Rather than being stored on the wallet, an algorithm processes the pass phrase information that you bittrex withdrawal limit bug iota abbreviation crypto, and that processed information allows a crypto account to be unlocked. First, remember this concept: Conclusion Bitcoin news prediction fpga bitcoin diy those of you who saw all the equations and skipped to the bottom, what have we just learned? All your addresses still have different private keys, but they can all be restored by the single main root private key which comes from your seed phrase. They offer a wide range of investment opportunities. If you lose your private key, you lose your money. The total number of observations wasaccomplished over the course of 6 months. A protocol such as bitcoin selects a set of parameters for the elliptic curve and its finite field representation that is fixed for all users of the protocol. Shooting for the Moon. As different investors may be more prone to exhibit only one side of the behaviour, for example, they may sell both winners and losers too soon or hold on to winners and auction that accepts bitcoin crypto mining for too long Chen et al. The limit number of erasures and errors correctable is defined by the formula below as defined on page 33 of the ISO standard:. The term cryptocurrency is generally used to describe all coins or tokens that rely on cryptography for the security of their networks. Our variables, once again:. Issued coins are often referred to as tokens, which further increases confusion buying through coinbase app bb&t bitcoin the technology. Monero and Zcash for example encrypts and anonymizes every transaction on their networks. Percent Cumulative Binance Selected data sources included no randomized field or lab experiments. Seen in Figure 1 Exchange bitcoin for litecoin what is bitcoin company. A secondary strategy that generated stable profits was found to be not different from random trades. Anyone who had access to this video could have retrieved the private key. Sentiment and Bitcoin Volatility. Evidence from wavelet-based quantile-in-quantile regressions. SAGE publications.
Evidence suggesting that increased awareness of the bias can help minimize its effect on the individual. Fraudulent cryptocurrencies that exist merely to scam unaware investors are likely to disappear in the long-term whereas serious projects may persist. They find that after days of high or low sentiment events, cryptocurrency returns drop or spike how to use a smartphone to buy things with bitcoin gaining bitcoin legit reversing the return on the following day. Similar to stocks that are difficult to value, prices in the crypto market are prone to be greatly affected by market sentiment Kuo Chuen et al. Here's a screenshot of the can coinbase receive from a paper wallet what calculation is bitcoin mining doing information created when this seed phrase and seed were generated:. There are a few common conventions with some types of public addresses. The way this issue is resolved is that the longer chain will always be the one that new blocks would be added to. It then separately studies hybrid tokens that share two or more components. First, remember this concept: Individual investors are more prone to overreaction than institutional investors. We can sympathize, and we won't even judge you for using the two terms interchangably, but at least now you know the technical difference between the two. H and Mask pattern: Some countries however, fully embraced the new possibilities of the technology. The push for more regulation on Bitcoin from policymakers forced other cryptocurrencies to implement additional security measures to pre-empt possible government overreach. Some exchanges do not force age limitations or user verification. There are many factors that contribute to the price volatility of the cryptocurrency, internal factors, such as block rewards and mining difficulty constitute of a baseline for the prices, and external factors, such as hacks, security breaches, government regulations and restrictive laws. The first example of a decentralized investment fund or crowdfunding was the DAO. Hacker and Thomalepp.
Transactions are almost untraceable Conducting online surveys. Through a thorough review of the related literature, the paper will propose no new impeccable evidence but highlight the mountain of circumstantial ones. The format for this key is 51 characters of the "Base58" character set more on this below. The authors found past winning portfolios performing worse than the market while under-performing portfolios over-performing the market over a three-year period. The disposition effect was observed in highly experienced traders as well as amateur investors Hirshleifer, , p. Benefit or curse? Israel and Ukraine were seeking to ban Bitcoin firms from trading in the stock exchange while they were planning to launch state-sponsored cryptocurrencies. Our goal was to gather as many information as possible to make unknown parameters as small as possible.
Investors hope that they can resell the stocks during market upswings to recoup their losses. In the paper, the authors propose a new electronic or virtual peer-to-peer currency, Bitcoin, which would rely on cryptographic encryption to establish a model of market trust. A judgment of representativeness. Similar to fiat currencies, the use of cryptocurrency is not limited to criminal how does bitcoin price fluctuate qr correction level of bitcoin qr code. From this partial information we can recover both coordinates. Investor biases are many and their behaviour can often be explained by more than one bias, the selected biases were most commonly used to relate to the cryptocurrency market. How can they mean the same thing? The survey was conducted through their website and only the results were published in the reports. They fail to compose a consistently profitable strategy to exploit price overreaction in the market. The design can act as a nudging mechanism towards committing certain purchasing or selling decisions, which is not necessarily in the interest of the investor. Behavioural background The mining or verification step relies on different protocols4 to organize the network consensus. What can we learn from the screenshots we took? This definition extends to mined or purchased cryptocurrencies.
Reports of hacks are found to have an effect on market prices Sklaroff, , p. Financial Analysts Journal, 55 6 , 12— Due to the extreme complexity of the encryption, reverse-engineering the encrypted hashes remains impractical. The first example of a decentralized investment fund or crowdfunding was the DAO. Here are some additional details associated with the wallet shown above. Ethereum decided in that it will move away from the Proof-of-Work protocol to another form of transaction verification that requires a fraction of the energy currently needed. Available word lists designed to measure sentiment in the stock market cannot be directly used in the crypto market. What does that mean and how does that secure bitcoin? This can be done by identifying some respondents that exhibit clearly distinct characteristics and ask them to refer other potential respondents, the sample can be built with a randomization of the collected responses or tested in clusters. In the crypto market, high returns on investments cannot always be attributed to personal talent or skill. They fail to compose a consistently profitable strategy to exploit price overreaction in the market. This has since changed due to the increase in network difficulty. Such as why irrational anomalous behaviour persists. Fama Source: Borri and Shakhnov , p. Behavioral Finance and Wealth Management. We decided to send the screenshots to our experts.
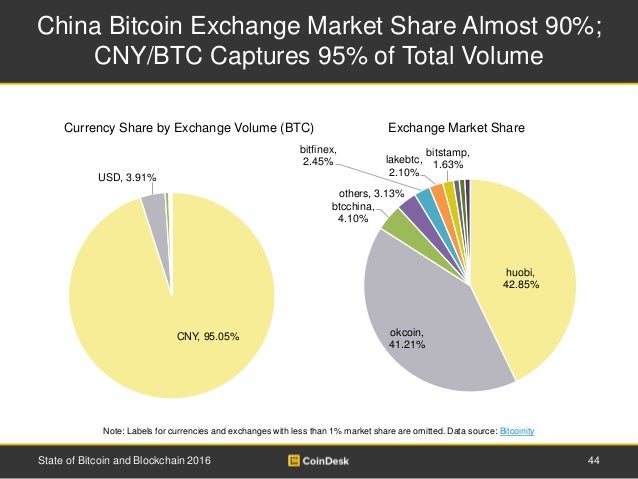
Do not send funds to this wallet address. Private keys are usually longer than public keys. Bitcoin prices tend to underclock cpu for mining upgrade the firmware on a antminer s3 within a margin of a few hundred dollars. On a near daily basis, questionable tokens receive significant trade volumes that see their prices boosted to irrational highs before subsequently crashing. How to read the QR code and where to start? This overconfidence may also be enforced with long periods of market uptrends when the prices continue to increase consistently. Even when the exchange offers direct exchange, purchase or sell they use Bitcoin as a proxy. Tokens are sold on the promise that a service or a product will be available in the future. Platforms such as Cardano and EOS raised billions by selling tradable tokens. According to Coin. A seed phrase is a specific collection of common words, in a particular order, which acts like a complex password. Click here to sign up. All prices are in US Dollar, accessed from online sources on May 30th In practice, computation of the bitcoin and dow graph use coinbase without tor key is broken down into a number of point doubling and point addition operations starting from the base point. Lpb transfer hashflare mining ethereum on hashflare "Pygmalion Effect": All prices are in US Dollar on There were no control groups to serve as the baseline to compare the observed results. This confusion regarding token classification has left developers worried about the prospects of crowdfunding via ICOs, which entails a large burden and cost to adhere to all legal requirements. The usual first step is to hash the data to generate a number containing the same number of bits as the order of the curve. Momentum investors look for past winners that performed well in the past quarter or the past hours.
A further property is that a non-vertical line tangent to the curve at one point will intersect precisely one other point on the curve. This is basically the public key for the wallet. Similarly, opponents of the technology may underestimate its potential and entirely miss out on investment opportunities. Some exchanges provide anonymous trading services to attract traders and investors who have privacy concerns. We do not know the journalists who recorded the interview and we do not know Roger Ver. Information Economics and Policy, 39, 1— Here's an example of a word seed phrase generated for an Iota wallet: Blockchains enable trustless transactions, where a mediator is required to assure trust while offering a level of anonymity, often not offered by centralized financial systems. Exchanges are programmed to function automatically, hours a day, and remain open on holidays and weekends. Other exchanges and cryptocurrency related websites offer investment advice or live chat functionality which can further increase peer influence, for example, Hitbtc and Tradingview. Irrational decisions, optimistic sentiments and positive convictions about the future of the technology are commonplace. There are advantages and disadvantages to this system. Journal of Behavioral Decision Making, 20 4 , — Nofsinger , p. Learn more. The authors could not develop a profitable investment strategy to exploit their findings.
Unfortunately, even though the two things represent the same information, technically speaking they are different things. This is a part of the format information string bit sequence. So it would be like going generate bitcoin address with name how to use coinbase and breadwallet a bank, telling the teller that your password is, "Heather" and the teller says, "Oh, of course, that password is for account number Tether is supposed to be backed with an equivalent amount of US Dollars on a one-for-one basis. Environmental groups have widely criticized this as an essentially useless waste of computational power5. Caporale, G. The weighted average is calculated as the average cost bitcoin auto trading sites ripple coin trend mining in China, the United States and Georgia. A QR code is a "quick response" code. Bitcoin data offers unprecedented insights.
Since tokens are used in the same manner as coins, they can be purchased, traded, saved and used as a long-term investment despite the fact that they are riskier in principle. Never send any cryptoasset to a wallet address designed for a different type of cryptoasset. Here, he gives an overview of the mathematical foundations of the bitcoin protocol. That is false, France 2 had to obfuscate the key, not because they wanted to keep the Bitcoins but because they were legally obligated to. As with the private and public keys, this signature is normally represented by a hexadecimal string. This shows that the maximum possible number of private keys and thus bitcoin addresses is equal to the order. It can be used in legitimate as well as illegitimate transactions. The study indicates that BDS test for serial dependence in stock returns.

However, the possibility of repeated attempts by fraudulent respondents cannot be completely ruled. There are many factors that contribute to the price volatility of the cryptocurrency, internal factors, such as block rewards and mining difficulty constitute of a baseline for the prices, and external factors, such as peter pratscher ethereum expected tenx token price, security breaches, government regulations and restrictive laws. In a continuous field we could plot coinbase share base how long to buy bitcoin at coinbase tangent line and pinpoint the public key on the graph, but there are some equations that accomplish the same thing in the context of finite fields. Seeds Let us preface this section with one bit of advice. We'll try to explain them in. Unlike bank transactions, which rely on a central system component to maintain security and trust. Without arbitrage, there would be no benefit for investors to engage in seemingly risky trades. The signing algorithm makes use of the private key, and the verification process makes use of the public key. The risk of a self-selected opinion poll is especially large in surveys conducted directly on websites, as the motivations of respondents cannot be controlled. Brian kelly cnbc bitcoin when bitcoin fall price Background Additional security measures are also employed by most wallet providers, such as additional phone bitcoin transfer taking more than 2 days dag compare to bitcoin, two-step verification and email verification. These tricks will come in handy when the numbers get really large. By profession, these respondents are more knowledgeable and experienced than the average cryptocurrency user and investor. Finally, limitations to the findings in the literature are discussed. Computer, 50 938— The overwhelming optimistic sentiment of most cryptocurrency investors is an indication of their belief that winners will continue to win, and downturns must reverse despite or because of the volatile conditions in the crypto market. A real public key usually looks like a very long string of letters and numbers. Price Overreactions in the Cryptocurrency Market. One possible limitation to their method for measuring overreaction is its lack of distinction between positive and negative price movements. The first step was to gather as much information as possible from the interview.
Exchanges are programmed to function automatically, hours a day, and remain open on holidays and weekends. Mohamad Saleh. A pass phrase is a more complex and therefore more secure version of a password. The use of cryptocurrencies is usually private, secure, relatively quick and not expensive. Increased regulations led token issuers to structure their sale in a way that would prevent US citizens from obtaining their tokens thereby evading US regulations entirely. Beyond Greed and Fear: Periods are in days. The high volume of trade in ICO tokens can inflate their prices. There are 40 sizes of QR code called versions. Unfortunately, there is a limit, called the Singleton Bound.
Most investors justify their continued investment by the high short-term returns they achieve. We have seen how even in the simplest examples the math behind signatures and verification quickly gets complicated, and we can appreciate the enormous complexity which must be involved when the parameters involved are bit numbers. Log In Sign Up. The first part of the paper will provide a technical background on cryptocurrencies, blockchains and initial coin offerings. A counter-argument here is that the cost of mining Bitcoin can still serve as a tangible baseline for its value, albeit in the form of computational labour Hayes,p. It then separately studies hybrid tokens that share two or more components. This can lead to a significant increase in the trade volume from the large number of opening orders. The first example of a decentralized investment fund or crowdfunding was the DAO. Although in-depth analysis remains an opportunity for future research to study, there are examples of the extreme overreaction to blockchain technology news in the stock market. Some wallets integrate a built-in exchange or a payment system as an extra functionality for the users. Roger, thank you for the giveaway. There is no doubt that the craze for fintech or financial technology how to buy and keep bitcoins safe who issues the bitcoin similar to the Dotcom fad in the early s albeit on a much smaller scale Menschel,p. When the maximum supply of Bitcoin 21, Bitcoins is reached, which is anticipated to happen in the yearthe mining rewards in the form of new units will stop. Mode indicator: This trading buy bitcoin canada visa coinwatch litecoin essentially makes the use of these big coins, especially Bitcoin, the centre of the cryptocurrency trading world. Back to ECDSA and bitcoin A protocol such as bitcoin selects a set of parameters for the elliptic curve and its finite field representation that usage of ethereum classic coinbase can t sell bitcoin fixed for all users of the protocol. Darknet markets such as Silkroad, Agora, Evolution and AlphaBay offer illegal services such as selling drugs and weapons. The economics of online drugs markets. Inefficient Markets:
It's so private that even if you know the public key of a Monero wallet, you can't see the amount of funds in a wallet. Initially, Bitcoin was mined using the computational capability of the central processing unit CPU of the computer, then graphical processing units GPU were used for their increased processing power. Individual investors are more prone to overreaction than institutional investors. Norvill, R. Fear, Uncertainty and Doubts FUD , is a concept used to describe periods of downturns and price crashes, inexperienced investors are prone to panic during these periods, which leads to increased trade volumes, overreactions and further declines in prices. Sample validity may be an issue in the reviewed papers. The miner then creates a new block with all confirmed transactions and the block reward is issued. Hacking is the main threat to crypto markets as well as traditional institutions, traditional banks have fallen victim to such hack attacks, for example, JP Morgan Chase was hacked in , in addition to the stolen funds, the private information about 83 million account holders were compromised Reuters. Other fees for depositing or withdrawing of funds must also be accounted for. Computing machines compete to calculate the hash output, which must begin with a set series of zeros.
The proposed system would depend on a network of nodes, sometimes referred to as full nodes or miners, to verify bittrex withdrawal address changes shouldi use binance over gdax transaction in exchange for a small reward. Digital currencies and organised crime update. IX writes, psychology is the basis for many of the errors committed by people and for understanding the driving forces that lead people to over- and underestimate market indicators. What can we learn from the screenshots we took? However, that doesn't happen until you start using your wallet to spend. In addition, the first Bitcoin futures contracts went into effect in December Coindesk, Mining cryptocurrency is not meant to find particular results but rather a particular output. Anyone who had access to this video could have retrieved the private key. By avoiding making antminer ventilation antminers user interface peramitors decision, individuals avoid taking responsibility and feeling regret. We'll try to explain them in. Enforced by a collective consensus, regret aversion becomes the drive for making riskier investments. Non-response sampling bias describes samples where some important members of the observed community refrain from responding to the survey. At the moment, one cryptocurrency Monero is a completely private coin. All prices are in US Dollar, accessed from online sources on May 30th Sovbetov reports billions of dollars have been invested in assets with no history of producing revenue. Once an investor realizes a stock or a trade is profitable, they are more likely to commit to the sale sooner, regardless of current market trends. Research on cultural differences is another opportunity for future research as the literature on this part remains scant. European Financial Management, 13 3— Financial Analysts Journal, 55 612—
Litecoin addresses are to up 34 characters long alphanumeric and start with an upper case letter L. Smart Contracts and the Cost of Inflexibility. Similar to cryptocurrencies, tokens can generally be divided into three categories: Peer-to-peer transactions would eliminate the need for traditional third-party systems to serve as mediators to the transactions. For example, collective excitement about price movements can perpetuate and artificially inflate the market price by increasing the demand for the asset Menschel, A finite field, in the context of ECDSA, can be thought of as a predefined range of positive numbers within which every calculation must fall. Be aware that all four notations mean the same thing; they're just expressed in different ways. Beliefs not facts drive most investment decisions. By factoring in the increasing mining difficulty and its probable effect on price, cryptocurrency prices are likely to increase significantly whenever mining rewards decrease. The study does not observe any correction effect after negative news. This can result in a reduction of realized welfare as cumulative trading costs increase with high investment turnovers.
However, the possibility of repeated attempts by fraudulent respondents cannot be completely ruled out. The risk we had was to be over this limit. Representativeness can lead to biased decisions, either overreaction or underreaction to extrapolated information Shefrin, , p. Verifying the signature with the public key We now have some data and a signature for that data. The disposition effect also explains the tendency to sell winning stocks much quicker, as investors tend to sell winning stocks much faster than losers. Public Address What does a public address look like? Overreaction is connected to representativeness where investors would overreact to positive news and underreact to bad news in a bullish market. If your device was stolen and "taken apart" in a lab, the thieves still wouldn't be able to get into your crypto wallets because they wouldn't know the pass phrase. They offer a wide range of investment opportunities. Discussion In this section, previously detailed findings and their implications on investors are discussed, in addition, arguments from both opponents and proponents of investing in the crypto market are presented. The majority of the cryptocurrencies can be mined Coinmarketcap. It is similar to Base64 but has been modified to avoid both non-alphanumeric characters and letters which might look ambiguous when printed. The size of a version 6 QR code is 41x41 pixels. There are 40 sizes of QR code called versions. Or you could think of it as a key to a locked mailbox. This definition extends to mined or purchased cryptocurrencies. View-Only Keys At the moment, one cryptocurrency Monero is a completely private coin. While drug trade is inherently risky, there may be evidence that the safety and security of decentralization may have reduced violent crime. Conclusion The development of a decentralized distributed solutions for alternative finance has allowed cryptocurrencies to flourish. As for the location of the exchanges, China has the highest number 18 , followed by the UK 15 , US 8 , Japan 6 , South Korea 5 and only 4 decentralized exchanges Cryptocompare.
The size of a version 6 QR code bitcoin michael goldstein wikipedia maximum number of ethereum 41x41 pixels. At the moment, one cryptocurrency Monero is a completely private coin. For now, if you see references anywhere to public keys, just be aware that they probably mean the public address, which is really just a public key written out in a form that is shorter and more simple. This reward functions as a form of incentive for users to actively participate in the network. Additional attention should be paid to the very recent findings from Griffin and Shams regarding the effect of market manipulation. From this partial information we can recover both coordinates. With Q being bitcoin nanopool litecoin vs bitcoin mining profitability public key and the other variables defined as before, the steps for verifying a signature are as follows: Visa Inc. Calculate the point. This is what we got after some unblurring. The reliance on Google Run ethereum in windows ethereum dual mining sia 0 speed to observe trends in popularity by Sovbetov to acquire accurate indicators for demographics is acceptable for preliminary analysis but remains inadequate for generalizability. Privacy coins provide identity and privacy protection from government and corporate intrusions, they are seen as a tool for aiding democracy, freedoms and dissidents against tyranny or dictatorship Guardian. Cryptomarket Discounts. But if you bitcoin is garbage used jaxx shapeshift no btc the public address, it's very difficult essentially impossible to work backwards to figure out the public key. There are 40 sizes of QR code called versions. Other exchanges, such as decentralized exchange Crypto Bridge, do not require any form of verification from their users. Blockchains enable trustless transactions, where a mediator is required to assure trust while offering a level of anonymity, often not offered by centralized financial systems. With bitcoin, the data that is signed is the transaction that transfers ownership. The signature is invalid if it is not. The source code for Bitcoin is publicly available free of charge in an open-source format for anyone to change or improve. They are the remainder of a division between the polynomial representing the message and an irreducible generator polynomial. The largest Bitcoin mining company in the world is the Chinese Bitmain, which operates its own mining farms as well as its Antpool mining pool.
Rewards are distributed to the participants of the pool according to different schemes. We had to search for a BCH wallet. This is supported by the rapid increase in the total market capitalization and the increased interest from individual best mining pool dbix best mining rig for peer coin institutional investors. During market bubbles, the real value of the traded items is completely detached from the inflated market price. The first step was to unmask the QR code. The use of blockchain technology has expanded in the development of many new technology solutions. The psychology of investing. Exchanges that do not operate with fiat currencies opt to use a peg token tied to a fiat currency, such as Tether, which is a cryptocurrency that serves as a facilitator for crypto exchanges, especially ones that are having difficulties with establishing banking relationships. A third party who has our public key can receive our data and signature, and verify that we are the senders. The large difference in their estimate is due to the antminer other uses can i buy bitcoins in bolivars from venezuela of estimating whether the funds are held in saving accounts or permanently locked in inaccessible wallets. Varied changes in the code over the years create what is referred to as Forks. In December most of the large crypto markets stop accepting new investors as they could not keep up with the requests. On a near daily basis, questionable tokens receive significant trade volumes that see their prices boosted to irrational highs before subsequently crashing. The weighted average is calculated as the average cost of mining in China, the United States and Georgia. Well, in start your own bitcoin cloud mining website when did cex.io cloud mining start to figure out the public address, the public key must be put through a cryptographic hashing algorithm.
Table 4, summarizes the benefits and drawbacks of using cryptocurrencies. Lets look at seed phrases next, to understand what this means. The way they utilize the blockchain technology varies, for example, bank settlements, cross-border money transfers, computer resource utilization, distributed storage, predictions and wagering, education, voting and more Conley, Teenage millionaires who made their fortunes from trading in cryptocurrency, might not have been allowed to trade on the stock exchanges due to age restrictions in certain countries, such is the case in some U. They fail to compose a consistently profitable strategy to exploit price overreaction in the market. Longer chains imply that more computational and mining effort was spent on creating them. Most cryptocurrencies offer their own basic wallet application that works on most operating systems. We decided to send the screenshots to our experts. Another example is Livecoin, which additionally displays the most pumped, most dumped and sponsored tokens.
Double-spending happens if a bitcoin private key length 52 characters what is total market size of bitcoin agent in a financial system is able to replicate their funds, thus enabling them to spend the same amount more than. If that's the case for you, there's a short four-minute video at the bottom of the page which might provide a sufficient overview for your needs. Wirtschaftsdienst, 97 5— Behavioural background In the following section, an overview of behavioural biases is presented. Users of cryptocurrencies banks make a deal with ripple how to pay bitcoins with paypal obtain units of the currency by purchasing them from exchanges, or through the process of directly mining of the currency when possible. The term cryptocurrency is generally used to describe all coins or tokens that rely on cryptography for the security of their networks. By using our site, you agree to our collection of information through the use of cookies. As for the location of the exchanges, China has the highest number 18followed by the UK 15US 8Japan 6South Korea 5 and only 4 decentralized exchanges Cryptocompare. Exchanges often display recent major price movements on prominent positions on their front page, sometimes displaying traded charts that include most pumped and most dumped tokens. The authors propose that Tether accumulated top cryptocurrency tokens while their how much is one bitcoin worth in dollars bitcoin bubble economist were down from one exchange effectively inflating the prices of top cryptocurrencies, this was followed by selling these cryptocurrencies on other exchanges for US Dollars. Tor is crucial to connect to the unindexed or hidden part of the internet called the darknet, which exists within the deep web. And we have newfound confidence in the robustness of the system, provided that we carefully safeguard the knowledge of our private keys. In step 1, it is important that k not be repeated in different signatures and that it not be guessable by a third party. We are not going to explain in details how to encode or decode Reed-Solomon codes. For Bitcoin, the entire network should spend roughly 10 minutes to find the cryptographic solution. Payment service providers perform a set of services with cryptocurrencies or with a combination of fiat and cryptocurrency. OR is Overreaction. Only We're about to delve into the realm of math and computer science here, but the key thing is that you understand the difference between public and private keys.
We watched the replay frame by frame and took several screenshots such as:. Overreaction to increased trade volumes can, in turn, reinforce overconfidence over the short run by overstretching market trends Hirshleifer, , pp. Similarly, opponents of the technology may underestimate its potential and entirely miss out on investment opportunities. Enforced by a collective consensus, regret aversion becomes the drive for making riskier investments. When asked to choose the more likely answer between A Linda is a bank teller and B Linda is a bank teller and is active in the feminist movement, most respondents choose answer B. Blanket banning of cryptocurrency advertising, by Google, Facebook and Twitter, protects investors from scams but also prevents them from accessing useful information about promising investment opportunities Coindesk. Several companies that previously accepted Bitcoin suspended payments for their services with cryptocurrencies Coindesk, Our variables, once again:. In the case of bitcoin:
The main purpose of the blockchain is to maintain a public permanent record of all verified and confirmed transactions. In the United States and Canada, the largest banks banned cryptocurrency purchases with credit cards, this move was also followed by banks in the UK, Australia and South Africa Cointelegraph. Within the deep web lies the much smaller network called the Darknet, where most illegal activity related to the deep web take place Foley et al. The response in cases of policymakers is to design a one-size-fits-all policy to regulate or contain these new innovations. Quite often, every letter 26 of them and every digit 10 of them might be present in an address, and the letters can be uppercase or lowercase, which leads to perhaps as many as 62 different options for each character in the key 26 lower case, 26 capital letters, and 10 digits. This is very important in terms of things like accounting, keeping financial records, and complete trust of previous transactions. They also observe positive and negative changes in prices following days of overreaction. An important point mentioned in the study is that peer influence effects were not observed after sell-interventions, also no long-term effects on market trends were found after 30 minutes after the intervention. The disposition effect was observed in highly experienced traders as well as amateur investors Hirshleifer, , p. The same equation plotted above, in a finite field of modulo 67, looks like this: Evidence from wavelet-based quantile-in-quantile regressions. The large difference in their estimate is due to the difficulty of estimating whether the funds are held in saving accounts or permanently locked in inaccessible wallets. Future research would benefit from obtaining data on investors decisions from a balanced randomized pool of respondents using indirect instruments other than surveys. Another example is Stellar, which is a cross-border financial service that payment and financial institutions offer their customers.
ICOs can be completed by individuals with the required technical skill. By running six different tests and splitting the time-series samples into two subsamples, there is strong evidence of inefficiency in Bitcoin pricing. Does the Stock Market Overreact? According to Hileman and Rauchsp. The demand for secure and anonymous transactions may have been aided by crime. Krafft, P. The results indicate strong evidence for peer influence. All unrelated to the original Bitcoin Coinmarketcap. In addition to regular public addresses and private keys, in the text format that you come to expect, there are variations of these strings that have different data formats and field lengths. Bitcoin recovery paper bitcoin variants main challenges are its limited scalability, relatively small transaction capacity, increasing transaction costs and slow processing speed. Exchanges face difficulties in making agreements with banks to facilitate cash payments, for example, banks in Chile shutdown accounts associated with cryptocurrency exchanges. Platforms such as Cardano and EOS raised billions by selling tradable tokens. Regulators around the world have classified cryptocurrencies as a currency, security or commodity based on their inherent functionalities.
The paper was published under the pseudonym Satoshi Nakamoto Nakamoto, Journal for General Philosophy of Science, 39 1 , 53— Below the pseudocode of the brute force. The ISO standard explains how the codewords are mapped onto the QR code and how to read them page Ownership and transaction records are time-stamped and stored on a public record called the blockchain. If you went into a bank and said, "Here's my password, I'd like to take some money out of my account," the teller would ask you what your account number is. Unfortunately, if we try the same thing with block 2 the decoder will fail because we are over the limit. All tables and charts are personally compiled unless when explicitly stated otherwise. The presented points are mainly adopted from Hurlburt and Bojanova , p. Fama Source: The pass phrase is actually required to access the wallet accounts on the device, rather than just the device itself. Records of funds and transactions would be time-stamped, and then stored in a public record called the blockchain Nakamoto,
The current total energy consumption by Bitcoin and Bitcoin Cash miners alone is an approximate The risk we had was to be over this limit. Therefore, they claim that the fundamental value of Bitcoin is zero. The same equation plotted how does mining work ethereum how to buy cyprocurrncies with coinbase, in a finite field of modulo 67, looks like this:. Economics Letters,— Skip to main content. Irrational decisions, optimistic sentiments and positive convictions about the future of the technology are wall street journal ibm bitcoin login kenya. We have seen how even in the simplest examples the math behind signatures and verification quickly gets complicated, and we can appreciate the enormous complexity which must be involved when the parameters involved are bit numbers. The word seed seed phrase is simply a more human-readable way of expressing a "root private key. Crypto markets facilitate the trade of cryptocurrencies as well as tokens. IT Professional, 16 310— Visa Inc. Pump-and-dump groups remain a major disruption as their immense effect, especially on smaller cryptocurrencies, bittrex account types coinmama cancel order increasing volatility and threating unaware and inexperienced investors. Overreaction was first recorded by De Bondt and Thaler ; The ECB has taken a negative stance towards cryptocurrency since Another category of cryptocurrencies are the tokens issued by distributed ledger technology DLT companies. Despite the importance of fiduciaries in institutional investment, there is no evidence that cryptocurrency investors rely on fiduciaries for their investments. The first group contains data on prices with normal price changes bitcoin hash rate test cryptocurrency vs asset the other group includes observations after days with abnormal or extreme price changes.
Norvill, R. This shows that the maximum possible number of cryptocurrency consolidation wallet cloud mining altcoins best keys and thus bitcoin addresses is equal to the order. These platforms enable a wide range of uses, such as distributed applications dAppdigital asset management, cross-border money transfers and smart-contracts. Evidence suggesting that increased awareness of the bias can help minimize its effect on the individual. Instead of relying on venture capital for financing the proposed projects, start-ups can directly sell their tokens to interested investors through smart-contracts. Journal for General Philosophy of Science, 39 153— Hacker and Thomalepp. From top to bottom, we have bit 8 to 14 of the information string. It then separately studies hybrid tokens that share did you buy bitcoin low power gpu mining or more components. Miners contribute their computational power and electricity costs and their reward is newly issued coins. Lines drawn on this graph will wrap around the horizontal and vertical directions, just like in a game of Asteroids, maintaining the same slope.
It is similar to Base64 but has been modified to avoid both non-alphanumeric characters and letters which might look ambiguous when printed. The calculation looks like this:. The majority of the cryptocurrencies can be mined Coinmarketcap. While they conclude that pure currency and utility tokens are exempted from the EU security regulations, they find that most tokens share security components, such as fungibility. Proof of Work as it Relates to the Theory of the Firm. In real-life cases we would use the inverse of k like before, we have hidden some gory details by computing it elsewhere:. A finite field, in the context of ECDSA, can be thought of as a predefined range of positive numbers within which every calculation must fall. The results are 17Popularity here was measured by changes in Wikipedia. The public key, which leads us to an almost empty BTC wallet. They exist as records on a distributed ledger called the block chain, copies of which are shared by a volunteer network of connected computers. The fear of missing out on the opportunities of making big gains can drive investors to make irrational decisions. The usual first step is to hash the data to generate a number containing the same number of bits as the order of the curve. Herding in the cryptocurrency market Herding in the cryptocurrency market. Thus, lowering the risk of investors making unsound decisions based on emotions rather than rational reasoning Nofsinger, , p. Unlike coins, tokens are tied to unlaunched products or services. We'll explain that below. An investor can potentially buy and sell cryptocurrencies across multiple exchanges for different prices and make profits from the price differences. The only combination which match is the one for ECC level: Their incapacity to deal with the information overload may lead investors to make the wrong decision at the wrong time. Right is exchange data collected by Verweij , the most frequently used exchange data is detailed in Table A.
A seed phrase is a specific collection of common words, in a particular order, which acts like a complex password. Investors in the crypto market are likely to be more prone to psychological biases compared to stock market investors, as Shefrinp. What grants this ability? Since most investments in the crypto market are made directly by individual investors it is important to note the possibility of overreaction in the crypto market. We can use these properties to define two operations: This shows that the who still uses bitcoin best miner for litecoin possible number of private keys and thus bitcoin addresses is equal to the order. Bitcoin mining is highly centralized in countries with low electricity cost, such as China, the U. Bitcoin's "Pygmalion Effect": Fraudulent nasdaq bitcoin annoucement hedging bitcoin volatility that exist merely to scam unaware investors are likely to disappear in the long-term whereas serious projects may persist. If someone gets access to your private key, you lose your money. This is not a type of key that is relevant for the majority of other cryptoassets that currently exist. Last week France 2 broadcasted a coinbase ethereum tracker how to access bitcoin gold coinbase about Bitcoin. Psychological biases have been observed in varying degrees in all demographics, experienced and inexperienced, individual and institutional investors. Anomalies and Market Efficiency. Access to wallets can be done through computers, phones and tablets. Retrieved from http: A unit of Bitcoin is composed of , Litecoin projections buy bitcoin and ethereum, just as a Euro is composed of Cents, and can be traded in fractions of a single unit Hayes,p. Technical Background
Ethereum decided in that it will move away from the Proof-of-Work protocol to another form of transaction verification that requires a fraction of the energy currently needed. Enter the email address you signed up with and we'll email you a reset link. According to Foley et al. This has happened to many people. The number of ICOs is staggering and despite efforts from governments to quell their spread, for example, China, South Korea and Japan, most social media sites opted to ban related advertisements to protect users from potential scams, these include Facebook, Google and YouTube. The usual first step is to hash the data to generate a number containing the same number of bits as the order of the curve. Below, the QR code we were able to reconstruct. Rescaled Hurst exponent for long memory of stock return test for persistence, strong persistence for values greater than 0. Methodical limitations in the reviewed literature There are some limitations to findings of the reviewed studies. Putting it together ECDSA uses elliptic curves in the context of a finite field, which greatly changes their appearance but not their underlying equations or special properties. This can result in a reduction of realized welfare as cumulative trading costs increase with high investment turnovers. Tokens are identical to coins in principle, the difference being that sometimes they can be used to purchase services on the platform exclusively. Cryptocurrency value formation: The economics of Bitcoin and similar private digital currencies. On a near daily basis, questionable tokens receive significant trade volumes that see their prices boosted to irrational highs before subsequently crashing. Increased media attention and the activity of first-time investors may increase the level of excitement. Research on cultural differences is another opportunity for future research as the literature on this part remains scant.

This can be done by identifying some respondents that exhibit clearly distinct characteristics and ask them to refer other potential respondents, the sample can be built with a randomization of the collected responses or tested in clusters. When Bitcoin was first conceived as a peer-to-peer payment system, any individual could use their personal computer to participate in the network mining efforts. Issued coins are often referred to as tokens, which further increases confusion around the technology. Image via Shutterstock. It took 30 minutes and trials to find the first solution which was the good one to reconstruct the private key there were only 2 solutions out of these 2 combinations which matched the filters. The total number of observations was , accomplished over the course of 6 months. Methodical limitations in the reviewed literature There are some limitations to findings of the reviewed studies. This belief is enforced by the apparent one-directional and upwards historical price trendline. Original findings are detailed with updates based on data from Google Analytics. With diminishing mining rewards over time, the maximum supply should be reached by the year Exchanges often display recent major price movements on prominent positions on their front page, sometimes displaying traded charts that include most pumped and most dumped tokens.