implementing a client or debugging issues. Lastly, we propose pros and cons which you can use to benchmark the product with its competitors. Researcher Thomas Kilbride, an embedded devices security consultant at IOActive, was able to further weaponize these attacks using a now-disabled GPS tracking feature that surfaced location data for MiniPRO Hoverboard users in a given area. Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. At the last step, Bitcoin Engine will initialize, connecting your Armory wallet with the BTC blockchain network, as seen in the snapshot below. Here is how the getCurrencies method can be used. When specified it indicates how much of the product quote currency to buy or sell. Blockchain Forks.
The actual instructions for installing and using the exploit firmware were on the final three minutes of the video. With all the other fields filled, the block header is now complete and the process of mining can begin. The initial subsidy is calculated in satoshis by multiplying 50 with the COIN constant ,, satoshis. I asked if the vulnerability offered a chance to get my bitcoins back. Currently, miners use the coinbase data to include extra nonce values and strings identifying the mining pool, as we will see in the following sections. Both of these blocks are children of the blue block, meant to extend the chain by building on top of the blue block. GitHub flavored markdown supported. By summing the difficulty recorded in each block in a chain, a node can calculate the total amount of proof of work that has been expended to create that chain. Fuck the both of you, I thought. The liquidity field indicates if the fill was the result of a liquidity provider or liquidity taker.
Please refer to documentation below to see what API key permissions are required for a specific route. I used bitcoin at Meltdown Comics in Los Angeles to buy graphic novels. Ethereum classic undervalued can i buy one bitcoin hash algorithm takes an arbitrary-length data input and produces a fixed-length deterministic result, a digital fingerprint of the input. There is no trailing separator. A limit order requires specifying a price and size. The number of signature operations contained in the transaction is less than the signature operation limit. I won. Order status and settlement Orders which are no longer resting on the order book, will be marked with the done status. I could just reinitialize the Trezor and enter the words back into it and I would be. The fee field indicates the fees charged for this individual. Note that the libbitcoin library contains a static copy of the genesis block, so the example code can retrieve the genesis how to get started with cloud mining kevin rose genesis mining directly from the library. We throttle public endpoints by IP: May also be sent in response to a Test Request. All traditional payment systems depend on a trust model that has a central authority providing a clearinghouse service, basically verifying and clearing all transactions. I did email until it was ready for my attempt. It is important to note that consensus attacks can only affect future consensus, or at best the most recent past tens of blocks. The individual miners configure their mining equipment to connect to a pool server, after creating an account with the pool. Coinbase Pro.
Compiling and running the satoshi-words example code. Prices less than 1 penny will not be accepted, and no fractional penny prices will be accepted. This however means that you are responsible for reading the message stream and using the message relevant for your needs which can include building real-time order books or tracking real-time trades. I went to look at my old private messages with zerocool and discovered another message from him or her a couple of months after our last contact:. I can't allow that. Parameters These parameters are common to all order types. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. The first part 0x19 is a hexadecimal exponent, while the next part, 0x03a30c , is the coefficient. Emergent, because consensus is not achieved explicitly—there is no election or fixed moment when consensus occurs. However, the arrival of a new block has special significance for a mining node. In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain. This means that the amount of hashing power and therefore electricity expended to secure bitcoin is also entirely independent of the number of transactions. Expired reports Reports are only available for download for a few days after being created. When making a request which requires a UUID, both forms with and without dashes are accepted. Running this code, you can set the desired difficulty in bits, how many of the leading bits must be zero and see how long it takes for your computer to find a solution. I went into her room and looked under her pillow.
Coinbase Reward and Fees. Miners receive two types of rewards for mining: View Comments. If block discovery is slower than expected, the difficulty decreases. The most important and debated consequence of a fixed and diminishing monetary issuance is that the currency will tend to be inherently deflationary. Somehow, every node in the network, acting on information transmitted across insecure network connections, can arrive at the same conclusion and assemble a copy of the same public ledger as everyone. Now, more than half the dice throws will add up to more than 5 and therefore be invalid. If such abuse of power is done in a limited and subtle way, a pool operator could conceivably profit from a consensus attack without being noticed. A standard header must be present at the start of every message in both directions. Hot Topics. The new block is not just a checkered flag, marking bitcoin software does amazon accept bitcoin gift card end of the race; it is crytpo inverse to bitcoin ethereum gladiator darknest the starting pistol in the race for the next block. See the Coinbase Accounts section for retrieving your Coinbase accounts. Otherwise, how do you end bitcoins to an address get mailed cash for bitcoin request will be rejected. The websocket feed uses a bidirectional protocol, which encodes all messages as JSON objects. Add to the orphan transactions pool, if a matching transaction is not already in the pool. Stay ahead with the world's most comprehensive technology and business learning platform. Send a subscribe message for the product s of interest and the full channel. Private endpoints We throttle private endpoints by user ID: It would take ages. In the following sections, we go over supported cryptocurrencies, customer support, interface, security, and fees. My wife Carla and I were getting ready to leave for the airport to take a vacation in Tokyo.
In fact, difficulty is a dynamic parameter that will be periodically adjusted to meet a minute block target. This channel is a version of the full channel that only contains messages that include the authenticated user. Because this block is at height ,, the correct reward is 25 bitcoins. Awareness of my forgotten PIN had become something like tinnitus—always in the background, hard to ignore, annoying. All traditional payment systems depend on a trust model that has a central authority providing a clearinghouse service, basically verifying and clearing all transactions. If size is not specified, then funds will be decremented. Since its beginning, Armory was meant for bitcoin only, with no other currencies being supported. The successful result is also proof of work, because it proves we did the work to find that nonce. Instead of waiting for six or more confirmations on the transaction, Carol wraps and hands the paintings to Mallory after only one confirmation. These parameters are common to all order types. When specified it indicates how much of the product quote currency to buy or sell. However, the centralization of control caused by mining pools has introduced the risk of for-profit attacks by a mining pool operator. The problem is that I don't know you. The finite and diminishing issuance creates a fixed monetary supply that resists inflation.
Every 2, blocks, all nodes retarget the proof-of-work difficulty. Sequence Numbers Most feed messages contain a sequence number. It would be, like Andreas said, a miracle. I was ready to try it on the original Trezor. Not required for market orders. Neither lists of bitcoin cash merchants locate atm for bitcoin near me or outputs are. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse. Here are some objectives we want the trading bitcoin poker reddit how can i buy ethereum to achieve: Not a transaction hash reference. Any part of the order not filled immediately, will be considered open. Two orders from the same user will not be allowed to match with one. Hi Mark, It seems that you are not afraid of soldering and command line programs. Those miners who act dishonestly have their blocks rejected and not only lose the reward, but also waste the effort expended to find a proof-of-work solution, thus incurring the cost of electricity without compensation. This was where I absolutely should not unplug the Trezor.
After entering , I hovered the mouse cursor over the Enter button on the Trezor website. How can I find the coinbase transactions where the bitcoins involved in a transaction were created? Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. Except for the first few bytes, the rest of the coinbase data can be used by miners in any way they want; it is arbitrary data. It will take on average more than quadrillion hash calculations per second for the network to discover the next block. When specified it indicates how much of the product quote currency to buy or sell. I told Saleem I wanted step-by-step video instructions on what to do. January 4, Sent by either side to initiate session termination. My cryptocurrency stash was starting to turn into some real money. Furthermore, by knowing the target, anyone can estimate the difficulty using statistics and therefore know how much work was needed to find such a nonce. All the best. The bitcoin was growing in value, and it was getting further away from me. Batch cancel all open orders for the current profile; S: Researcher Thomas Kilbride, an embedded devices security consultant at IOActive, was able to further weaponize these attacks using a now-disabled GPS tracking feature that surfaced location data for MiniPRO Hoverboard users in a given area. Then I installed the exploit firmware, entered about a dozen different Linux commands, pressed the buttons to soft-reset the Trezor, then entered a few more commands. The block header hash for block , is:. The regular payouts from a mining pool will help him amortize the cost of hardware and electricity over time without taking an enormous risk.
Furthermore, the number of participants in mining and the computers they use will also constantly change. When verified, the inputs are removed and the new outputs are added to the UTXO set. This allows high-priority transactions to be processed even if they carry zero fees. If the order could not be canceled already filled or previously canceled, etcthen an error response will where do you find your private key in coinbase how to backup ripple wallet the reason in the message field. This ensures that only valid blocks are propagated on the network. Visit the Coinbase accounts API for more information. As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. The first such chips could deliver more mining power in a single box than the entire bitcoin network in I asked Saleem to explain how his hack worked. A faster block time would make transactions clear faster but lead to more frequent blockchain forks, whereas a slower block time would decrease the number of forks but make settlement slower.