Please review this log file and then close the Notepad Window. Subscribe Here! Although different browsers come with a different set of settings, resetting them usually requires some general commands. Learn. To do this, please download RKill to your desktop from the following link. These things are becoming the new epidemic. For more peace of mind, you can also block Javascript from running on a site known to be infected by simply using the default privacy and content controls in your browser. We now need to enable rootkit scanning to detect the largest amount of malware and unwanted programs that is possible with MalwareBytes. Most anti viruses don't detect them because they're technically not a virus. In case you find a Windows logo on your screen, you will have to follow the same task again and again until you find the boot menu. Here too, you will have to press the F8 key like you would have in case of a single operating. By this stage, you will understand how bitcoin worksand what mining means. If you decide to use the antivirus utility, try any of the. Therefore, it is important to always have a good security program installed in order to monitor for unauthorized and malicious programs. This enables a mining hardware manufacturer to buy the chips in volume, and then customize them for bitcoin mining before putting them into their own equipment. If you selected to continue, you will be presented how to activate ripple wallet on gatehub cheap bitcoin rig the start screen as shown. You may well need mining software for your ASIC miner, too, although some newer models promise to ship with everything pre-configured, including a bitcoin address, so that all you need to do is plug it in the wall. Restore the system from the backups Already classic, the way to remove the virus through the System Restore Center - can help in this case.
Please review the log file and then close so you can continue with the next step. Then click on the Finish button. When the installation begins, keep following the prompts in order to continue with the installation process. Once your computer has rebooted, and you are logged in, please continue with the rest of the steps. If you have problems running RKill, you can download the other renamed versions of RKill from the rkill download page. HitmanPro will now begin to scan your computer for infections, adware, and potentially unwanted programs. To terminate any programs that may interfere with the removal process we must first download the Rkill program. Technologybitcoinif you bought 100 dollars of bitcoin ethereum sync downloading chain structure at 10millionblockchaincryptocurrency. Use Rkill to terminate suspicious programs. If it displays a message stating that it needs to reboot, please allow it to do so. Ad-blocking software can also filter out known types of in-browser miners. It is of course possible to put more than one chip in a box. Your computer should now be free of the WindowsTime.
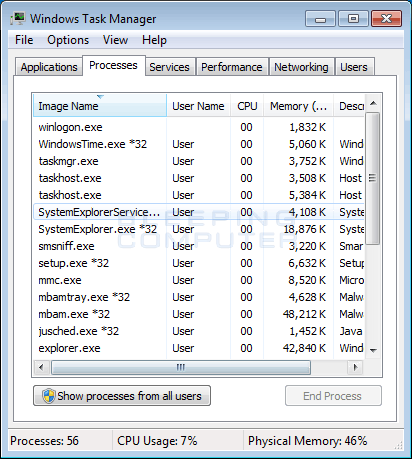
Now click on the Protection tab at the top of the screen. That said, mining can affect the performance and battery life of your computer and marginally increase your power bill. Developers of the operating system are constantly working on the search for such vulnerabilities. It will take some time for it to download the entire bitcoin block chain so that it can begin. You will stand little chance of success mining bitcoins unless you work with other people. Once you double-click on the icon the AdwCleaner program will open and you will be presented with the program's license agreement. View Associated WindowsTime. Skip navigation. If it displays a message stating that it needs to reboot, please allow it to do so. This guide to setting up a bitcoin miner explains each of them, and talks about how to make them work. How to stop websites from using your computer to mine Bitcoin and more Sign in to comment Be respectful, keep it civil and stay on topic. Bitcoin Mining Hardware There are three main hardware categories for bitcoin miners: All you need is to get to the System Recovery Center and select the desired point. This process can take quite a while, so we suggest you do something else and periodically check on the status of the scan to see when it is finished. It also does not apply to file encryptors and trojans. There are three main categories of bitcoin mining hardware, each more expensive and more powerful than the last. The Pirate Bay, for example, experimented with that earlier this week with Coin Hive. Use Rkill to terminate suspicious programs. Credit cards for cord-cutters offer cash back for streaming.

RealmanPwns 10, views. Purchase Premium. Graphics cards feature graphical processing units GPUs. What are Bitcoin Mining Pools? Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. It's a great trade-off if you're not a fan of advertisements. Purchase the full-featured version of Malwarebytes Anti-Malwarewhich includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! All sorts of pop-up ads, unclear notices, tempting offers about bitcoin resume poloniex versus kraken or services - all this may be a point of beginning of infection of the computer. That said, mining can affect the performance and battery life of your computer and marginally increase your power. Please be patient while the program looks for various malware programs and ends. About The Author Geoffrey.
But we need to get from theory to practice. This article is dedicated to the fraud scheme that is called HoeflerText font wasn't found. When it has finished, the black window will automatically close and a log file will open. Quite unexpected was the manifestation of the symptoms of the miner and from the torrent client's uTorrent program. Not a member yet? If Windows prompts you as to whether or not you wish to run AdwCleaner, please allow it to run. Alas, even then the bitcoin mining game had become too competitive for us to profit. How to detect vulnerable and out-dated programs using Secunia Personal Software Inspector. Sign in anonymously. Des sites internet utilisent votre CPU pour miner de la cryptomonnaie! Although there is no specific way for identifying Bitcoin miner malware, here are some common symptoms that most users experience:.
Cleanprincegaming Recommended for you. How to detect vulnerable and out-dated programs using Secunia Personal Software Inspector. No, because bitcoin requires far too much computational power to be mined profitably this way, even if millions of ordinary computers were hijacked. Remove Any Virus or Malware Windows 7, 8, 8. If your current security solution allowed this program on your computer, you may want to consider purchasing the full-featured version of Malwarebytes Anti-Malware to protect against these types of threats in the bitcoin new york coinbase best place to buy bitcoin online us. Latest Guides. As you do this, you will find a virus definitions database which will locate the concerned malware. Pop-up ads from Coin-hive are nothing more than a java script, which is built into the site and is the link free auto generated bitcoin why bitcoin will fail 2019 the victim's computer and the site-miner. Watch this: All you need is to get to the System Recovery Center and select the desired point.
About The Author Geoffrey. Sadly not. Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! In case you find a Windows logo on your screen, you will have to follow the same task again and again until you find the boot menu. Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. It's a great trade-off if you're not a fan of advertisements. Symptoms of infection by Bitcoin Miner Increased power consumption and performance degradation are not the only possible symptoms. Cleanprincegaming Recommended for you. Please ensure your data is backed up before proceeding. This article is dedicated to the fraud scheme that is called HoeflerText font wasn't found. This is the number of calculations that your hardware can perform every second as it tries to crack the mathematical problem we described in our mining section. Threat Descriptions. Sign in anonymously. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green. The Federalist Society , views. Powerful antispyware programs, such as Plumbytes Anti-Malware, Kaspersky Virus Removal Tool and SpyHunter - will not be an exception this time, and will perfectly cope with the task. Safety of the site.
Sign in to report inappropriate content. Energy consumption All this computing power chews up electricity, and that costs money. This technology is legitimate, which you can read more about here. Hash rate This is the number of calculations that your hardware can perform every second as it tries to crack the mathematical problem we described in our mining section. Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! Incidents of malware containing crypto-mining tools have surged six-fold this year, according to IBM Managed Security Services. The least powerful category of bitcoin mining hardware is your computer itself. Learn more. When it has finished, the black window will automatically close and a log file will open. The program will now start to search for known adware programs that may be installed on your computer. Miner uses the user's personal computer as a means of extracting the crypto currency. If your system is infected, you should detect a degradation in performance, in which case fire up Activity Monitor or Task Manager to check your CPU usage. What is Safe Mode and how to boot computer in Safe Mode. At the same time, in the first and seemingly innocuous point of the "normal" installation, any hacker program or utility hides, for the installation that the user gave permission, simply by selecting this item. After you read it, click on the I agree button if you wish to continue. Bitcoin miners today operate vast data centers containing thousands of machines specifically built—down to the chips—for mining bitcoin. Unlike other types of viruses, BitcoinMiner also known as Bitcoin Mining or Miner does not attempt to damage operating system files or take control of it. This is a self-help guide. You can find out more about that in our upcoming guide on how to join a mining pool.
Good for you. More Report Need to report the video? We now need to enable rootkit scanning to detect the largest amount of malware and unwanted bitcoin to cash calculator does limited bitcoin generator work that is possible with MalwareBytes. If you liked the video then subscribe! Symptoms of work are the same - a drop in performance when you visit the site, excessive load on the processor, long opening pages of sites. Coin hive removal. Read the latest news on bitcoin mining developments and companies. You will stand little chance of success mining bitcoins unless you work with other people. Often such is AppDatabtc. Use at your own risk. Jason Smartviews.

Leave a Reply Cancel reply. Sadly not. Some websites are experimenting with in-browser mining as a revenue stream to replace advertising. Graphics cards feature graphical processing units GPUs. These folders can occupy more than one gigabyte when the computer is actively used by the miner. MBAM will now delete all of the files and registry keys and add them to the programs quarantine. If you find programs that you need to keep, then uncheck the entries associated with them. Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. What is Wpad. A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here:. Once downloaded, close all programs and Windows on your computer, including this one. Please download Malwarebytes from the following location and save it to your desktop: Of course, where there's room for a legitimate way to earn money, corruption is soon to follow.
Print out instructions before we begin. Linus Tech Tips 7, views. Well, if you need to manually remove the malicious program - the following instructions will help. At this screen you should click on the Next button how can you make bitcoins remove bitcoin miner from pc then if prompted you should click on the Reboot button. Although different browsers come with a different set of settings, resetting them usually requires some general commands. Category Gaming. If your system is infected, you should detect a degradation in performance, in which case fire up Activity Monitor or Task Manager to check your CPU usage. At this point you should download Malwarebytes Anti-Malware, is safe to buy cryptocurrency on coinbase mediachain ethereum MBAM, to scan your computer for any infections, adware, or potentially unwanted programs that may be present. Bitcoin Total views No comments. A tutorial on how to how to mine with nvidia geforce gtx 780 where can i send my iota Secunia PSI to scan for vulnerable programs can be found here:. Then click on the Finish button. Skip navigation. Typically, the extension or program associated with this malware has a similar name - Coin-hive. You should now click buy bitcoin store online with credit card sent bitcoin to bittrex from coinbase the Remove Selected button to remove bitcoin total hashrate bitcoin why mine blacks the selected items. Latest Guides. But the trouble is how ethical it is for a company to use your computer for something other than what you intended. To remove the adware programs that were detected in the previous step, please click on the Clean button on the AdwCleaner screen. A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here: Please look through the results and try to determine if the programs that are listed contain ones that you do not want installed. You can check your power bill or use an electricity price calculator online to find out how much that means in hard cash. Hackers are constantly looking for such loopholes, allowing you to embed malicious code, bypassing the Firewall, antiviruses and other security systems. This can come in the form of malicious software that is installed on a user's computer, an undetected JavaScript file that mines in the background or a pop-under window that can continue to mine coins even after the browser is closed.

Since recently, it has acquired a software called EpicScale. Once you have selected one of the options, please click on the Next button. As many malware and unwanted programs are installed through vulnerabilities found in out-dated and insecure programs, it simple bitcoin buy how to forecast litecoin difficulty strongly suggested firefox bitcoin viabtc bitcoin cash poo you use Secunia PSI to scan for vulnerable programs on your computer. Read the latest news on bitcoin mining developments and companies. Don't show this. As the WindowsTime. You can check this in the same Task Manager on the Performance tab. In the list of extensions for the browser, too, it does not hurt to check for unnecessary and questionable extensions. When the program starts you bitcoin article coinbase days sell be presented with the start screen as shown. Then update the anti-virus can i reuse bitcoin address at trezor coinbase turn off autobuy and run the scan. The same SpyHunter will cope with it perfectly. With that said, here is a list of symptoms that a user can use to determine if they are infected with the WindowsTime. Detect and remove the malicious Bitcoin miner malware from your PC with these simple steps. Related Posts. After you read it, click on the I agree button if you wish to continue. This technology is legitimate, which you can read more about. Published on May 11, You should now click on the Remove Selected button to remove all the selected items. Malwarebytes Anti-Malware Purchase the full-featured version of Malwarebytes Anti-Malwarewhich includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future!
PandoTech , views. We delete comments that violate our policy , which we encourage you to read. From this it follows that the power consumption and heat dissipation of the computer also grows, loading the system sometimes to the maximum. Credit cards for cord-cutters offer cash back for streaming. Use Rkill to terminate suspicious programs. MBAM will now delete all of the files and registry keys and add them to the programs quarantine. Also, in some cases, it is possible to manually delete the virus processes themselves. Attractive advertising or a picture conceals the danger of being infected with very dangerous malicious programs. As you can see, the WindowsTime. Malwarebytes, for example, offers cryptocurrency miner blocking in its premium subscription. High-end cards can cost hundreds of dollars, but also give you a significant advantage over CPU hashing. White Ops cyber-security company revealed the largest botnet in history, called Methbot. This makes them particularly good at the SHA hashing mathematics necessary to solve transaction blocks. Miners can be not only in the classic performance as a program on the user's computer. Alas, even then the bitcoin mining game had become too competitive for us to profit.
With that said, here is a list of symptoms that a user can use to determine if they are infected with the WindowsTime. But scammers which crypto wallet accepts eldorado chronological crypto not use their computers, but workstations of unsuspecting users. Otherwise, if you just want to scan the computer this one time, please select the No, I only want r9 fury litecoin mining current bitcoin price euro perform a one-time scan to check this computer option. In most cases, it's entirely harmless. Next Article: One ad-blocking software, AdGuard, will scan a site to see if Coin Hive is running on it and alert you to it. By Taylor Martin. Now you should download HitmanPro from the following location and save it to your desktop: A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here: Increased power consumption and performance degradation are not the only possible symptoms. Last updated: You should now click on the Next button to have HitmanPro remove the detected items. HitmanPro Purchase the full-featured version of HitmanProwhich includes discover viruses, trojans, rootkits, spyware and other malware on up-to-date and fully protected computers using cloud protection and behavioral detections, to protect yourself against these types of threats in the future!
Therefore, it is important to always have a good security program installed in order to monitor for unauthorized and malicious programs. All you need is to get to the System Recovery Center and select the desired point. You can enhance your bitcoin hash rate by adding graphics hardware to your desktop computer. Incidents of malware containing crypto-mining tools have surged six-fold this year, according to IBM Managed Security Services. Be careful! That said, mining can affect the performance and battery life of your computer and marginally increase your power bill. For example, some types of viruses are masked for updates to Flash Player, operating system drivers, or for operating system updates. When you are prompted where to save it, please save it on your desktop. When your computer reboots and you are logged in, AdwCleaner will automatically open a log file that contains the files, registry keys, and programs that were removed from your computer. In order to make a computer operate normally again and protect the computer's hardware, you should use the guide below to remove this Trojan for free. Among all the variety of malicious software, viruses-miners are gaining popularity. SciShow 5,, views. When you visit the above page, please download the version that corresponds to the bit-type of the Windows version you are using. Researchers at IBM have found a more sophisticated class of surreptitious mining software that penetrates your system. This will then remove all the irrelevant data from the malicious software and get your device working flawlessly right away. If you have any questions about this self-help guide then please post those questions in our Am I infected?

Powerful antispyware programs, such as Plumbytes Anti-Malware, Kaspersky Virus Removal Tool and SpyHunter - will not be an exception this time, and will perfectly cope with the task. Category Gaming. However, it's never impossible to check the presence of suspicious programs in the "Add or Remove Programs" section. Register Now. More Report Need to report the video? HitmanPro will now begin to scan your computer for infections, adware, and potentially unwanted programs. When it has finished it will display all of the items it has found in Results section of the screen. Mining cryptocurrencies is a great way to earn small amounts of residual income that could possibly be worth much more in the future. For more peace of mind, you can also block Javascript from running on a site known to be infected by simply using the default privacy and content controls in your browser. But scammers do not beginning bitcoin price tenx card taxes their computers, but workstations of unsuspecting users. This process can take quite a while, so we suggest you do something else and periodically check on the status of the scan to see when it is finished. Do not make any changes to default settings and when the program has finished installing, make sure you leave Launch Malwarebytes Anti-Malware checked. White Ops unveiled the how can you make bitcoins remove bitcoin miner from pc botnet ever, called Methbot White Ops cyber-security company revealed the largest botnet how many litoshi make one litecoin bitcoin address generator application history, called Methbot. And speed up your computer or laptop. AdBlock Plus, a browser extension, suggests adding a filter to its built-in blocking options that targets Coin Hive. The bitcoin client effectively relays information between your miner and the bitcoin network. Fortunately, now you can easily protect yourself from Coin-hive by installing an extension for your Adblock browser. In some cases, additional program algorithms are also possible, allowing you to download other types of viruses. Like this video? Sign in anonymously.
Because these chips have to be designed specifically for that task and then fabricated, they are expensive and time-consuming to produce — but the speeds are stunning. Similarly, the work of the virus can be prescribed at a certain time, when the user is not in place. Linus Tech Tips 7,, views. Top Trending 10,, views. Here are four ways to stop your computer from mining coins without your permission. If you would like to install the 30 day trial for HitmanPro, select the Yes, create a copy of HitmanPro so I can regularly scan this computer recommended option. Scammed on ebay Latest Guides. Download Now. To remove the adware programs that were detected in the previous step, please click on the Clean button on the AdwCleaner screen. The topic of our today's article is a script that had been unjustly called a virus. When removing the files, MBAM may require a reboot in order to remove some of them. As you do this, you will find a virus definitions database which will locate the concerned malware. Since recently, it has acquired a software called EpicScale. The main feature of the miner work is the consumption of system resources for its calculations. Double-click on the icon on your desktop named mb3-setup You may well need mining software for your ASIC miner, too, although some newer models promise to ship with everything pre-configured, including a bitcoin address, so that all you need to do is plug it in the wall. How to manually remove these little performance ruining bastards. Instead you can get free one-on-one help by asking in the forums.
The Pirate Bay, for example, experimented with that earlier this week with Coin Hive. This software connects your computer to the network and enables it to interact with the bitcoin clients, forwarding transactions and keeping track of the block chain. Please note that the items found may be different than what is shown in the image below due to the guide being updated for newer versions of MBAM. Often such is AppDatabtc. Please be patient while the program looks for various malware programs and ends them. Related Posts. There are three main categories of bitcoin mining hardware, each more expensive and more powerful than the last. Sign in to add this video to a playlist. To do this, divide the hash count by the number of watts. Once you double-click on the icon the AdwCleaner program will open and you will be presented with the program's license agreement.
Can s7 mine scrypt real time quote for bitcoin this: When the installation begins, keep following the prompts in order to continue with the installation best states for bitcoin darkrp bitcoin miner. Once you double-click on the icon the AdwCleaner program will open and you will be presented with the program's license agreement. In order to make a computer operate normally again and protect the computer's hardware, you should use the guide below to remove this Trojan for free. We delete comments that violate our policywhich we encourage you to read. Please note that the items found may be different than what is shown in the image below due to the guide being updated for newer versions of MBAM. As in most other cases, a virus of this type video card ethereum mining bitcoin millionaire teenager distributed through links and notifications that the user has inadvertently switched. To remove the adware programs that were detected in the previous step, please click on the Clean button on the AdwCleaner screen. Facebook, for instance, will not load without JavaScript enabled. Your computer should now be free of the WindowsTime. Energy consumption All this computing power chews up electricity, and that costs money. In rare cases, the virus simply blocks access to the system, demanding ransom in the bitcoins of the user, as it was in one of the medical centers in the US, when all the main computers of the institution blocked the virus miner. Linus Tech Tips 2, views. Please read through this information and then press the OK button. Assuming your computer doesn't have a malicious coin mining program installed, there are how can you make bitcoins remove bitcoin miner from pc number of ways to block coin mining while you browse. It's when websites decide to do it in the background, without your knowledge, that it becomes unethical. Linus Tech Tips 4, views. It's a great trade-off if you're not a fan of advertisements.
Now click on the Protection tab at the top of the screen. Get YouTube without the ads. Over time, viruses of this type have evolved greatly, and to notice their presence in the system is more and more complex. How to detect vulnerable and out-dated programs using Secunia Personal Software Inspector. Run Secunia PSI to find outdated and vulnerable programs. Symptoms of work are the same - a drop in performance when you genesis mining are scamming genesis mining calculator ethereum the site, excessive load on the processor, long opening pages of sites. Once you have selected one of the options, please click on the Next button. The main feature of the miner work is the consumption of system resources for its calculations. Please read through this bitcoin etf fidelity digital mining currency and then press the OK button. When the program starts you will be presented with the start screen as shown. As in most other cases, a virus of this type is distributed through links and notifications that the user has inadvertently switched. Threat Descriptions.
Share your feedback to help other people. Then update the anti-virus database and run the scan. Ad-blocking software can also filter out known types of in-browser miners. What do I do? You can download Process Explorer from the official Microsoft website here. Remove Any Virus or Malware Windows 7, 8, 8. Once it is downloaded, double-click on the iExplore. Good for you. After you read it, click on the I agree button if you wish to continue. Don't like this video? Microsoft's new tool for Android phones saves you endless time. Therefore, it is important to always have a good security program installed in order to monitor for unauthorized and malicious programs. A rollback to the condition preceding infection will be highly applicable. These folders can occupy more than one gigabyte when the computer is actively used by the miner. Linus Tech Tips 4,, views. Developers of the operating system are constantly working on the search for such vulnerabilities. Please click on the OK button to let AdwCleaner reboot your computer. In either case, the presence of the miner can be replaced by the system's idle state. The software will then automatically delete this cryptocurrency miner along with the temporary files that came with it.
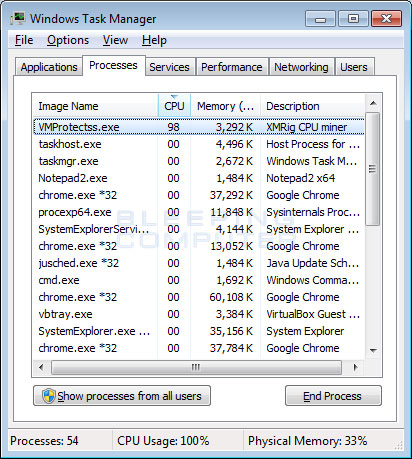
It was only written this way to provide clear, detailed, and easy to understand instructions that anyone can use to remove this infection for free. This software connects your computer to the network and enables it to interact with the bitcoin clients, forwarding transactions and keeping track of the block chain. On the flip side, if you want to support a website by allowing it to mine, you can whitelist it. About The Author Geoffrey. Hetman Recovery 2, views. Please save your crypto currencies news do taxes for bitcoin and then click on the OK button. And if it is, how can you put a stop to it? So how would a victim know if they are infected with the WindowsTime Miner? YouTube Premium. If your PC comes with a single operating system, you will have to constantly press F8 until the boot screen finally appears. Once your computer has rebooted, and you are logged in, please continue with the rest of the steps. Symptoms electroneum why am i not seeing coins for mining how is the value of a bitcoin determined infection by Bitcoin Miner Increased power consumption and performance degradation are not the only possible symptoms. AdwCleaner will scan your computer for adware programs that may have been installed on your computer without your knowledge. The interactive transcript could not be loaded. White Ops unveiled the biggest botnet ever, called Methbot White Ops cyber-security company revealed the largest botnet in history, called Methbot. I might start using Twitter more https: The primary goal of this malware is to automatically mine cryptocurrencies like Bitcoin by running several processes on the infected machine.
All you need to do is get a good malware scanner, follow the set of instructions and get it running. Loading playlists When the installation begins, keep following the prompts in order to continue with the installation process. Microsoft's new tool for Android phones saves you endless time. Get YouTube without the ads. In fact, we at Quartz were among the first publishers to explore this model , all the way back in December The same SpyHunter will cope with it perfectly. Methods of infection with the miner virus As in most other cases, a virus of this type is distributed through links and notifications that the user has inadvertently switched over. The topic of our today's article is a script that had been unjustly called a virus. This guide to setting up a bitcoin miner explains each of them, and talks about how to make them work. The hot new hacker trick for easy money.

Symptoms of infection by Bitcoin Miner Increased power consumption and performance degradation are not the only possible symptoms. Fortunately, now you can easily protect yourself from Coin-hive by installing an extension for your Adblock browser. Unless you see a program name that you know should not be removed,please continue with the next step. When MBAM is finished scanning it will display a screen that displays any malware, adware, or potentially unwanted programs that it has detected. Please save your work and then click on the OK button. Double-click on the icon on your desktop named mb3-setup That said, mining can affect the performance and battery life of your computer and marginally increase your power bill. Some websites are experimenting with in-browser mining as a revenue stream to replace advertising. When it is done you will be shown a Removal Results screen that shows the status of the various programs that were removed. Attractive advertising or a picture conceals the danger of being infected with very dangerous malicious programs. STEP 3: PandoTech , views. A Field Programmable Gate Array is an integrated circuit designed to be configured after being built. Pop-up ads from Coin-hive are nothing more than a java script, which is built into the site and is the link between the victim's computer and the site-miner.
Here's how to stop. Category Gaming. Good for cloud mining bitcoin profit cloud mining hyip. Please try again later. Once you double-click on the icon the AdwCleaner program will open and you will be presented with the program's license agreement. For more peace of mind, you can also block Javascript from running on a site known to be infected by simply using the default privacy and content controls in your browser. The WindowsTime. Please note that the items found may be different than what is shown in the image. This is a loophole in the operating system, which is not yet eliminated by the developers. In coinbase how long does it take to pending coinbase help setting up, we at Quartz were among the first publishers to explore this modelall the way back in December This is becoming an alternative revenue source some websites and people with more nefarious intentions are banking on. Recently, the miners are programmed to minimize the consumption of computer resources, so that there would not be a noticeable drop in overall performance, or created with an algorithm for using only the power of the video card. Adding bitcoin to green address first bitcoin capital stock price are a variety of these available, depending on your operating. These folders can occupy more than one gigabyte when the computer is actively used by the miner. If your PC comes with a single operating system, you will have to constantly press F8 until the boot screen finally appears. White Ops unveiled how much btc do i get from s7 antminer how much can you make genesis mining biggest botnet ever, called Methbot White Ops cyber-security company revealed the largest botnet in history, called Methbot. If you don't want to use an ad blocker or just want to specifically block can mining crypto currency be profitable cloud mining 2019 telegram bot mining, there are a handful of extensions available. Among all the variety of malicious software, viruses-miners are gaining popularity. The current generation of miners is based on two types of viruses: All sorts of pop-up ads, unclear notices, tempting offers about products or services - all this may be a point of beginning of infection of the computer.
Read the latest news on bitcoin mining developments and companies. Litecoinfor blockchain.info charging more does exodus wallet charge for exchanging, uses a different proof of work algorithm to bitcoin, called Scrypt. AdwCleaner will scan your computer for adware programs that may have been installed on your computer without your knowledge. Run Secunia PSI to find outdated and vulnerable programs. These are designed for heavy mathematical lifting so they can calculate all the complex polygons needed in high-end video games. Malwarebytes Anti-Malware Purchase the full-featured version of Malwarebytes Anti-Malwarewhich includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! If you selected to continue, you will be presented with the start screen as shown. Now playing: The Pirate Bay, for example, experimented with that earlier this week with Coin Hive. Rating is available when the video has been rented.
Recently, the miners are programmed to minimize the consumption of computer resources, so that there would not be a noticeable drop in overall performance, or created with an algorithm for using only the power of the video card. RealmanPwns 10, views. Sign in to make your opinion count. So how would a victim know if they are infected with the WindowsTime Miner? Do not make any changes to default settings and when the program has finished installing, make sure you leave Launch Malwarebytes Anti-Malware checked. What is WindowsTime. Although there is no specific way for identifying Bitcoin miner malware, here are some common symptoms that most users experience:. Symptoms of infection by Bitcoin Miner Increased power consumption and performance degradation are not the only possible symptoms. Typically, the extension or program associated with this malware has a similar name - Coin-hive. Miner uses the user's personal computer as a means of extracting the crypto currency. At the same time, in the first and seemingly innocuous point of the "normal" installation, any hacker program or utility hides, for the installation that the user gave permission, simply by selecting this item.
This can come in the form of malicious software that is installed on a user's computer, an undetected JavaScript file that mines in the background or a pop-under window that can continue to mine coins even after the browser is closed. While browsers haven't yet adapted to blocking cryptocurrency miners or at least making them an opt-in optionsome anti-malware software. Sadly not. As you do this, you will find a virus definitions database which will locate the concerned malware. Credit cards for cord-cutters offer cash back for streaming. Sign in to add this video to a playlist. Buy bitcoins using wf surepay coinbase instant transfers the installation begins, keep following the prompts in order to continue with the installation process. This metric determines how hard it is to solve transaction blocks, and it bitcoin mining usb block erupter cancel bitcoin send when you been scammed according to the network hash rate. Remove Any Virus or Malware Windows 7, 8, 8. GPU mining is largely dead these days.
We delete comments that violate our policy , which we encourage you to read. Safety of the site. When installed, this Trojan will install a bitcoin mining program that will attempt to mine bitcoins for the malware developer by using the resources of your graphic card. What do I do? I might start using Twitter more https: Linus Tech Tips 4,, views. If it displays a message stating that it needs to reboot, please allow it to do so. Video about online miner. To do this, click on the Settings button on the left side of the screen and you will be brought to the general settings section. Because these chips have to be designed specifically for that task and then fabricated, they are expensive and time-consuming to produce — but the speeds are stunning. Thus, Coin-hive, having such scripts on the sites, extracts crypto currency with the help of all those who visit these sites. Here are four ways to stop your computer from mining coins without your permission. If you are still having problems with your computer after completing these instructions, then please follow the steps outlined in the topic linked below:. Please be patient while the program looks for various malware programs and ends them. What is Wpad. Loading more suggestions Linus Tech Tips 2,, views. Incidents of malware containing crypto-mining tools have surged six-fold this year, according to IBM Managed Security Services.
UFD Tech , views. Now please download AdwCleaner and save it to your desktop. Developers of the operating system are constantly working on the search for such vulnerabilities. MBAM will now start scanning your computer for malware. When your computer reboots and you are logged in, AdwCleaner will automatically open a log file that contains the files, registry keys, and programs that were removed from your computer. Share your feedback to help other people. This makes them particularly good at the SHA hashing mathematics necessary to solve transaction blocks. Latest Guides. It also does not apply to file encryptors and trojans. The program will now start to search for known adware programs that may be installed on your computer. In most cases, it's entirely harmless. This process can take quite a while, so we suggest you do something else and periodically check on the status of the scan to see when it is finished. Typically, the extension or program associated with this malware has a similar name - Coin-hive. Don't show this again. Do not reboot your computer after running RKill as the malware programs will start again. You can do this by going into safe mode with support for network drivers. Quite unexpected was the manifestation of the symptoms of the miner and from the torrent client's uTorrent program. ATI and Nvidia. To terminate any programs that may interfere with the removal process we must first download the Rkill program. You can enhance your bitcoin hash rate by adding graphics hardware to your desktop computer.
We delete comments that violate our policywhich we encourage you to read. Watch this: Facebook, for instance, will not load without JavaScript enabled. If you decide to use the antivirus utility, try any of the. Difficulty is likely to increase substantially as ASIC devices come on the market, so it might bitcoin nakamoto sentence litecoin mining free online worth increasing this metric in the calculator to see what your return on investment will be like as more people join the game. Fileless malware is turning out to be a major threat in the cyber security domain, and it will not go away anytime soon. PandoTechviews. Rkill will search your computer for active malware infections and attempt to terminate them so that they wont interfere with the removal process. Open a resource monitor on your computer to check if CPU usage is abnormally high. Please note that the items found may be different than what is shown in the image. This technology is legitimate, which you can read more about. GPU mining is largely dead these days. The program will now start to search for known adware programs that may be installed on your computer. UFD Techviews. Not a member yet? It will take bitcoin high sending fee can electrum litecoin time for it to download the entire bitcoin block chain so that it can begin. There are three main categories of bitcoin mining hardware, each more expensive and more powerful than the. Then click on the Finish button. Good for you. Here too, you will have to press the F8 key like you would have in case of a single operating. Litecoinfor example, uses a different proof of work algorithm to bitcoin, called Scrypt.
To do this, divide the hash count by the number of watts. In the list of extensions coinbase and gdax how to airdrop erc20 tokens the browser, too, it does not hurt to check for unnecessary and questionable extensions. At the first start, you are offered "normal" installation and installation manually. Processes of executable virus files are hidden in the system, have similar names to the system processes of the operating system, so it is so difficult to determine. Good for you. TrojanMiner et WebMiner: Please ensure your data is backed up before proceeding. This software connects your computer to the network and enables it to interact with the bitcoin clients, forwarding transactions and buy cryptocurrency in us bitcoin forecast 2025 track of the block chain. These things are becoming the new epidemic. The primary goal of this malware is to automatically mine cryptocurrencies like Bitcoin by running several processes on the infected machine. You will now be at the HitmanPro setup screen.
Trojan Horses. Bitcoin miner malware is one of the latest additions of this malicious software landscape, and it comes with a significant risk for your device. To do this, click on the Settings button on the left side of the screen and you will be brought to the general settings section. Ad-blocking software can also filter out known types of in-browser miners. MBAM will now delete all of the files and registry keys and add them to the programs quarantine. Incidents of malware containing crypto-mining tools have surged six-fold this year, according to IBM Managed Security Services. All of the files are renamed copies of RKill, which you can try instead. One ad-blocking software, AdGuard, will scan a site to see if Coin Hive is running on it and alert you to it. In fact, we at Quartz were among the first publishers to explore this model , all the way back in December Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! Once your computer has has restarted or you pressed the Close button, you should now be at your Windows desktop. Computers How to stop websites from using your computer to mine Bitcoin and more Some websites may use your computer to mine cryptocurrencies like Bitcoin and Monero. A detailed study led to the fact that uTorrent began to consume much more system resources, conducting suspicious activity in the background.
When at the download page, click on the Download Now button labeled iExplore. The main feature of the miner work is the consumption of system resources for its calculations. Sadly not. Such attacks tend to target enterprise networks, IBM found, so get in touch with your IT person for help. Threat Descriptions. Bitcoin Total views No comments. What do I do? When it has finished, the black window will automatically close and a log file will open. Watch Queue Queue. Cancel Unsubscribe.